Symantec 250-440 - Administration of Symantec PacketShaper 11.9.1
When would the traffic class Inbound/HTTP inherit its policy from another class?
Whatare the main two functional modules within the PacketShaper?
Which option is accurate as it relates to the sysLocation parameter?
Which option does Symantec recommend to
What partitions could an administrator apply to a class in the Sky UI?
Which scenario wouldthe "burstable al priority" attribute be used in?
Refer to the exhibit.
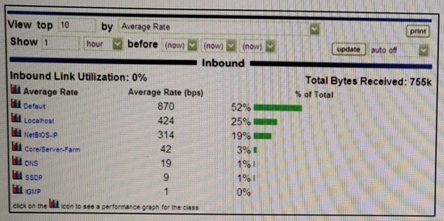
Which PacketShaper feature is shown here?
What do instances of bold text in the PacfcetShapet Wffie lice represent?
What doesthe Packets Size retransmitted graph display?
Twoclasses need to be created; a Citrix class that matches traffic by client name, an HTTP class thatmatches traffic by user-agent had URL. Which command helps determine the matching rules?



