ECCouncil 312-49 - Computer Hacking Forensic Investigator
Rusty, a computer forensics apprentice, uses the command nbtstat –c while analyzing the network information in a suspect system. What information is he looking for?
Files stored in the Recycle Bin in its physical location are renamed as Dxy.ext, where “x†represents the ___________________.
During an investigation, Noel found the following SIM card from the suspect's mobile. What does the code 89 44 represent?

Which of the following file formats allows the user to compress the acquired data as well as keep it randomly accessible?
What is the slave device connected to the secondary IDE controller on a Linux OS referred to?
What is the investigator trying to analyze if the system gives the following image as output?
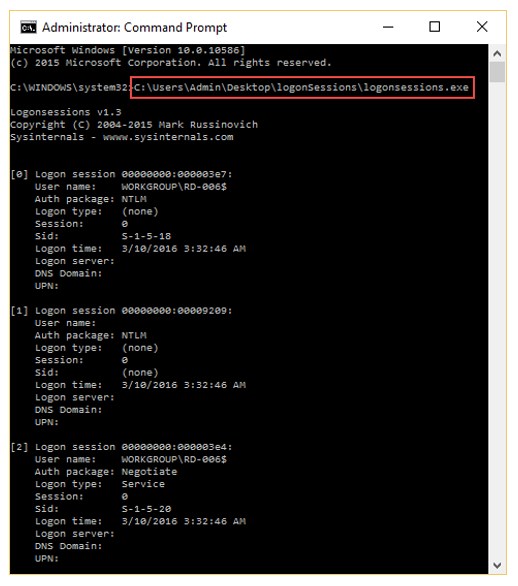
When investigating a network that uses DHCP to assign IP addresses, where would you look to determine which system (MAC address) had a specific IP address at a specific time?
An investigator has extracted the device descriptor for a 1GB thumb drive that looks like: Disk&Ven_Best_Buy&Prod_Geek_Squad_U3&Rev_6.15. What does the “Geek_Squad†part represent?
What file is processed at the end of a Windows XP boot to initialize the logon dialog box?
John is working on his company policies and guidelines. The section he is currently working on covers company documents; how they should be handled, stored, and eventually destroyed. John is concerned about the process whereby outdated documents are destroyed. What type of shredder should John write in the guidelines to be used when destroying documents?
What method of copying should always be performed first before carrying out an investigation?
Billy, a computer forensics expert, has recovered a large number of DBX files during the forensic investigation of a laptop. Which of the following email clients can he use to analyze the DBX files?
Which of the following file system is used by Mac OS X?
When a router receives an update for its routing table, what is the metric value change to that path?
As a part of the investigation, Caroline, a forensic expert, was assigned the task to examine the transaction logs pertaining to a database named Transfers. She used SQL Server Management Studio to collect the active transaction log files of the database. Caroline wants to extract detailed information on the logs, including AllocUnitId, page id, slot id, etc. Which of the following commands does she need to execute in order to extract the desired information?



