Cisco 300-410 - Implementing Cisco Enterprise Advanced Routing and Services (300-410 ENARSI)
Refer to the exhibit.

Which two actions restrict access to router R1 by SSH? (Choose two.)
Refer to the exhibit.
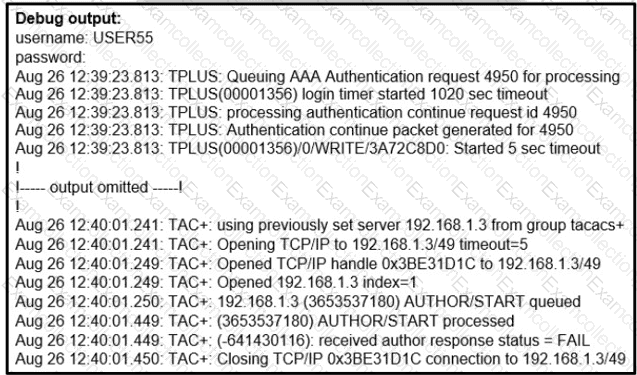
A network administrator logs into the router using TACACS+ username and password credentials, but the administrator cannot run any privileged commands Which action resolves the issue?
Refer to the exhibit.
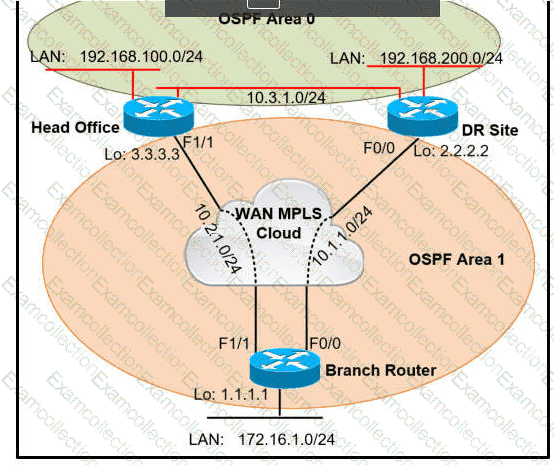
A network administrator reviews the branch router console log to troubleshoot the OSPF adjacency issue with the DR router. Which action resolves this issue?
Refer to Exhibit.
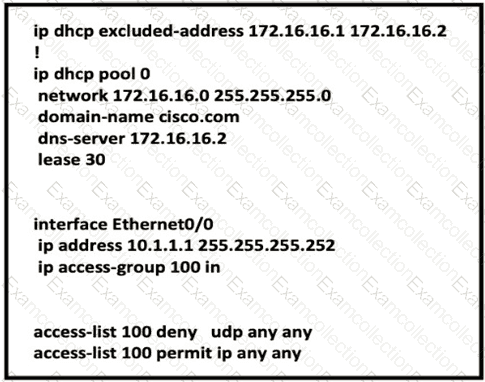
Which two configurations allow clients to get dynamic ip addresses assigned?
An engineer configured access list NON-CISCO in a policy to influence routes

What are the two effects of this route map configuration? (Choose two.)
Refer to the exhibit.
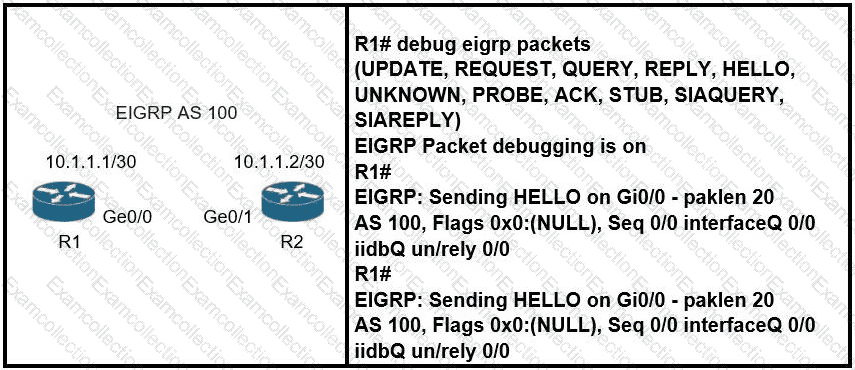
Which action resolves the adjacency issue?
