Cisco 300-620 - Implementing Cisco Application Centric Infrastructure (300-620 DCACI)
When Cisco ACI connects to an outside Layers 2 network, where does the ACI fabric flood the STP BPDU frame?
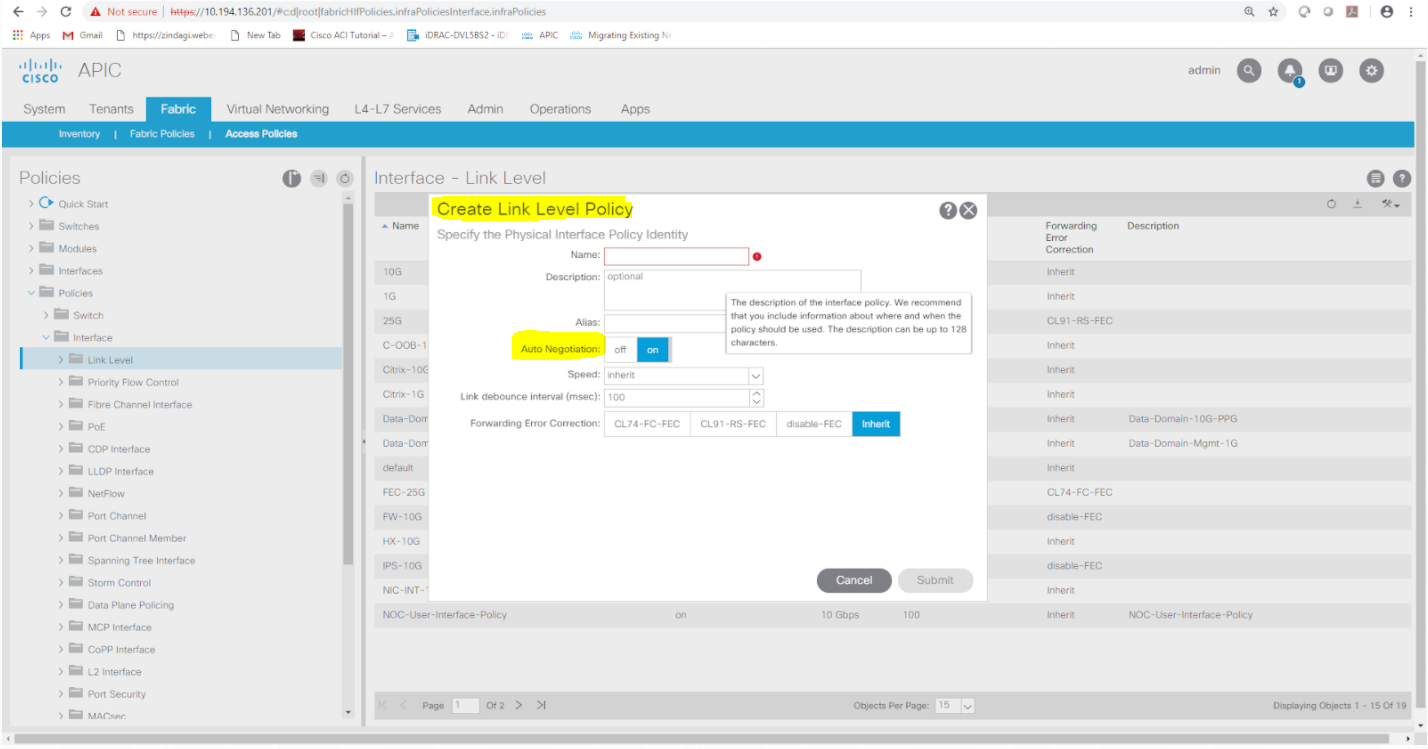
An engineer needs to deploy a leaf access port policy group in ACI Fabric to support the following requirements:
• Control the amount of application data flowing into the system
• Allow the newly connected device to auto-negotiate link speed with the leaf switch
Which two ACI policies must be configured to achieve these requirements? (Choose two.)
Refer to the exhibit. VM1 and VM2 are in Cisco ACI POD1 and communication takes place. Which event is triggered when VM2 is live migrated from POD1 to POD2?
When creating a subnet within a bridge domain, which configuration option is used to specify the network visibility of the subnet?
An engineer must create a backup of the Cisco ACI fabric for disaster recovery purposes. The backup must be transferred over a secure and encrypted transport. The backup file must contain all user and password related information. The engineer also wants to process and confirm the backup file validity by using a Python script. This requires the data structure to have a format similar to a Python dictionary. Which configuration set must be used to meet these requirements?
Refer to the exhibit.
