Cisco 300-710 - Securing Networks with Cisco Firepower (300-710 SNCF)
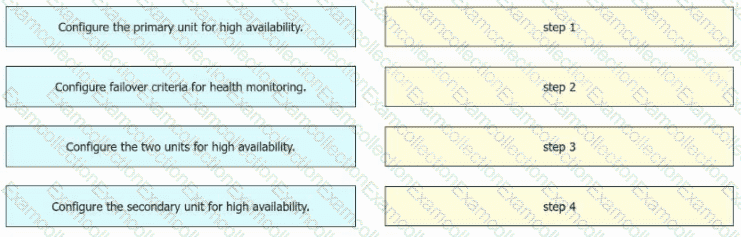
An engineer must configure high availability on two Cisco Secure Firewall Threat Defense appliances. Drag and drop the configuration steps from the left into the sequence on the right.
When an engineer captures traffic on a Cisco FTD to troubleshoot a connectivity problem, they receive a large amount of output data in the GUI tool. The engineer found that viewing the Captures this way is time-consuming and difficult lo son and filter. Which file type must the engineer export the data in so that it can be reviewed using a tool built for this type of analysis?
A network engineer is extending a user segment through an FTD device for traffic inspection without creating another IP subnet How is this accomplished on an FTD device in routed mode?
An engineer has been tasked with using Cisco FMC to determine if files being sent through the network are malware. Which two configuration tasks must be performed to achieve this file lookup? (Choose two).
Which action must be taken to configure an isolated bridge group for IRB mode on a Cisco Secure Firewall device?
A network administrator is deploying a Cisco IPS appliance and needs it to operate initially without affecting traffic flows.
It must also collect data to provide a baseline of unwanted traffic before being reconfigured to drop it. Which Cisco IPS mode meets these requirements?
An engineer must deny ICMP traffic to the networks of separate departments that use Cisco Secure Firewall Management Center. The engineer must use the same object on the relevant device for each network. What must be configured in Secure Firewall Management Center?
Network users are experiencing Intermittent issues with internet access. An engineer ident med mat the issue Is being caused by NAT exhaustion. How must the engineer change the dynamic NAT configuration to provide internet access for more users without running out of resources?
An engineer must investigate a connectivity issue by using Cisco Secure Firewall Management Center to access the Packet Capture feature on a Cisco Secure Firewall Threat Defense
device. The engineer must see a real packet going through the Secure Firewall Threat Defense device and the Snort detection actions. While reviewing the packet capture, the engineer
discovers that the Snort detection actions are missing. Which action must the engineer take to resolve the issue?
A company is deploying Cisco Secure Endpoint private cloud. The Secure Endpoint private cloud instance has already been deployed by the server administrator. The server administrator provided the hostname of the private cloud instance to the network engineer via email. What additional information does the network engineer require from the server administrator to be able to make the connection to Secure Endpoint private cloud in Cisco Secure Firewall Management Centre?