ECCouncil 312-50 - Certified Ethical Hacker Exam
Which of the following LM hashes represent a password of less than 8 characters? (Choose two.)
Name two software tools used for OS guessing? (Choose two.)
What is the difference between the AES and RSA algorithms?
Which tool allows analysts and pen testers to examine links between data using graphs and link analysis?
Which of the following is the primary objective of a rootkit?
Which of the following is designed to identify malicious attempts to penetrate systems?
MX record priority increases as the number increases. (True/False.)
Which service in a PKI will vouch for the identity of an individual or company?
While reviewing the result of scanning run against a target network you come across the following:
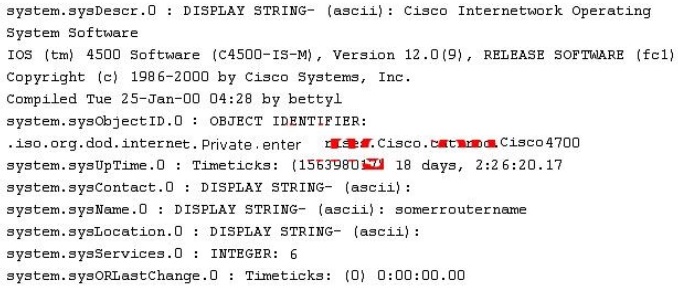
Which among the following can be used to get this output?
Sandra has been actively scanning the client network on which she is doing a vulnerability assessment test.
While conducting a port scan she notices open ports in the range of 135 to 139.
What protocol is most likely to be listening on those ports?



