Cisco 300-910 - Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS)
Microservices architecture pattern has been applied and the system has been architected as a set of services. Each service is deployed as a set of instances for throughput and availability. In which two ways are these services packaged and deployed? (Choose two.)
Refer to the exhibit.
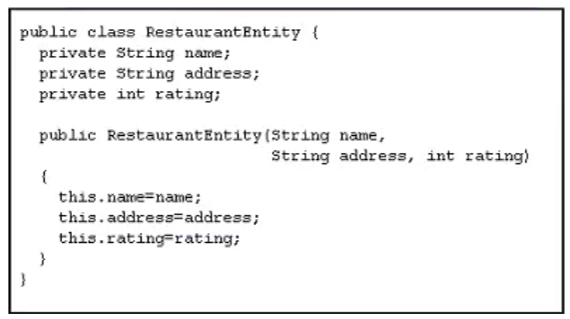
An application has been developed as a fileserver. To create this application as a fileserver. the class is used to store data in an SQL database.
Which two steps help minimize the risk of attack and compromise of the application? (Choose two.)
How long analysis systems such as Elasticsearch, Logstash, and Kibana Stack handle ingesting unstructured logs from different devices in various formats?
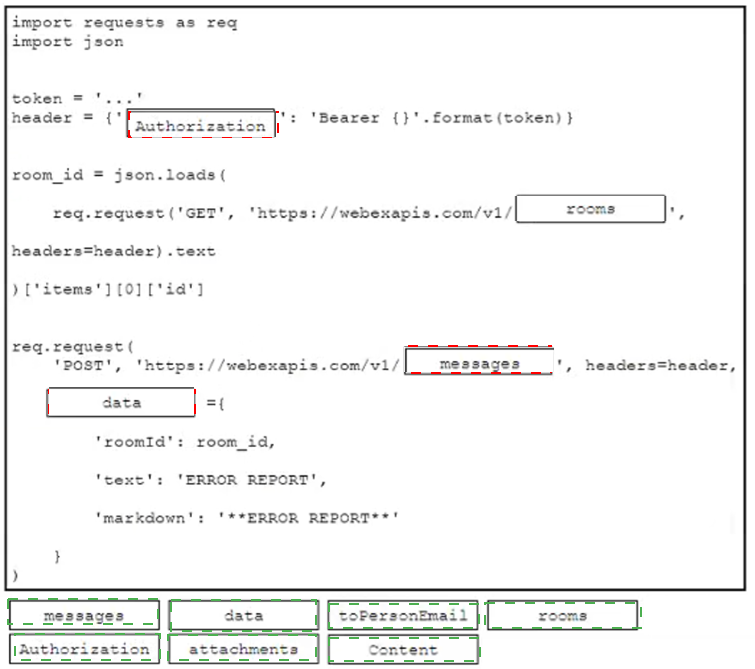
Drag and drop the code from the bottom onto the box where the code is missing to post a message to a Cisco Webex space. Not all options are used.

A DevOps engineer has built a container to host a web-server and it must run as an executable. Which command must be configured in a Dockerfile to accomplish this goal?
Which interface is most commonly used to integrate logging, monitoring, and alerting applications into your CI/ CD pipeline?
-
A developer is creating an application where each service uses a different operating system. The application components need to be isolated but must have the ability to communicate with each other.
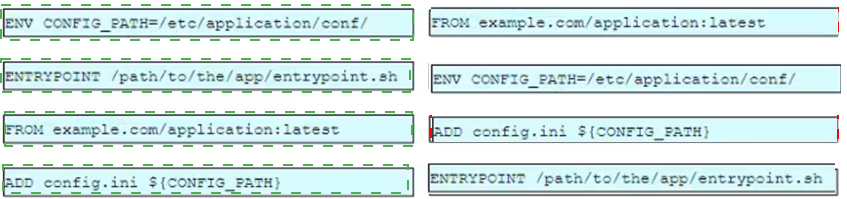
Drag and drop the entries from the left into the order on the right to create a Dockerfile that will accomplish this goal.

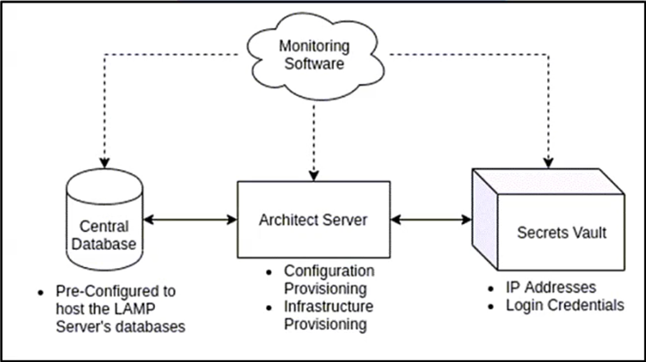
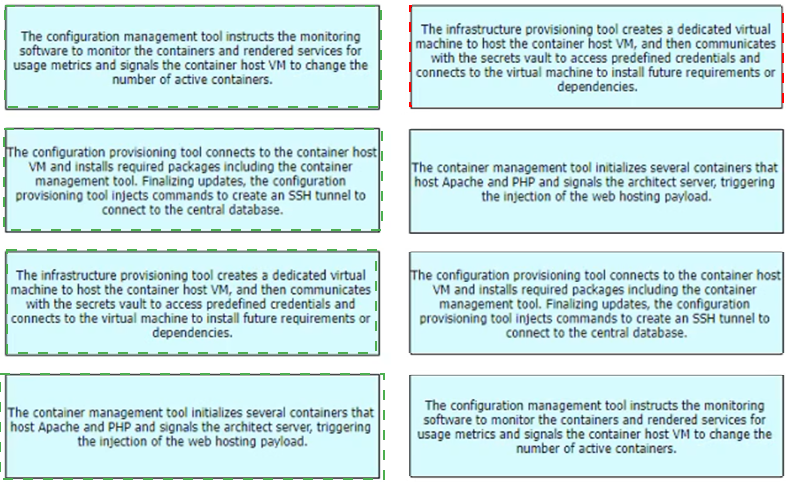
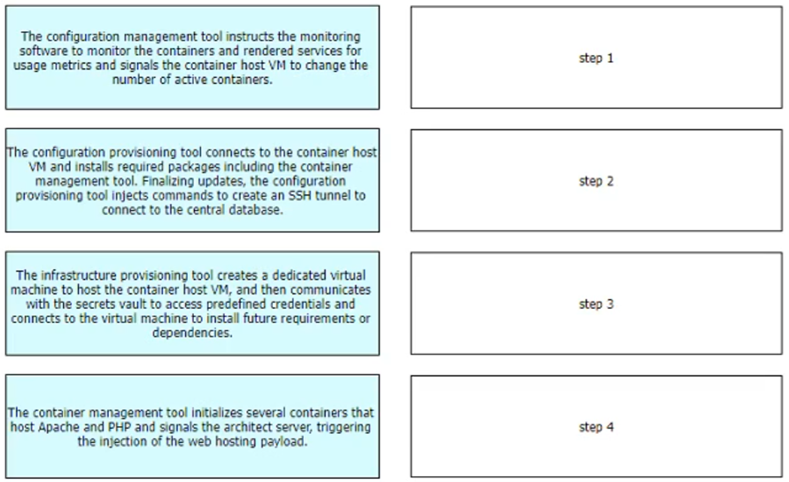
Refer to the exhibit. A containerized application that leverages a container host VM must be deployed. Drag and drop the events on the left onto their related steps on the right in order to describe the sequence behind the process.
How does eliminating hardcoded or default passwords help to secure an environment?