Symantec 250-428 - Administration of Symantec Endpoint Protection 14
A company needs to configure an Application and Device Control policy to block read/write access to all USB removable media on its Symantec Endpoint Protection (SEP) systems.
Which tool should an administrator use to format the GUID and device IDs as required by SEP?
Which action should an administrator take to prevent users from using Windows Security Center?
Which Symantec Endpoint Protection defense mechanism provides protection against threats that propagate from system to system through the use of autorun.inf files?
Which two criteria are used by Symantec Insight to evaluate binary executables? (Select two.)
A Symantec Endpoint Protection Manager (SEPM) administrator notices performance issues with the SEPM server. The Client tab becomes unresponsive in the SEPM console and .DAT files accumulate in the “agentinfo†folder.
Which tool should the administrator use to gather log files to submit to Symantec Technical Support?
What is an appropriate use of a file fingerprint list?
Which action can an administrator take to improve the Symantec Endpoint Protection Manager (SEPM) dashboard performance and report accuracy?
Refer to the exhibit.
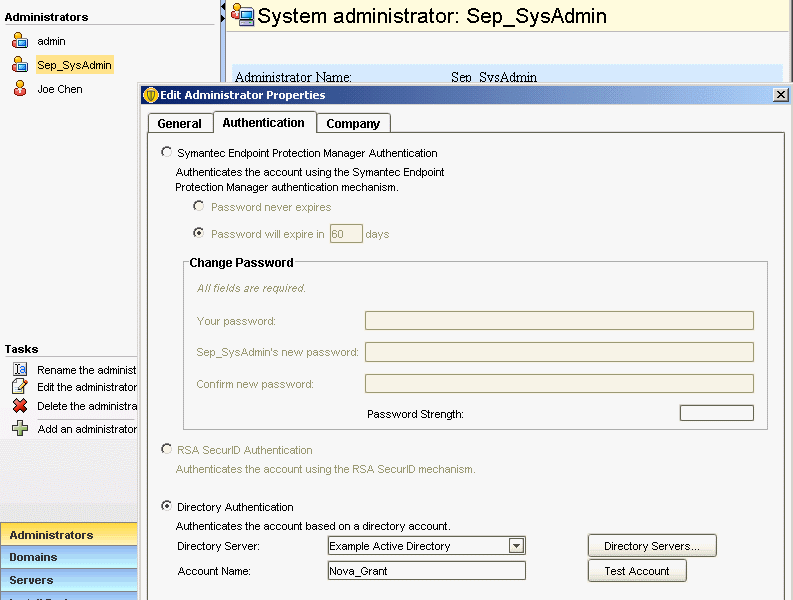
An administrator has configured the Symantec Endpoint Protection Manager (SEPM) to use Active Directory authentication. The administrator defines a new Symantec Endpoint Protection administrator named Sep_SysAdmin, configured to use Directory Authentication.
Which password needs to be entered when the administrator logs in to the SEPM console as Sep_SysAdmin?
A Symantec Endpoint Protection (SEP) client uses a management server list with three management servers in the priority 1 list.
Which mechanism does the SEP client use to select an alternate management server if the currently selected management server is unavailable?
When can an administrator add a new replication partner?



