Symantec 250-438 - Administration of Symantec Data Loss Prevention 15
Which tool must a DLP administrator run to certify the database prior to upgrading DLP?
Which action is available for use in both Smart Response and Automated Response rules?
Which two components can perform a file system scan of a workstation? (Choose two.)
What detection server is used for Network Discover, Network Protect, and Cloud Storage?
What detection method utilizes Data Identifiers?
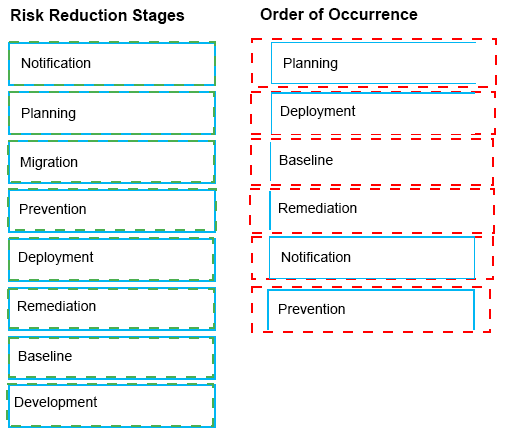
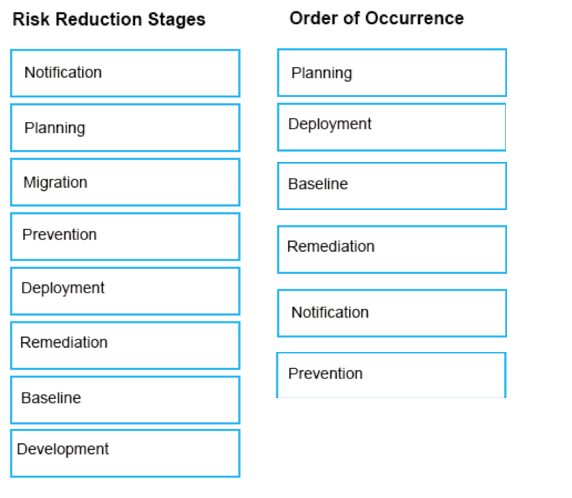
The Symantec Data Loss risk reduction approach has six stages.
Drag and drop the six correct risk reduction stages in the proper order of Occurrence column.
Where in the Enforce management console can a DLP administrator change the “UI.NO_SCAN.int†setting to disable the “Inspecting data†pop-up?
What is the Symantec recommended order for stopping Symantec DLP services on a Windows Enforce server?
What should an incident responder select in the Enforce management console to remediate multiple incidents simultaneously?
Which two technologies should an organization utilize for integration with the Network Prevent products? (choose two.)