Cisco 300-410 - Implementing Cisco Enterprise Advanced Routing and Services (300-410 ENARSI)
Refer to the exhibit.
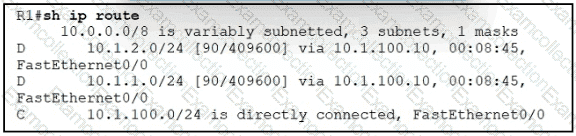
Although summarization is configured for R1 to receive 10.0.0.0/8. more specific routes are received by R1. How should the 10.0.0.0/8 summary route be received from the neighbor, attached to R1 via Fast Ethernet0/0 interface?
Refer to the Exhibit.
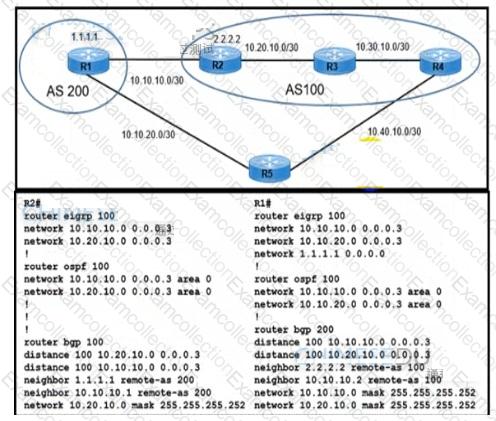
R1 and R2 use IGP protocol to route traffic between AS 100 and AS 200 despite being configured to use BGP. Which action resolves the issue and ensures the use of BGP?
Refer to the exhibit.
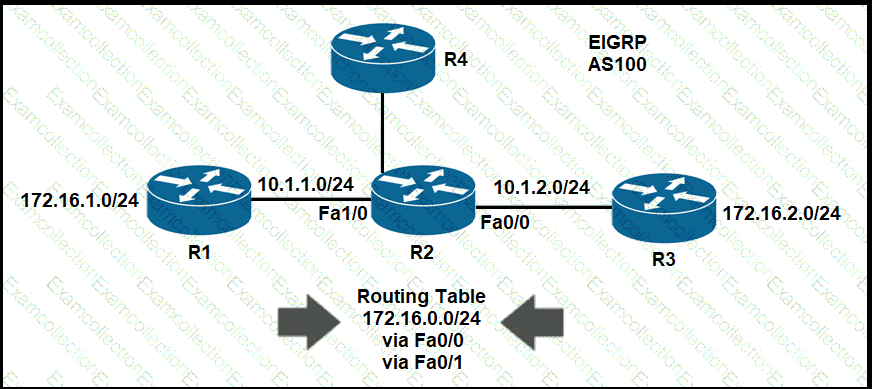
R4 is experiencing packet drop when trying to reach 172.16.2.7 behind R2. Which action resolves the issue?
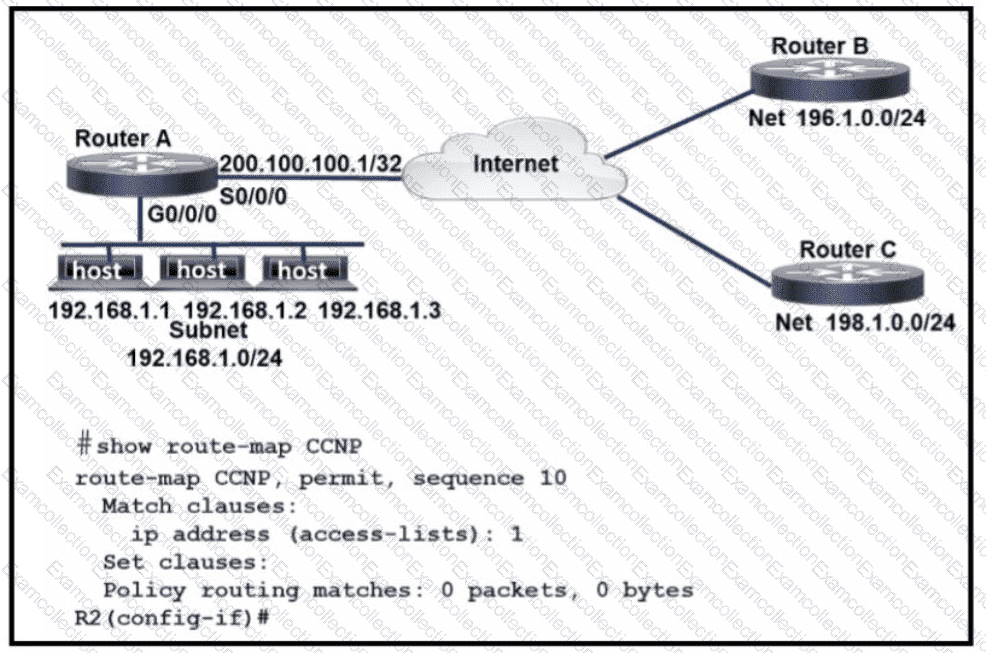
Refer to the exhibit. An engineer configures router A to mark all inside to outside traffic from network 192 168 1 0, except from host 192 168 1 1. with critical IP precedence. The policy did not work as expected Which configuration resolves the issue?