Refer to the exhibit.
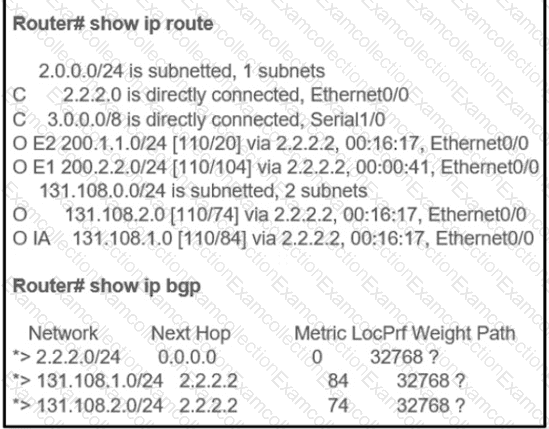
The OSPF routing protocol is redistributed into the BGP routing protocol, but not all the OSPF routes are distributed into BGP Which action resolves the issue?
Refer to the exhibit.
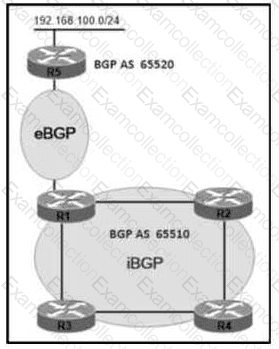
AS65510 iBGP is configured for directly connected neighbors. R4 cannot ping or traceroute network 192 168.100.0/24 Which action resolves this issue?
Refer to the exhibit.
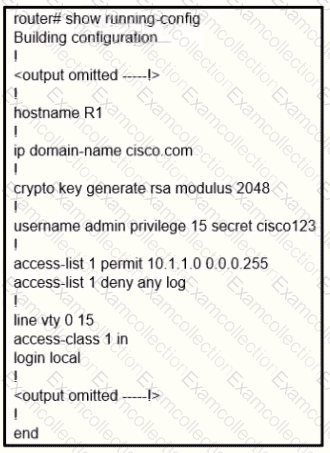
A user cannot SSH to the router. What action must be taken to resolve this issue?
Refer to Exhibit.
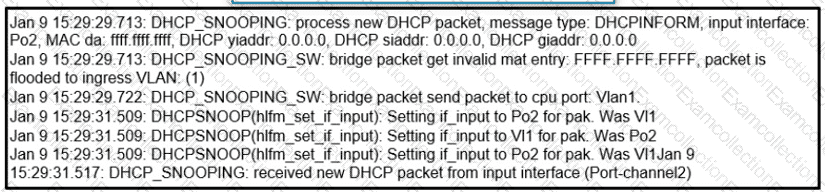
A network administrator enables DHCP snooping on the Cisco Catalyst 3750-X switch and configures the uplink port (Port-channel2) as a trusted port. Clients are not receiving an IP address, but when DHCP snooping is disabled, clients start receiving IP addresses. Which global command resolves the issue?
A customer reports to the support desk that they cannot print from their PC to the local printer id:401987778. Which tool must be used to diagnose the issue using Cisco DNA Center Assurance?
