ECCouncil 312-49v10 - Computer Hacking Forensic Investigator (CHFI-v10)
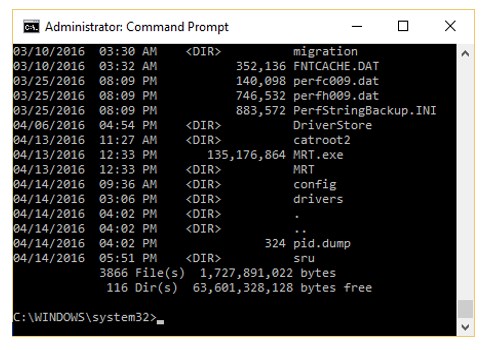
The given image displays information about date and time of installation of the OS along with service packs, patches, and sub-directories. What command or tool did the investigator use to view this output?
Meyer Electronics Systems just recently had a number of laptops stolen out of their office. On these laptops contained sensitive corporate information regarding patents and company strategies. A month after the laptops were stolen, a competing company was found to have just developed products that almost exactly duplicated products that Meyer produces. What could have prevented this information from being stolen from the laptops?
Software firewalls work at which layer of the OSI model?
Which of the following file system is used by Mac OS X?
The MD5 program is used to:
What TCP/UDP port does the toolkit program netstat use?
You are a security analyst performing a penetration tests for a company in the Midwest. After some initial reconnaissance, you discover the IP addresses of some Cisco routers used by the company. You type in the following URL that includes the IP address of one of the routers:
http://172.168.4.131/level/99/exec/show/config
After typing in this URL, you are presented with the entire configuration file for that router. What have you discovered?
When examining a file with a Hex Editor, what space does the file header occupy?
When examining a hard disk without a write-blocker, you should not start windows because Windows will write data to the:
Under which Federal Statutes does FBI investigate for computer crimes involving e-mail scams and mail fraud?
This organization maintains a database of hash signatures for known software.
When cataloging digital evidence, the primary goal is to
At what layer of the OSI model do routers function on?
John and Hillary works at the same department in the company. John wants to find out Hillary's network password so he can take a look at her documents on the file server. He enables Lophtcrack program to sniffing mode. John sends Hillary an email with a link to Error! Reference source not found. What information will he be able to gather from this?
Chris has been called upon to investigate a hacking incident reported by one of his clients. The company suspects the involvement of an insider accomplice in the attack. Upon reaching the incident scene, Chris secures the physical area, records the scene using visual media. He shuts the system down by pulling the power plug so that he does not disturb the system in any way. He labels all cables and connectors prior to disconnecting any. What do you think would be the next sequence of events?