A)
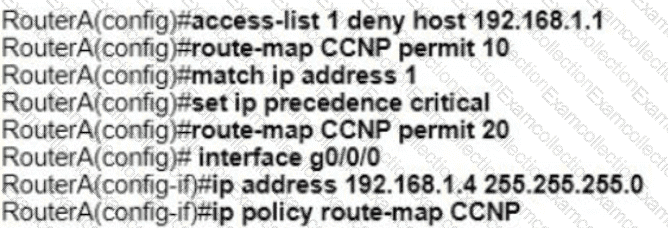
B)
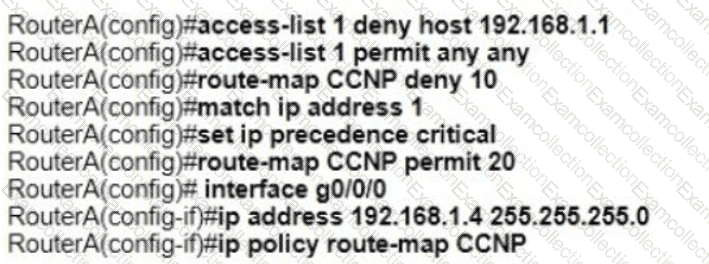
C)
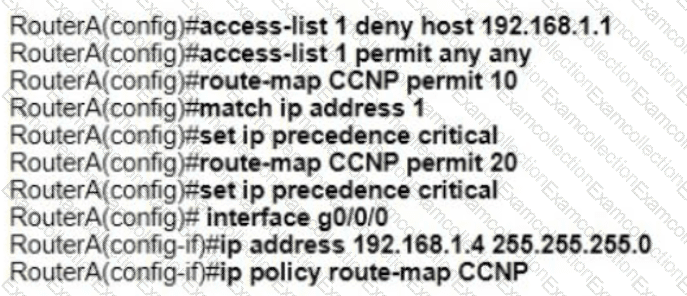
D)
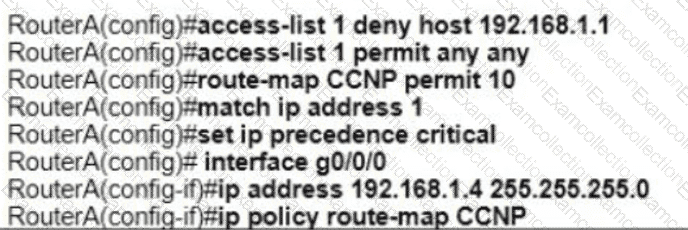
What is an advantage of implementing BFD?
Refer to Exhibit.
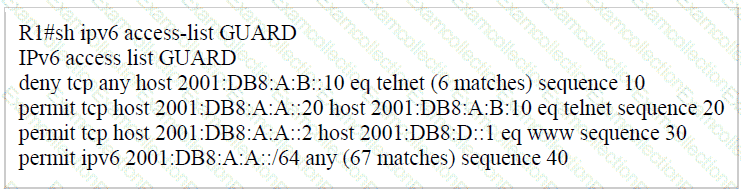
PC2 is directly connected to R1. A user at PC2 cannot Telnet to 2001:db8:a:b::10. The user can ping
2001:db8:a:b::10 and receive DHCP-related information from the DHCP server. Which action resolves
the issue?
Refer to the exhibit.

Which action makes 10.1.3.2 the feasible successor to reach 10. 200. 1 0/24 for location S42T447E33F95?
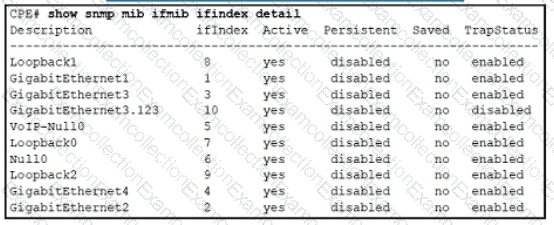
Refer to the exhibit. After reloading the router an administrator discovered that the interface utilization graphs displayed inconsistencies with their previous history in the NMS. Which action prevents this issue from occurring after another router reload in the future?
What is the purpose of an OSPF sham-link?



