ECCouncil 312-49v10 - Computer Hacking Forensic Investigator (CHFI-v10)
> NMAP -sn 192.168.11.200-215 The NMAP command above performs which of the following?
Which of the following is a tool to reset Windows admin password?
Andie, a network administrator, suspects unusual network services running on a windows system. Which of the following commands should he use to verify unusual network services started on a Windows system?
What does Locard's Exchange Principle state?
Randy has extracted data from an old version of a Windows-based system and discovered info file Dc5.txt in the system recycle bin. What does the file name denote?
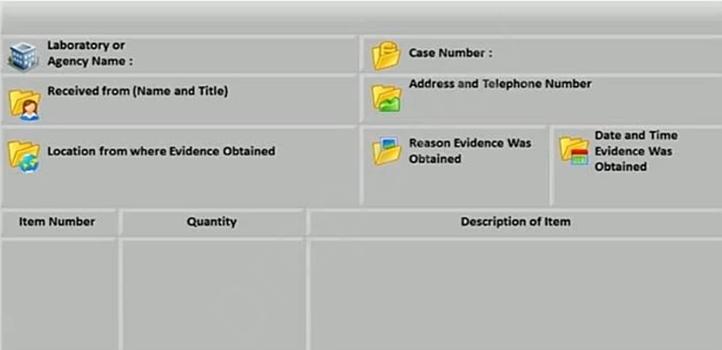
What document does the screenshot represent?
Select the tool appropriate for examining the dynamically linked libraries of an application or malware.
Graphics Interchange Format (GIF) is a ____ RGB bitmap image format for images with up to 256 distinct colors per frame.
Select the tool appropriate for finding the dynamically linked lists of an application or malware.
Hard disk data addressing is a method of allotting addresses to each _______ of data on a hard disk.
A Linux system is undergoing investigation. In which directory should the investigators look for its current state data if the system is in powered on state?
Which among the following tools can help a forensic investigator to access the registry files during postmortem analysis?
Which among the following laws emphasizes the need for each Federal agency to develop, document, and implement an organization-wide program to provide information security for the information systems that support its operations and assets?
Smith is an IT technician that has been appointed to his company's network vulnerability assessment team. He is the only IT employee on the team. The other team members include employees from
Accounting, Management, Shipping, and Marketing. Smith and the team members are having their first meeting to discuss how they will proceed. What is the first step they should do to create the network
vulnerability assessment plan?
Which of the following is a federal law enacted in the US to control the ways that financial institutions deal with the private information of individuals?



