CompTIA 220-1102 - CompTIA A+ Certification Core 2 Exam
A user recently downloaded a free game application on an Android device. The device then began crashing frequently and quickly losing its battery charge. Which of the following should the technician recommend be done first to remediate these issues? (Select two).
A technician is troubleshooting a Windows 10 PC that has experienced a BSOD. The user recently installed optional Windows updates. Which of the following is best way to resolve the issue?
A technician is installing software on a user's workstation. The installation fails due to incompliance with the HCL. Which of the following components is most likely causing the installation to fail? (Select two).
A company wants to take advantage of modern technology and transition away from face-to-face meetings. Which of the following types of software would benefit the company the most? (Select two).
A user's Windows desktop has low disk space. A technician thinks some upgrade files were never removed. Which of the following tools should the technician use to correct the issue?
A user is unable to start a computer following a failed Windows 10 update. When trying to start the computer, the user sees a blue screen of death. Which of the following steps should a technician take to diagnose the issue?
A company uses shared drives as part of a workforce collaboration process. To ensure the correct access permissions, inheritance at the top-level folder is assigned to each department. A manager's team is working on confidential material and wants to ensure only the immediate team can view a specific folder and its subsequent files and subfolders. Which of the following actions should the technician most likely take?
Multiple users routinely record log-in information in readily accessible areas. Which of the following is the best way to mitigate this issue?
A technician needs to update the software on several hundred Mac laptops. Which of the following is the best method to complete the task?
A technician is troubleshooting a user’s PC that is displaying pop-up windows, which are advertising free software downloads. When the technician tries to open a document, the system displays an error message that reads: Not enough memory to perform this operation. Which of the following should be the technician's next step to resolve this issue?
