ECCouncil 312-39 - Certified SOC Analyst (CSA)
Identify the HTTP status codes that represents the server error.
Which of the following Windows features is used to enable Security Auditing in Windows?
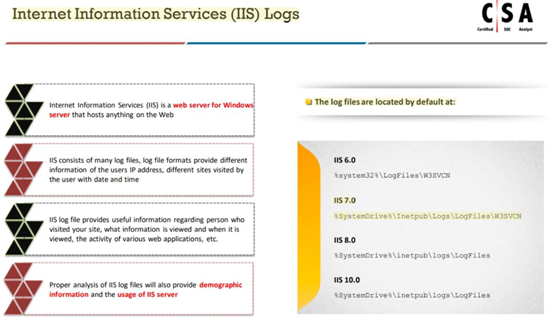
Harley is working as a SOC analyst with Powell Tech. Powell Inc. is using Internet Information Service (IIS) version 7.0 to host their website.
Where will Harley find the web server logs, if he wants to investigate them for any anomalies?
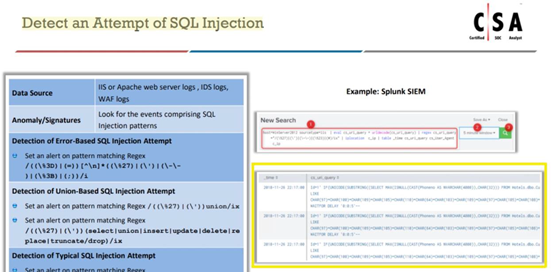
Jony, a security analyst, while monitoring IIS logs, identified events shown in the figure below.
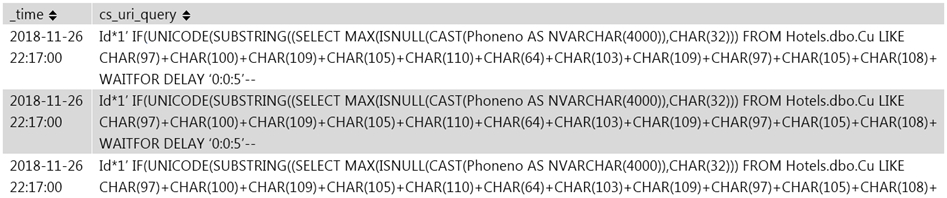
What does this event log indicate?
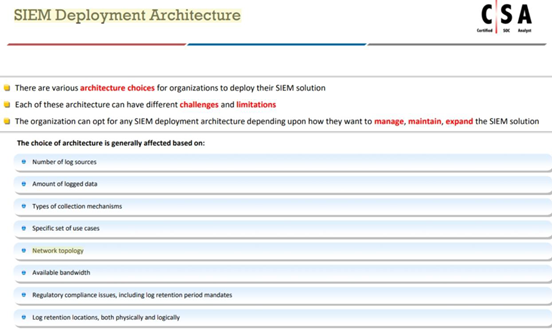
Which of the following factors determine the choice of SIEM architecture?
In which of the following incident handling and response stages, the root cause of the incident must be found from the forensic results?
Which of the following Windows Event Id will help you monitors file sharing across the network?
Peter, a SOC analyst with Spade Systems, is monitoring and analyzing the router logs of the company and wanted to check the logs that are generated by access control list numbered 210.
What filter should Peter add to the 'show logging' command to get the required output?
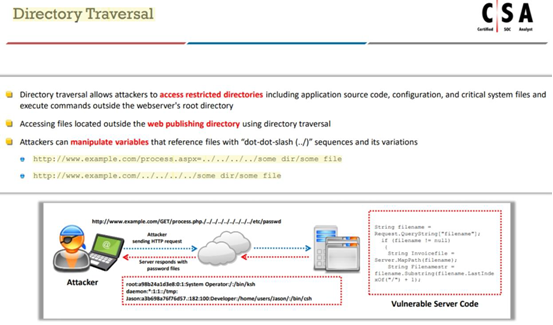
Identify the attack when an attacker by several trial and error can read the contents of a password file present in the restricted etc folder just by manipulating the URL in the browser as shown:
http://www.terabytes.com/process.php./../../../../etc/passwd
What does Windows event ID 4740 indicate?