Cisco 300-620 - Implementing Cisco Application Centric Infrastructure (300-620 DCACI)
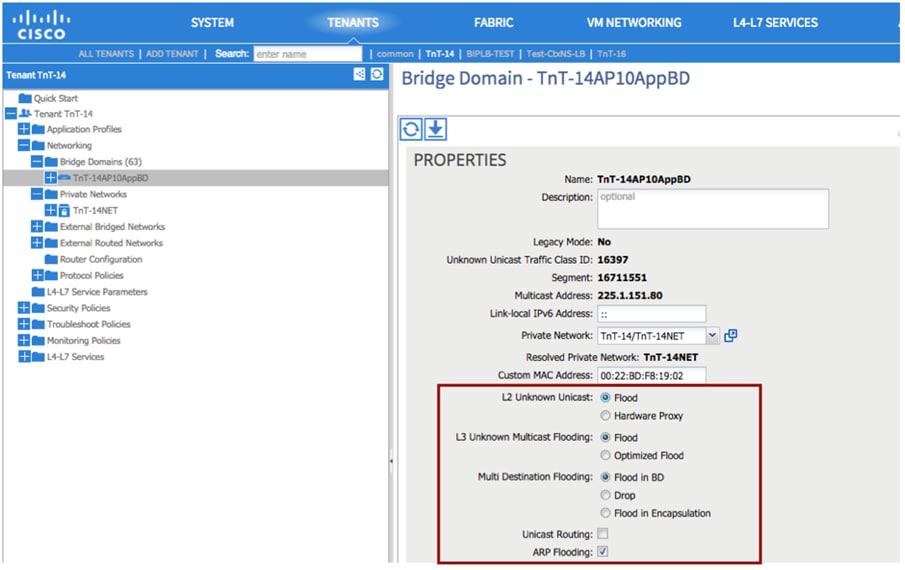
All workloads in VLAN 1001 have been migrated into EPG-1001. The requirement is to move the gateway address for VLAN 1001 from the core outside the Cisco ACI fabric into the Cisco ACI fabric. The endpoints in EPG-1001 must route traffic to endpoints in other EPGs and minimize flooded traffic in the fabric. Which configuration set is needed on the bridge domain to meet these requirements?
What is the effect of enabling the disable Remote EP learn feature?
The Application team reports that a previously existing port group has disappeared from vCenter. An engineer confirms that the VM domain association for the EPG is no longer present. Which action determines which user is responsible for the change?
The existing network and ACI fabric have been connected to support workload migration. Servers will physically terminate at the Cisco ACI, but their gateway must stay in the existing network. The solution needs to adhere to Cisco’s best practices. The engineer started configuring the relevant Bridge Domain and needs to complete the configuration. Which group of settings are required to meet these requirements?
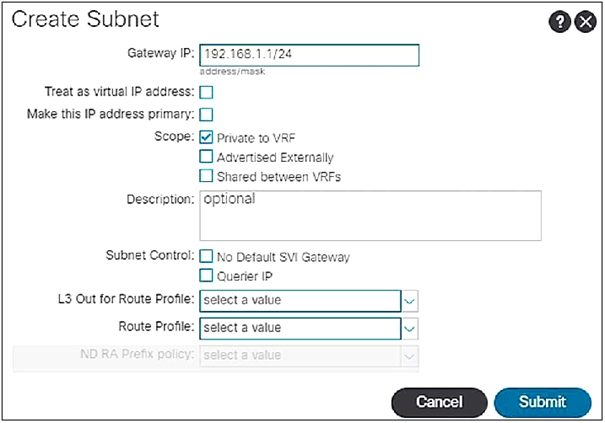
When the subnet is configured on a bridge domain, on which physical devices is the gateway IP address configured?
Which two types of interfaces are supported on border leaf switches to connect to an external router? (Choose two.)
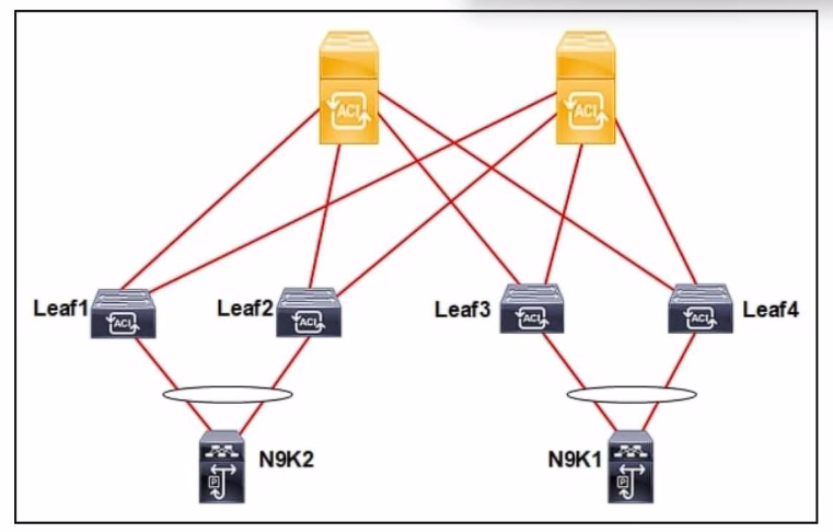
Refer to the exhibit. An engineer connects a Cisco ACI fabric to two different Cisco Nexus 9000 Series Switches. The fabric must be configured to ensure a loop-free topology and N9K1 be configured as the root bridge for VLAN 10. Which action meets these requirements?
Where are STP BPDUSs flooded in Cisco ACI fabric?
A company is implementing a new security policy to track system access, configuration, and changes. The network engineer must enable the log collection to track user login and logout attempts. In addition, any configuration changes such as a fabric node failure must be collected in the logs. The syslog policy is configured to send logs to the company SEIM appliance.
Which two log types must be enabled to meet the security requirements? (Choose two.)
An application team tells the Cisco ACI network administrator that it wants to monitor the statistics of the unicast and BUM traffic that are seen in a certain EPG. Which statement describes the collection statistics?