Cisco 300-720 - Securing Email with Cisco Email Security Appliance (300-720 SESA)
Which global setting is configured under Cisco ESA Scan Behavior?
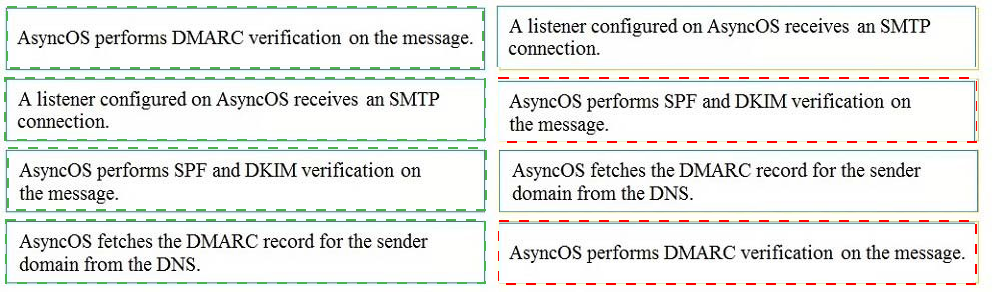
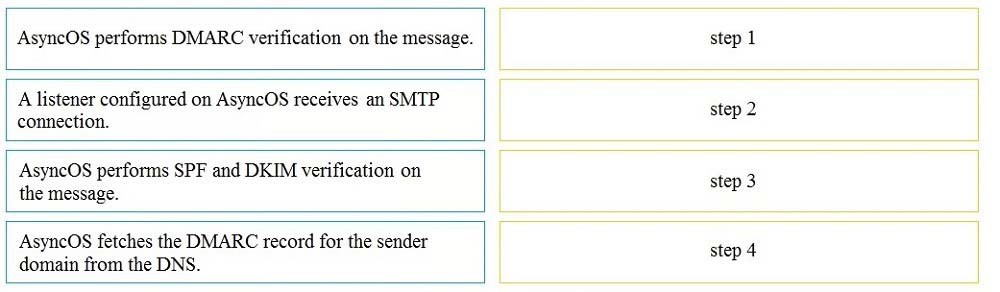
Drag and drop the AsyncOS methods for performing DMARC verification from the left into the correct order on the right.
Which action must be taken before a custom quarantine that is being used can be deleted?
Which two statements about configuring message filters within the Cisco ESA are true? (Choose two.)
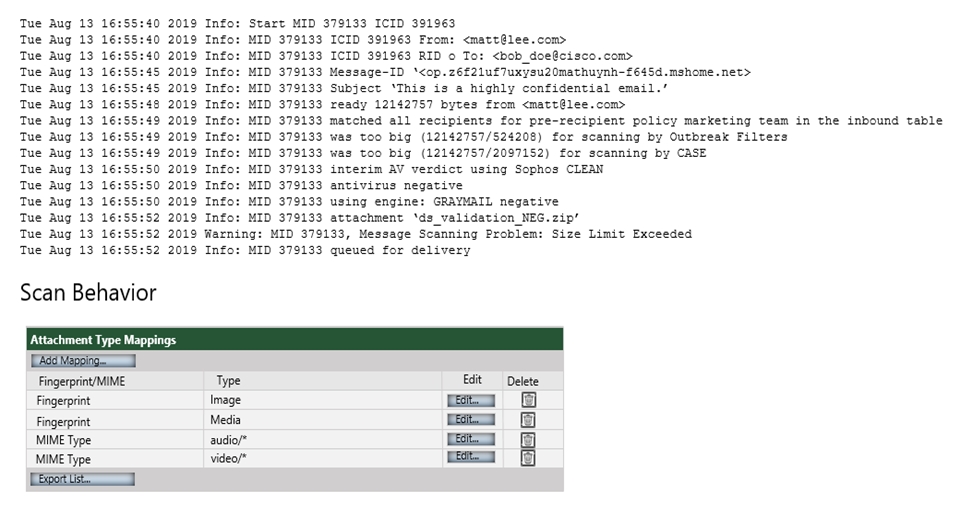
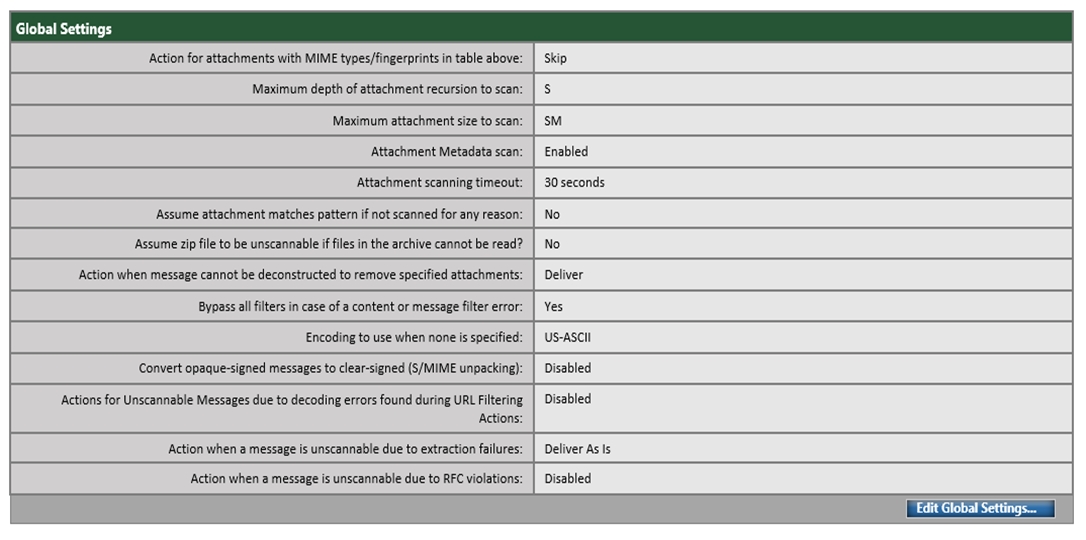
Refer to the exhibit. Which configuration on the scan behavior must be updated to allow the attachment to be scanned on the Cisco ESA?
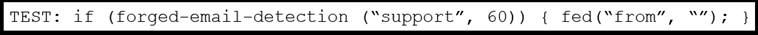
Refer to the exhibit. An engineer needs to change the existing Forged Email Detection message filter so that it references a newly created dictionary named ‘Executives’.
What should be done to accomplish this task?
Which action is a valid fallback when a client certificate is unavailable during SMTP authentication on Cisco ESA?
What are two prerequisites for implementing undesirable URL protection in Cisco ESA? (Choose two.)
What are the two different phases in the process of Cisco Secure Email Gateway performing S/MIME encryption? (Choose two.)
An administrator manipulated the subnet mask but was still unable to access the user interface. How must the administrator access the Cisco Secure Email Gateway appliance to perform the initial configuration?