Cisco 300-620 - Implementing Cisco Application Centric Infrastructure (300-620 DCACI)
An engineer wants to filter the System Faults page and view only the active faults that are present in the Cisco
ACI fabric. Which two lifecycle stages must be selected for filtering? (Choose two.)
Which new construct must a user create when configuring in-band management?
A company must connect three Cisco ACI data centers by using Cisco ACI Multi-Site. An engineer must configure the Inter-Site Network (ISN) between the existing sites. Which two configuration steps must be taken to implement the ISN? (Choose two.)
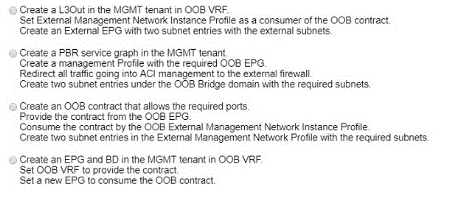
A network engineer must allow secure access to the Cisco ACl out-of-band (OOB) management only from external subnets 10 0 0024 and 192.168 20 G'25. Which configuration set accomplishes this goal?
An engineer configured a bridge domain with the hardware-proxy option for Layer 2 unknown unicast traffic. Which statement is true about this configuration?
What is the purpose of the Overlay Multicast TEP in a Cisco ACI Multi-Site deployment?
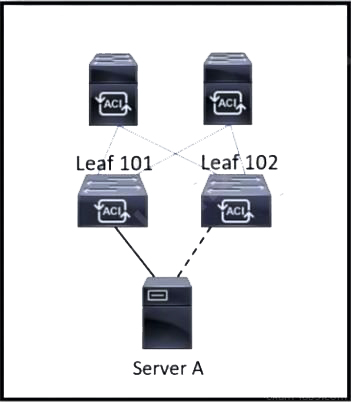
Refer to the exhibit. Server A is connected to the Cisco ACI fabric using two teamed interfaces. One interface in a team is configured as active and the other remains in standby mode. When a failover occurs and the standby interface becomes active, it uses its built-in MAC address to send traffic. Which bridge domain configuration must be applied to resolve the issue?
In the context of VMM, which protocol between ACI leaf and compute hosts ensures that the policies are pushed to the leaf switches for immediate and on demand resolution immediacy?
A Cisco ACI bridge domain and VRF are configured with a default data-plane learning configuration. Which two endpoint attributes are programmed in the leaf switch when receiving traffic? (Choose two.)
Which method does the Cisco ACI fabric use to load-balance multidestination traffic?




