Cisco 300-630 - Implementing Cisco Application Centric Infrastructure - Advanced (DCACIA)
Refer to the exhibit.
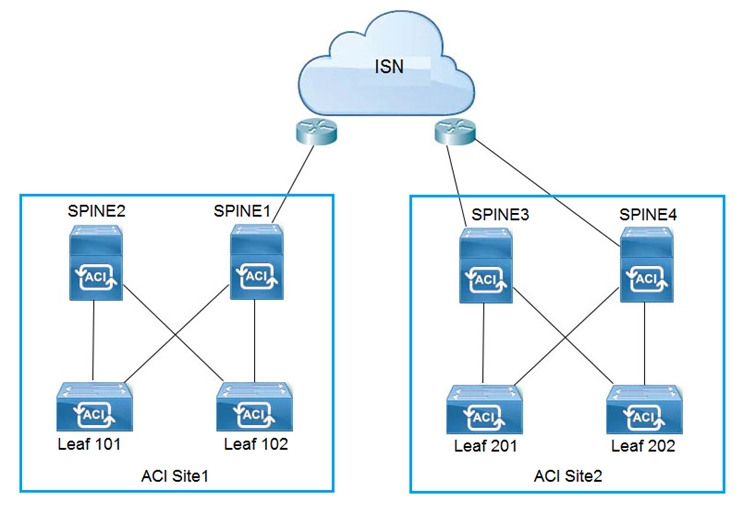
Which two configuration steps are required in ISN for Cisco ACI Multi-Site setup? (Choose two.)
An engineer implements the Cisco ACI solution and needs to confirm that the leaf switch correctly learns the remote endpoint MAC. Which information must be included in the VXLAN packet that is received from the Cisco ACI spine for the Cisco ACI leaf to learn MAC as a remote endpoint?
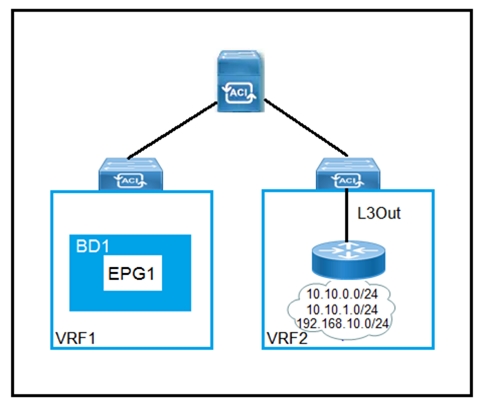
Refer to the exhibit. Drag and drop the subnets and flags from the left into the External Network Instance Profile policies on the right to create a setup that advertises only 10.10.0.0/24 and 10.10.1.0/24 prefixes in VRF1 and establishes connectivity between VRFs. Not all options are used.
Refer to the exhibit.
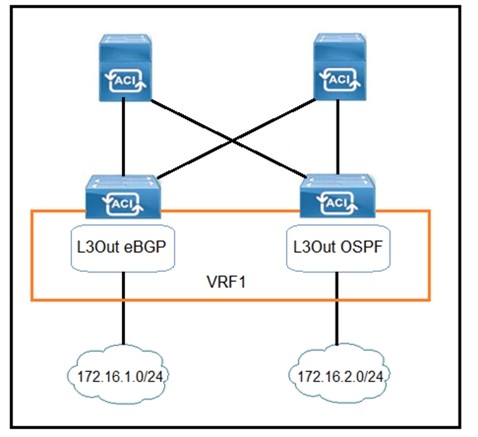
Which configuration must be implemented on L3Out EBGP to advertise out of the fabric 172.16.2.0/24 network that is learned from L3Out OSPF?
Refer to the exhibit.
