Cisco 300-725 - Securing the Web with Cisco Web Security Appliance (300-725 SWSA)
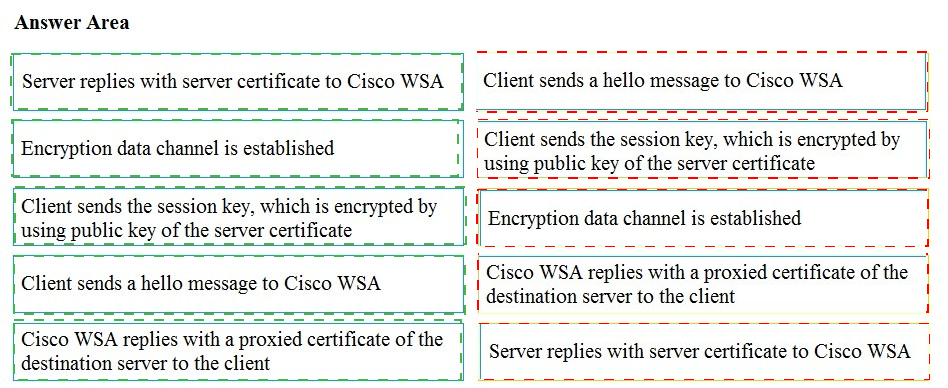
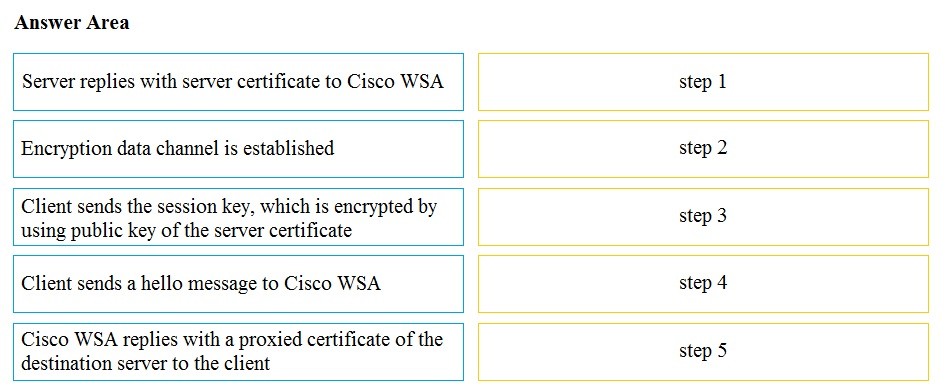
Drag and drop the actions from the left into the correct order on the right in which they occur as an HTTPS session passes through the Cisco WSA.
What is the function of a PAC file on a Cisco WSA?
Which configuration mode does the Cisco WSA use to create an Active Directory realm for Kerberos authentication?
Which statement about configuring an identification profile for machine authentication is true?
Which configuration option is suitable for explicit mode deployment?
What is used to configure WSA as an explicit proxy?
What is a benefit of integrating Cisco Cognitive Threat Analytics with a Cisco WSA?
What must be configured first when creating an access policy that matches the Active Directory group?
Which response code in the access logs indicates that a transaction was blocked due to policy?
Which type of FTP proxy does the Cisco WSA support?