ECCouncil 312-49v10 - Computer Hacking Forensic Investigator (CHFI-v10)
Which of the following commands shows you the names of all open shared files on a server and the number of file locks on each file?
On an Active Directory network using NTLM authentication, where on the domain controllers are the passwords stored?
Which of the following tool can the investigator use to analyze the network to detect Trojan activities?
Sectors are pie-shaped regions on a hard disk that store data. Which of the following parts of a hard disk do not contribute in determining the addresses of data?
Smith, a network administrator with a large MNC, was the first to arrive at a suspected crime scene involving criminal use of compromised computers. What should be his first response while maintaining the integrity of evidence?
Who is responsible for the following tasks?
When investigating a wireless attack, what information can be obtained from the DHCP logs?
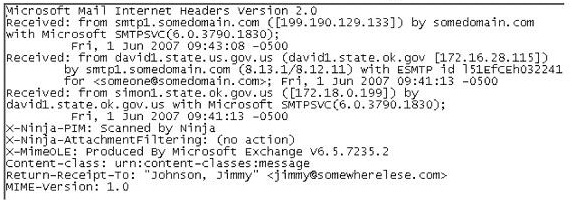
In the following email header, where did the email first originate from?
Charles has accidentally deleted an important file while working on his Mac computer. He wants to recover the deleted file as it contains some of his crucial business secrets. Which of the following tool will help Charles?
What is the smallest physical storage unit on a hard drive?
Which rule requires an original recording to be provided to prove the content of a recording?
Where is the startup configuration located on a router?
In Steganalysis, which of the following describes a Known-stego attack?
What hashing method is used to password protect Blackberry devices?
Which of the following files stores information about a local Google Drive installation such as User email ID, Local Sync Root Path, and Client version installed?