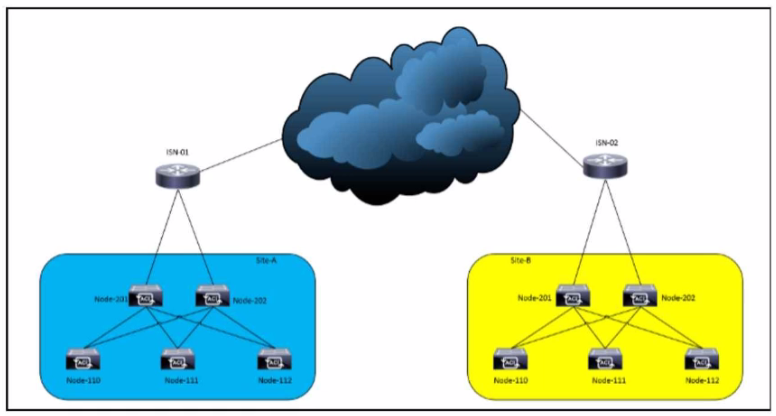
In a Cisco ACI Multi-Site deployment, traffic fails to pass between Site-A and Site-B. and an engineer troubleshoots the link between ISN-01 and Node-201. Which set of actions establishes connectivity?
How is the traffic directed to the firewall pair in a two-site Multi-Pod deployment with an active/standby firewall pair stretched across pods?
Which firewall connection allows for the integration of service nodes in transparent mode with a Cisco ACI Multi-Pod setup?
Refer to the exhibit.
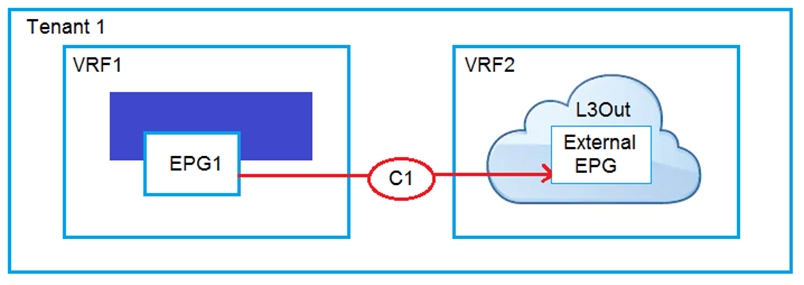
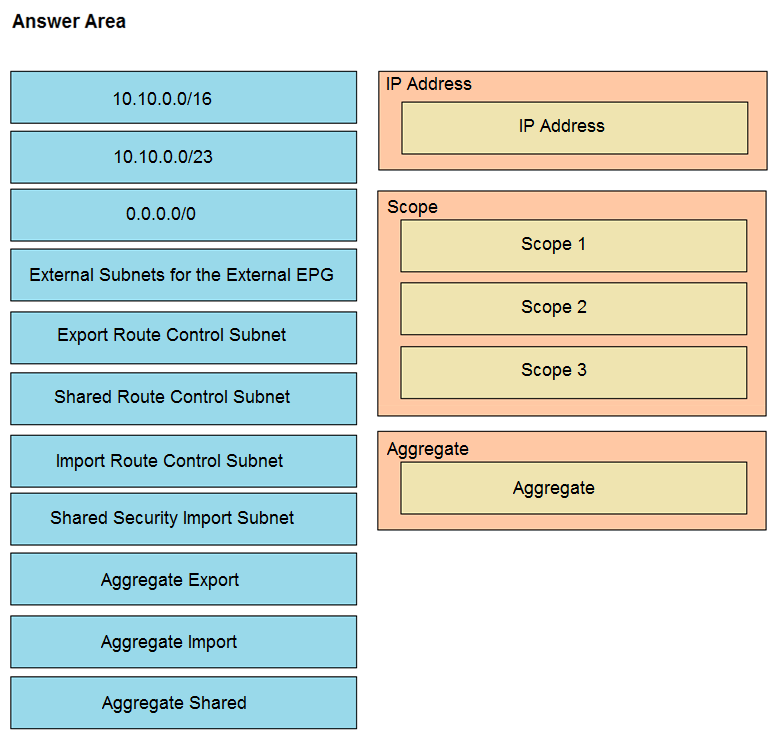
An engineer must have communication between EPG1 in VRF1 and External EPG in VRF2. Which three actions should be taken for the defined subnets in the L3Out External EPG to accomplish this goal? (Choose three.)