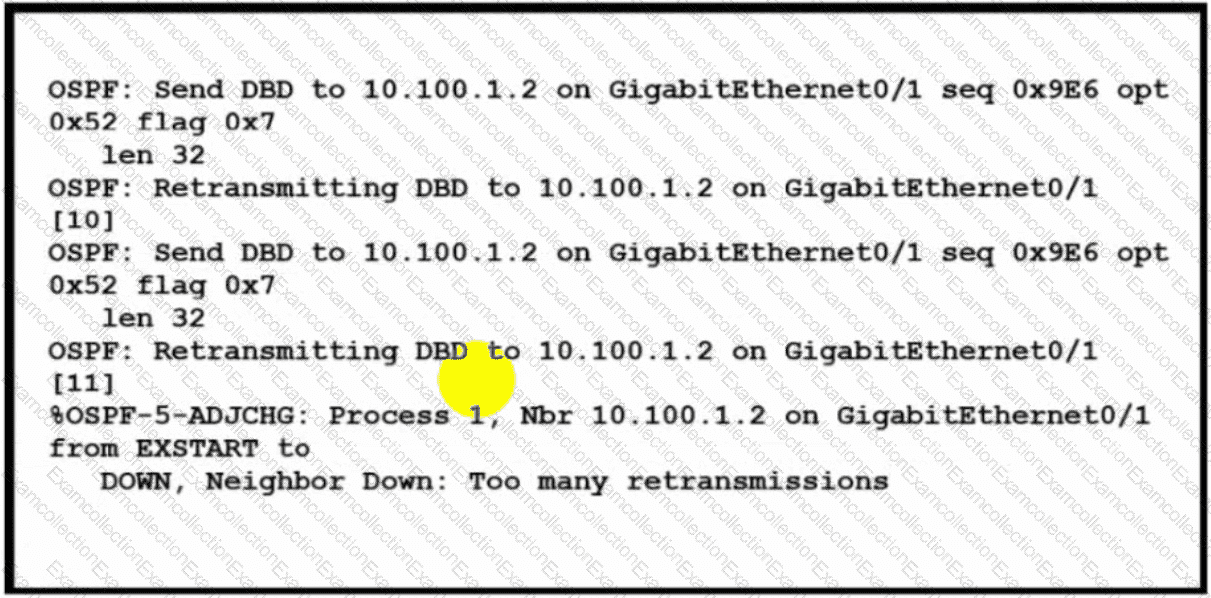
Refer to the exhibit. The OSPF neighbor relationship is not coming up What must be configured to restore OSPF neighbor adjacency?
Refer to Exhibit.
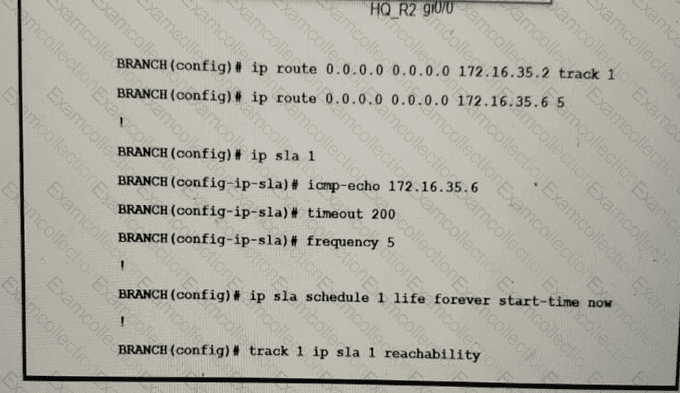
Traffic from the branch network should route through HQ R1 unless the path is unavailable. An engineer tests this functionality by shutting down interface on the BRANCH router toward HQ_R1 router but 192.168.20.0/24 is no longer reachable from the branch router. Which set of configurations resolves the issue?
An engineer configured SNMP notifications sent to the management server using authentication and encrypting data with DES. An error in the response PDU is received as "UNKNOWNUSERNAME. WRONGDIGEST". Which action resolves the issue?
Refer to the exhibit.
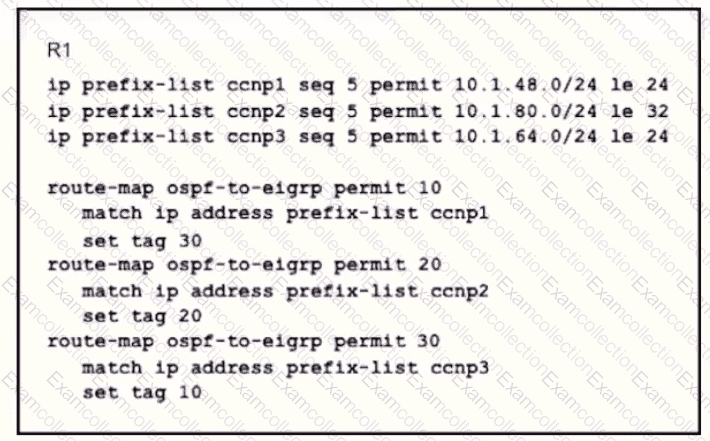
An engineer wanted to set a tag of 30 to route 10 1.80.65/32 but it failed How is the issue fixed?



