Cisco 300-735 - Automating and Programming Cisco Security Solutions (300-735 SAUTO)
A developer has just completed the configuration of an API that connects sensitive internal systems. Based on company policies, the security of the data is a high priority.
Which approach must be taken to secure API keys and passwords?
Refer to the exhibit.
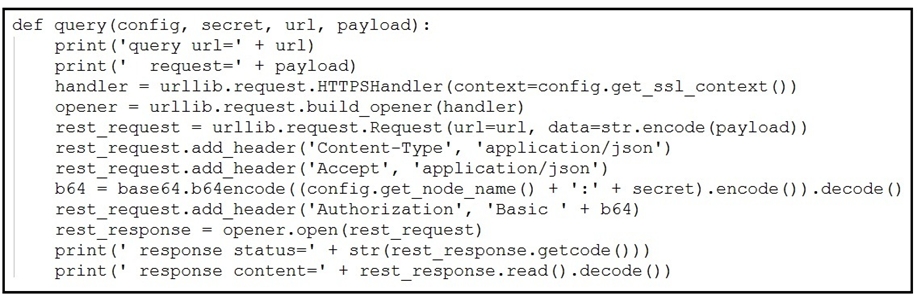
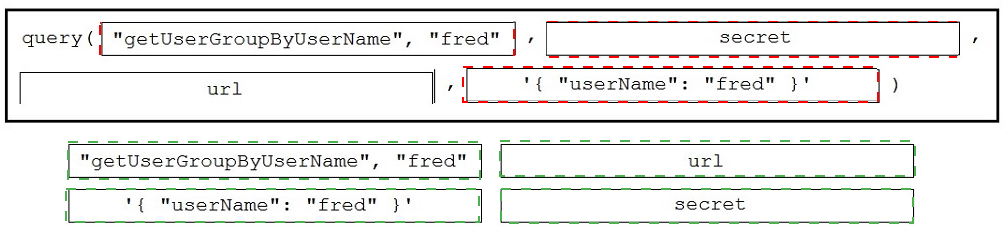
A Python function named "query" has been developed, and will be used to query the service "com.cisco.ise.session" via Cisco pxGrid 2.0 APIs.
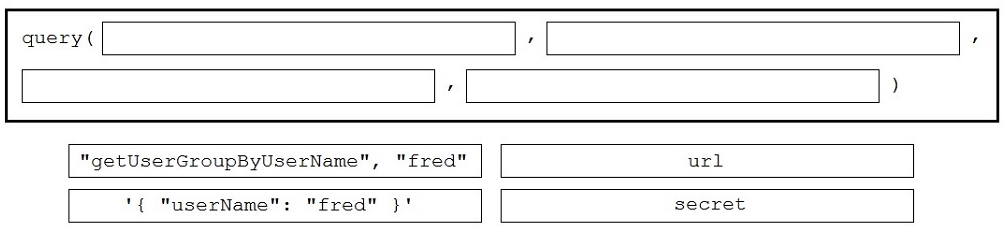
Drag and drop the code to construct a Python call to the "query" function to identify the user groups that are associated with the user "fred". Not all options are used.
Which URI string is used to create a policy that takes precedence over other applicable policies that are configured on Cisco Stealthwatch?
In Cisco AMP for Endpoints, which API queues to find the list of endpoints in the group "Finance Hosts," which
has a GUID of 6c3c2005-4c74-4ba7-8dbb-c4d5b6bafe03?
Which curl command lists all tags (host groups) that are associated with a tenant using the Cisco Stealthwatch Enterprise API?
Refer to the exhibit.

What is the purpose of the API represented by this URL?
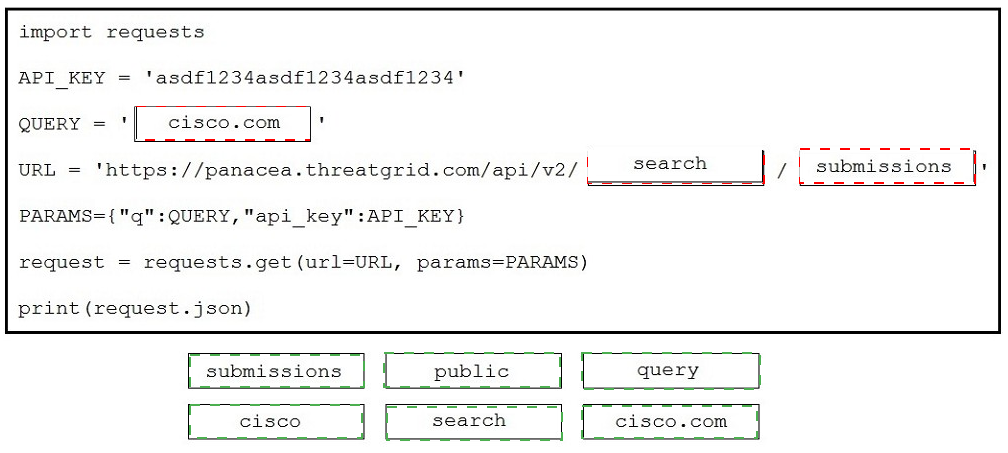
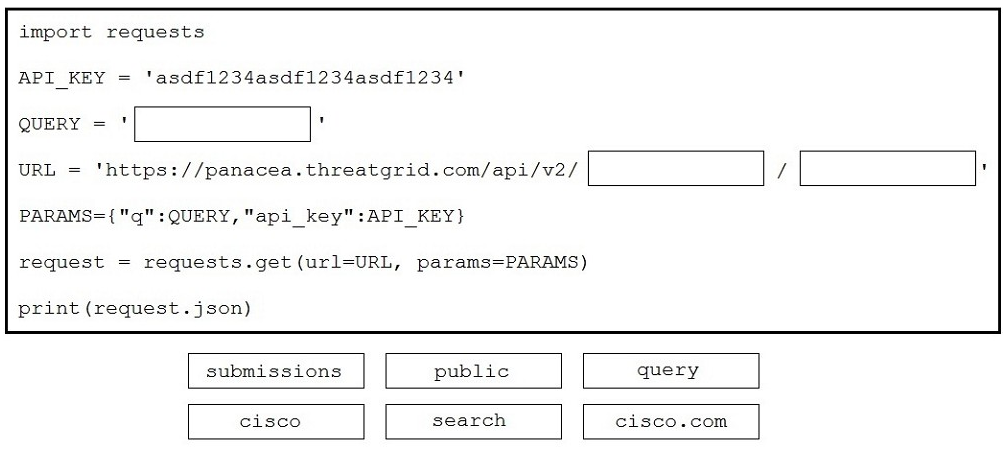
Drag and drop the code to complete the script to search Cisco ThreatGRID and return all public submission records associated with cisco.com. Not all options are used.
What are two advantages of Python virtual environments? (Choose two.)
Which two APIs are available from Cisco ThreatGRID? (Choose two.)
Refer to the exhibit. A network operator wrote a Python script to retrieve events from Cisco AMP.
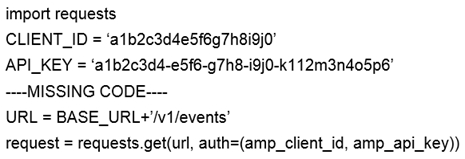
Against which API gateway must the operator make the request?