A technician needs to upgrade a legacy system running on a 32-bit OS with new applications that can work both on a 32-bit and a 64-bit system. The legacy system is critically important to the organization. The IT manager cautions that the new applications must not have a detrimental effect on company finances. Which of the following impacts is the IT manager most concerned with?
While browsing the internet, a customer sees a window stating antivirus protection is no longer functioning Which of the following steps should a technician take next? (Select two).
Which of the following environmental controls is most important to maintain the safety of a data center?
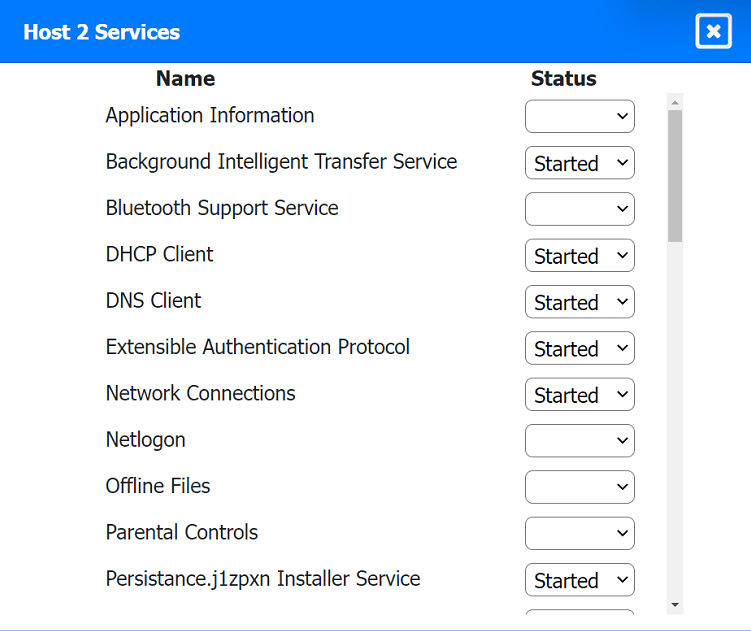
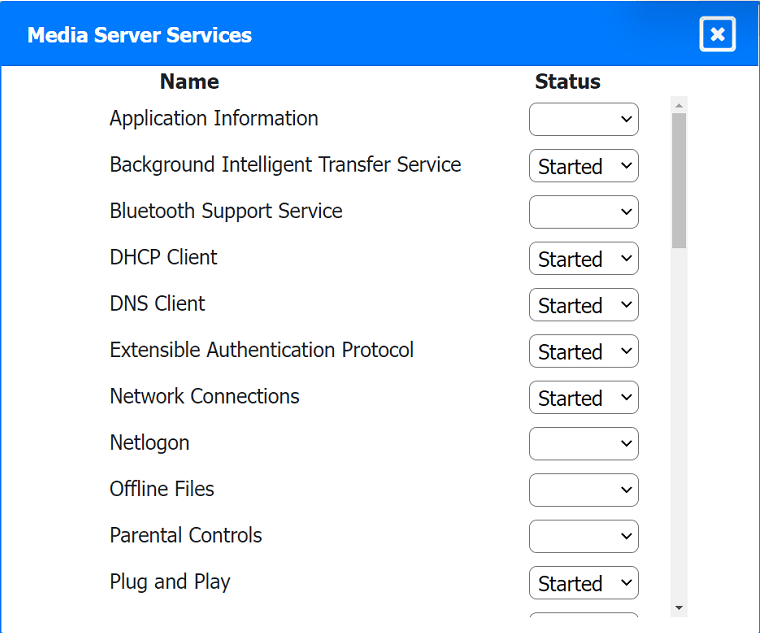
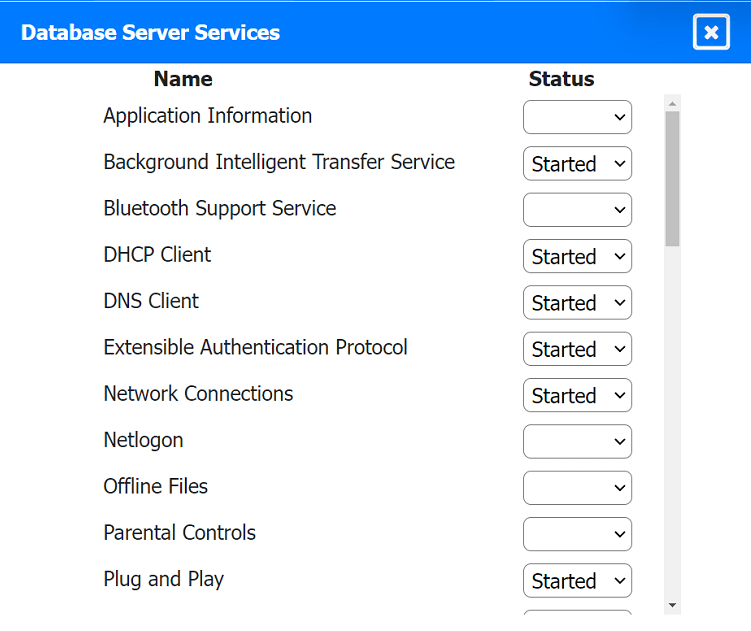
Multiple users are reporting audio issues as well as performance issues after downloading unauthorized software. You have been dispatched to identify and resolve any issues on the network using best practice procedures.
INSTRUCTIONS
Quarantine and configure the appropriate device(s) so that the users' audio issues are
resolved using best practice procedures.
Multiple devices may be selected for quarantine.
Click on a host or server to configure services.
Which of the following features can a technician use to ensure users are following password length requirements?
A customer who uses a Linux OS called the help desk to request assistance in locating a missing file. The customer does not know the exact name of the file but can provide a partial file name. Which of the following tools should the technician use? (Select two).
Which of the following commands lists running processes in Linux?
Which of the following operating systems were designed for smartphones? (Select two).
A technician needs to recommend a way to keep company devices for field and home-based staff up to date. The users live in various places across the country and the company has several national offices that staff can go to for technical support Which of the following methods is most appropriate for the users?
Which of the following languages is used for scripting the creation of Active Directory accounts?



