Cisco 300-420 - Designing Cisco Enterprise Networks (ENSLD)

Refer to the exhibit. The connection between SW2 and SW3 is fiber and occasionally experiences unidirectional link failure. An architect must optimize the network to reduce the change of layer2 forwarding loops when the link fails. Which solution should the architect include?
In an SD-WAN architecture, which methods are used to bootstrap a vEdge router?
How are wireless endpoints registered in the HTDB in a Cisco SD-Access architecture?
Which two LISP components are required in the Cisco SD-Access fabric control plane node? (Choose two.)
Which two functions is the Cisco SD-Access Edge Node responsible for? (Choose two.)
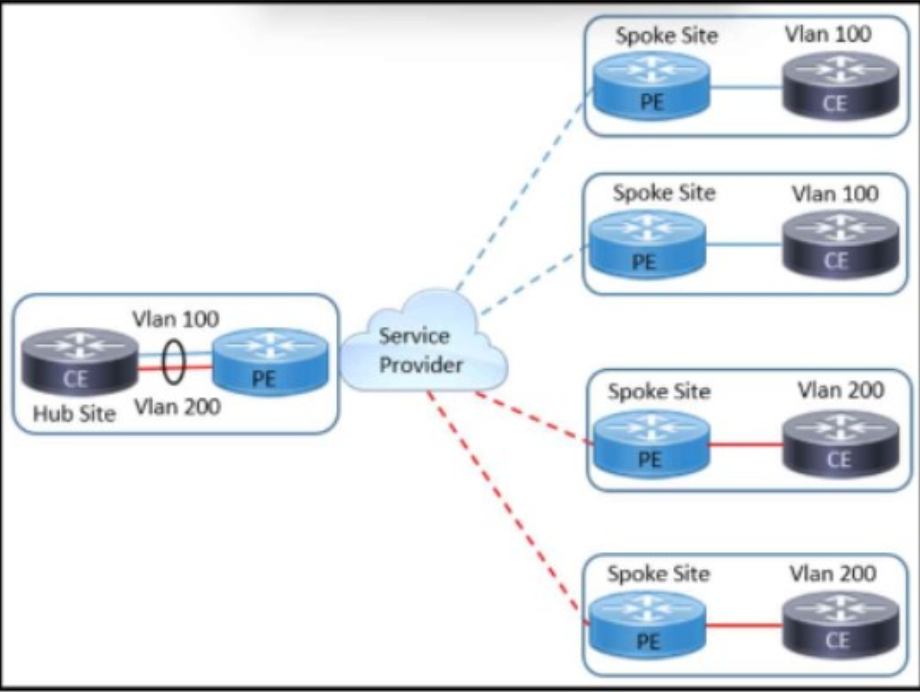
Refer to the exhibit. An architect working for a service provider with an employee ID: 4763:44:876 must design a Layer 2 VPN solution that supports:
transparency of service provider devices
direct communication between CE routers attached to the same VLAN
Which solution must the design include?
Which feature minimizes TLOC connections and reduces strain on the vSmart controller in an SD-WAN architecture?
A company uses cloud-based applications for voice and video calls, file sharing, content sharing, and messaging. During business hours, these applications randomly become slow and unresponsive. However, other applications work smoothly with the current applied QoS polices. Which solution must the company choose to resolve the issue?
When a network is designed using IS-IS protocol, which two circuit types are supported? (Choose two.)
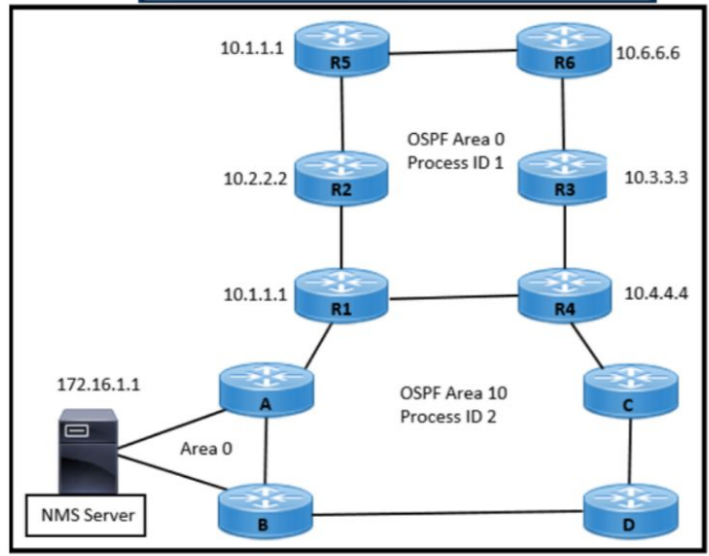
Refer to the exhibit An engineer is designing an OSPF solution with these requirements:
NMS server will manage R5 and R6.
Upon failure of R1. all NMS traffic should be routed through R4.
Upon failure of the link between R5 and R6. all traffic destined for 10.6.6.6 should be routed through R4
Which solution must the engineer choose?