Refer to the exhibit.
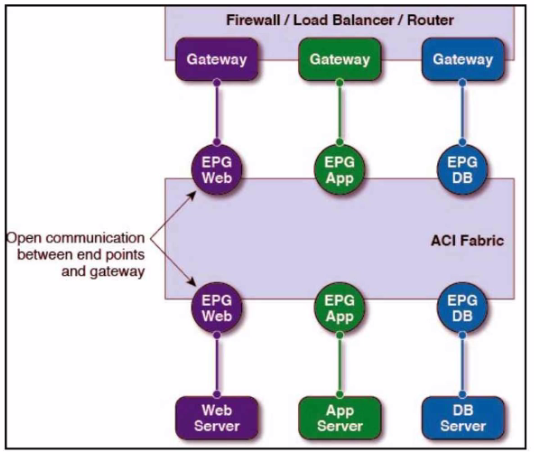
Which type of design approach is shown?
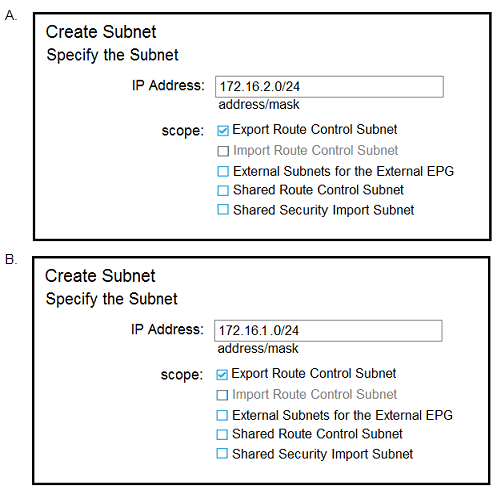
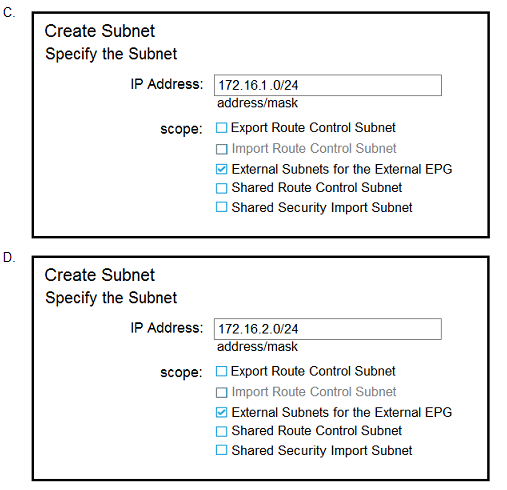
Refer to the exhibit.
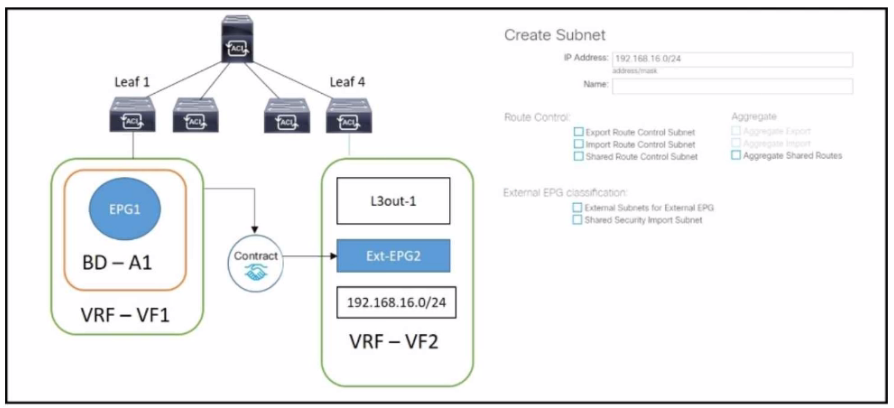
The external subnet and internal EPG1 must communicate with each other, and the L30ut traffic must leak Into the VRF named "VF1". Which configuration set accomplishes these goals?



