ECCouncil 312-50v13 - Certified Ethical Hacker Exam (CEHv13)
During security awareness training, which scenario best describes a tailgating social engineering attack?
Why is a penetration test considered to be more thorough than a vulnerability scan?
Which of the following are well-known password-cracking programs?
In the field of cryptanalysis, what is meant by a “rubber-hose" attack?
You are an ethical hacker contracted to conduct a security audit for a company. During the audit, you discover that the company's wireless network is using WEP encryption. You understand the vulnerabilities associated with WEP and plan to recommend a more secure encryption method. Which of the following would you recommend as a Suitable replacement to enhance the security of the company's wireless network?
What is the role of test automation in security testing?
A Security Engineer at a medium-sized accounting firm has been tasked with discovering how much information can be obtained from the firm’s public-facing web servers. The engineer decides to start by using netcat to port 80.
The engineer receives this output:
HTTP/1.1 200 OK
Server: Microsoft-IIS/6
...
Which of the following is an example of what the engineer performed?
Jane is working as a security professional at CyberSol Inc. She was tasked with ensuring the authentication and integrity of messages being transmitted in the corporate network. To encrypt the messages, she implemented a security model in which every user in the network maintains a ring of public keys. In this model, a user needs to encrypt a message using the receiver's public key, and only the receiver can decrypt the message using their private key. What is the security model implemented by Jane to secure corporate messages?
An ethical hacker is testing the security of a website's database system against SQL Injection attacks. They discover that the IDS has a strong signature detection mechanism to detect typical SQL injection patterns.
Which evasion technique can be most effectively used to bypass the IDS signature detection while performing a SQL Injection attack?
While using your bank’s online servicing you notice the following string in the URL bar:
"http://www.MyPersonalBank.com/account?id=368940911028389 &Damount=10980&Camount=21"
You observe that if you modify the Damount & Camount values and submit the request, that data on the web page reflects the changes.
Which type of vulnerability is present on this site?
Switches maintain a CAM Table that maps individual MAC addresses on the network to physical ports on the switch. In a MAC flooding attack, a switch is fed with many Ethernet frames, each containing different source MAC addresses, by the attacker. Switches have a limited memory for mapping various MAC addresses to physical ports.
What happens when the CAM table becomes full?
You want to analyze packets on your wireless network. Which program would you use?
You are tasked to configure the DHCP server to lease the last 100 usable IP addresses in subnet to. 1.4.0/23. Which of the following IP addresses could be teased as a result of the new configuration?
A penetration tester is evaluating a web application that does not properly validate the authenticity of HTTP requests. The tester suspects the application is vulnerable to Cross-Site Request Forgery (CSRF). Which approach should the tester use to exploit this vulnerability?
Under what conditions does a secondary name server request a zone transfer from a primary name server?
ViruXine.W32 virus hides its presence by changing the underlying executable code. This virus code mutates while keeping the original algorithm intact — the code changes itself each time it runs, but the function of the code (its semantics) does not change at all.
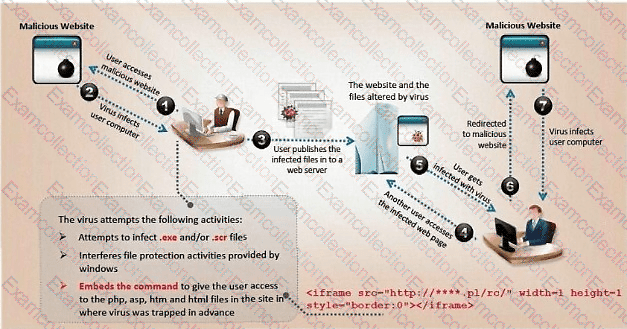
Here is a section of the virus code (refer to image), where the loop performs XOR encryption and changes the way the code looks every time it is executed.
What is this technique called?
A cybersecurity consultant suspects attackers are attempting to evade an Intrusion Detection System (IDS). Which technique is most likely being used?
You want to do an ICMP scan on a remote computer using hping2. What is the proper syntax?
How does a denial-of-service (DoS) attack work?
A company’s Web development team has become aware of a certain type of security vulnerability in their Web software. To mitigate the possibility of this vulnerability being exploited, the team wants to modify the software requirements to disallow users from entering HTML as input into their Web application.
What kind of Web application vulnerability likely exists in their software?



