ECCouncil 312-50 - Certified Ethical Hacker Exam
A software tester is randomly generating invalid inputs in an attempt to crash the program. Which of the following is a software testing technique used to determine if a software program properly handles a wide range of invalid input?
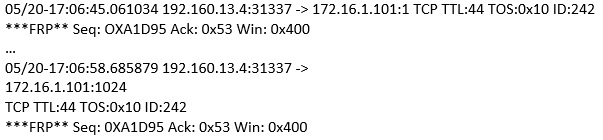
(Note: the student is being tested on concepts learnt during passive OS fingerprinting, basic TCP/IP connection concepts and the ability to read packet signatures from a sniff dump.). Snort has been used to capture packets on the network. On studying the packets, the penetration tester finds it to be abnormal. If you were the penetration tester, why would you find this abnormal?
What is odd about this attack? Choose the best answer.
When security and confidentiality of data within the same LAN is of utmost priority, which IPSec mode should you implement?
Which of the following is a common Service Oriented Architecture (SOA) vulnerability?
Which of the following descriptions is true about a static NAT?
Which element of Public Key Infrastructure (PKI) verifies the applicant?
The fundamental difference between symmetric and asymmetric key cryptographic systems is that symmetric key cryptography uses which of the following?
If an e-commerce site was put into a live environment and the programmers failed to remove the secret entry point that was used during the application development, what is this secret entry point known as?
What is the primary drawback to using advanced encryption standard (AES) algorithm with a 256 bit key to share sensitive data?
Which statement best describes a server type under an N-tier architecture?