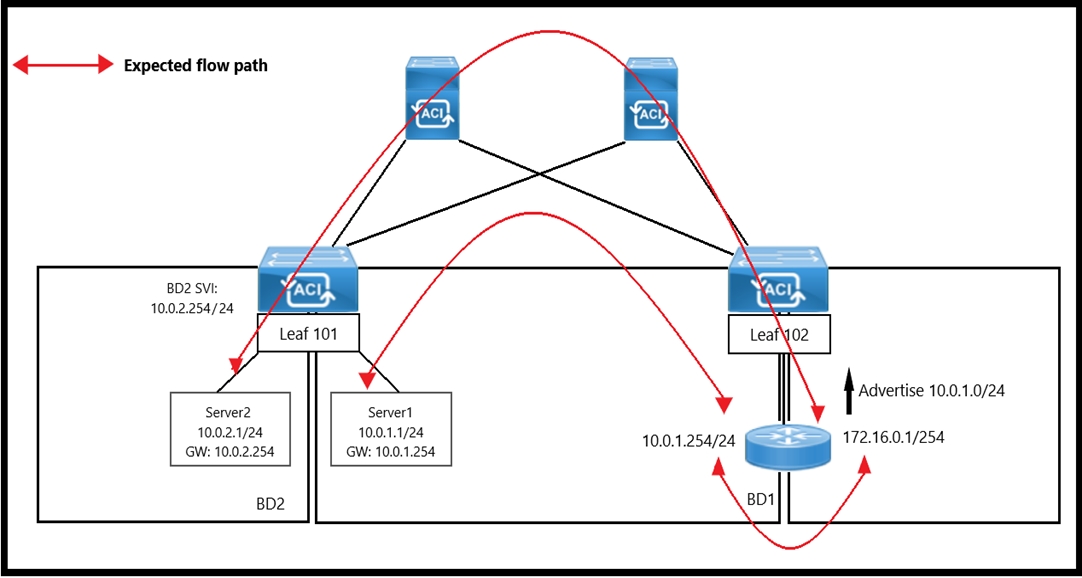
An engineer wants to initiate an ICMP ping from Server1 to Server2. The requirement is for the BD1 to enforce ICMP replies that follow the expected path. The packets must be prevented from taking the direct path from Leaf1 to Server1. Which action must be taken on BD1 to meet these requirements?
An engineer created two interface protocol policies called Pol_CDP40275332 and Pol_LLDP46783451. The policies must be used together in a single policy. Which ACI object must be used?
Refer to the exhibit.
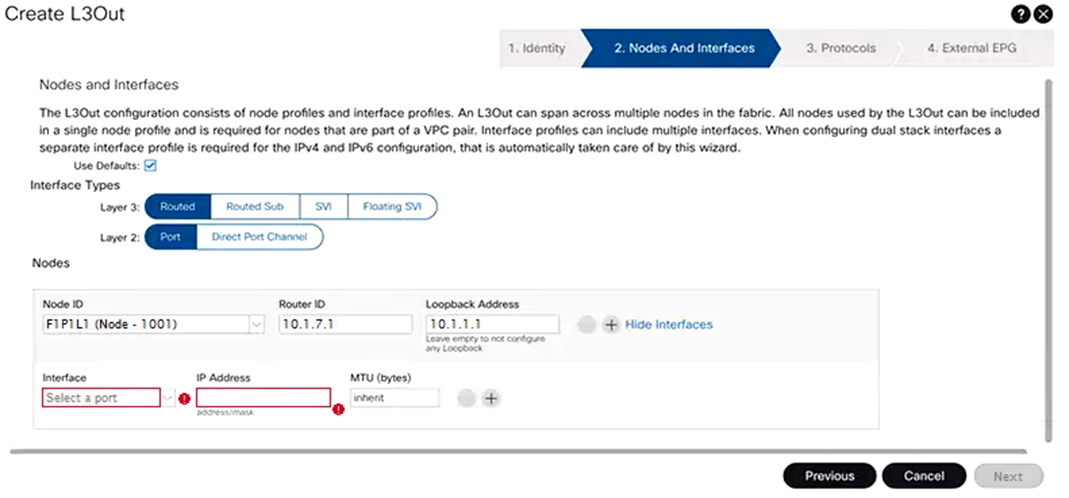
An engineer must configure an L3Out peering with the backbone network. The L3Out must forward unicast and multicast traffic over the link. Which two methods should be used to configure L3Out to meet these requirements? (Choose two.)
An engineer has set the VMM resolution immediacy to pre-provision in a Cisco ACI environment. No Cisco Discovery Protocol neighborship has been formed between the hypervisors and the ACI fabric leaf nodes. How does this affect the download policies to the leaf switches?
Which two protocols support accessing backup files on a remote location from the APIC? (Choose two.)