ECCouncil 312-50 - Certified Ethical Hacker Exam
An attacker changes the profile information of a particular user (victim) on the target website. The attacker uses this string to update the victim’s profile to a text file and then submit the data to the attacker’s database.
What is this type of attack (that can use either HTTP GET or HTTP POST) called?
Which tier in the N-tier application architecture is responsible for moving and processing data between the tiers?
By using a smart card and pin, you are using a two-factor authentication that satisfies
In this attack, a victim receives an e-mail claiming from PayPal stating that their account has been disabled and confirmation is required before activation. The attackers then scam to collect not one but two credit card numbers, ATM PIN number and other personal details. Ignorant users usually fall prey to this scam.
Which of the following statement is incorrect related to this attack?
What are two things that are possible when scanning UDP ports? (Choose two.)
What is the most common method to exploit the “Bash Bug†or “ShellShock" vulnerability?
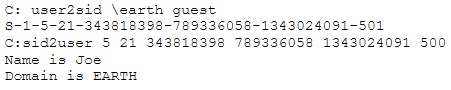
What did the following commands determine?
If you are to determine the attack surface of an organization, which of the following is the BEST thing to do?
You are performing a penetration test. You achieved access via a buffer overflow exploit and you proceed to find interesting data, such as files with usernames and passwords. You find a hidden folder that has the administrator's bank account password and login information for the administrator's bitcoin account.
What should you do?
A company's security policy states that all Web browsers must automatically delete their HTTP browser cookies upon terminating. What sort of security breach is this policy attempting to mitigate?