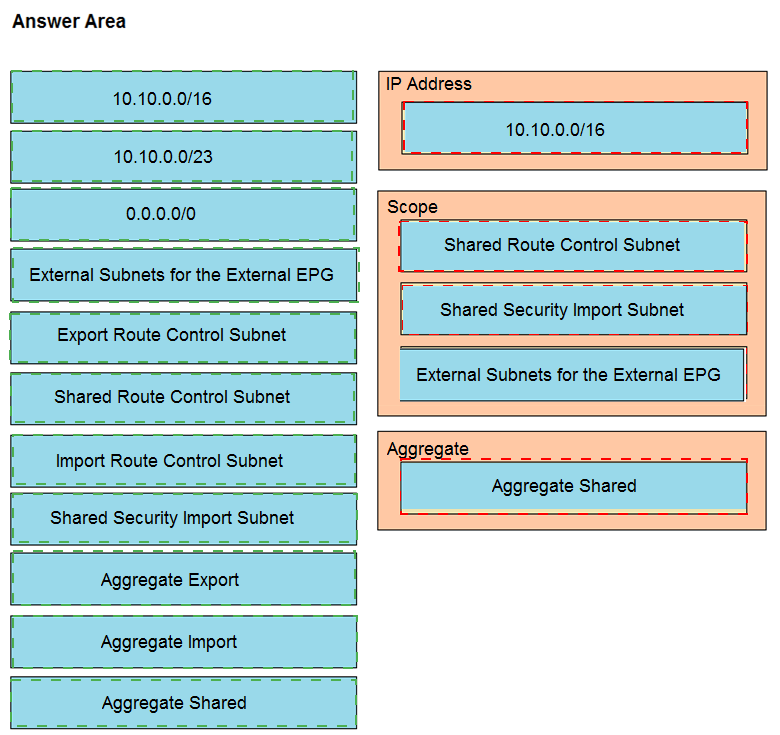
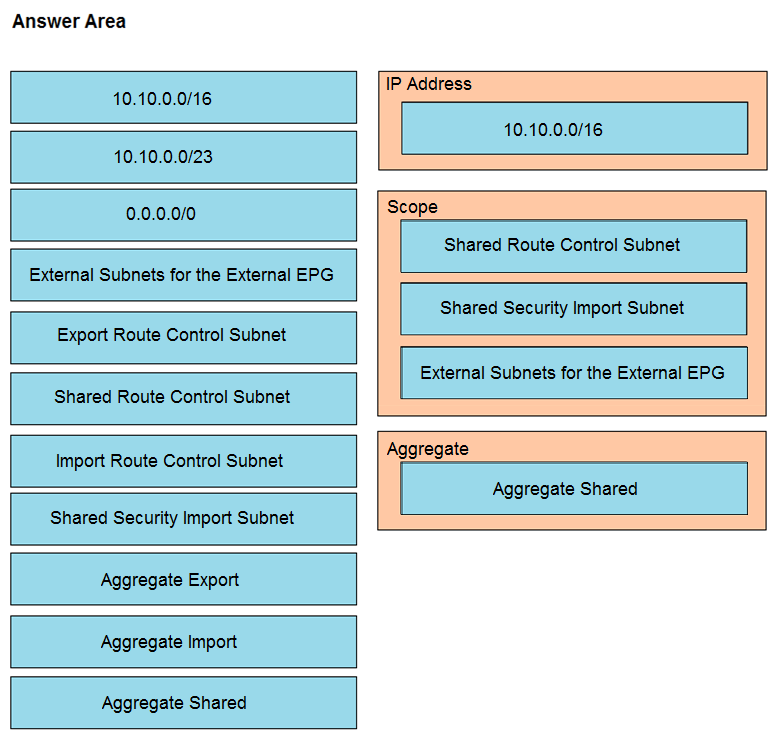 Graphical user interface
Description automatically generated
Graphical user interface
Description automatically generated