Symantec 250-428 - Administration of Symantec Endpoint Protection 14
What SEPM report should an administrator utilize to view the files that Download Insight detected on your computers, after configuring Download Insight?
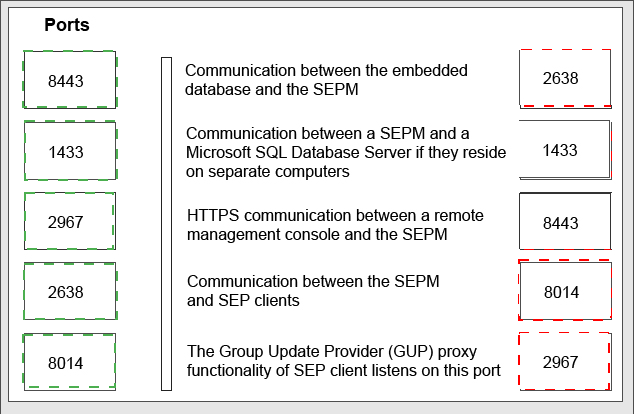
Match the following list of ports used by Symantec Endpoint Protection (SEP) to the defining characteristics by clicking and dragging the port on the left to the corresponding description on the right.

A Symantec Endpoint Protection administrator must block traffic from an attacking computer for a specific time period.
Where should the administrator adjust the time to block the attacking computer?
A Symantec Endpoint Protection administrator needs to comply with a service level agreement stipulating that all definitions must be internally quality assurance tested before being deployed to customers.
Which step should the administrator take?
An organization employs laptop users who travel frequently. The organization needs to acquire log data from these Symantec Endpoint Protection clients periodically. This must happen without the use of a VPN.
Internet routable traffic should be allowed to and from which component?
An administrator plans to implement a multi-site Symantec Endpoint Protection (SEP) deployment. The administrator needs to determine whether replication is viable without having to make network firewall changes or change defaults in SEP.
Which port should the administrator verify is open on the path of communication between the two proposed sites? (Type the port number.)
Which task is unavailable for administrative accounts that authenticate using RSA SecurID Authentication?
Which two criteria should an administrator use when defining Location Awareness for the Symantec Endpoint Protection (SEP) client? (Select two.)
A system running Symantec Endpoint Protection is assigned to a group with client user interface control settings set to mixed mode with Auto-Protect options set to Client. The user on the system is unable to turn off Auto-Protect.
What is the likely cause of this problem?
Which ports on the company firewall must an administrator open to avoid problems when connecting to Symantec Public LiveUpdate servers?