ECCouncil 312-50v13 - Certified Ethical Hacker Exam (CEHv13)
Bob, your senior colleague, has sent you a mail regarding a deal with one of the clients. You are requested to accept the offer and you oblige. After 2 days, Bab denies that he had ever sent a mail. What do you want to ““knowâ€â€ to prove yourself that it was Bob who had send a mail?
The establishment of a TCP connection involves a negotiation called three-way handshake. What type of message does the client send to the server in order to begin this negotiation?
Password cracking programs reverse the hashing process to recover passwords. (True/False.)
A critical flaw exists in a cloud provider’s API. What is the most likely threat?
Attackers abused Android Debug Bridge (ADB) to issue unauthorized commands. What is the strongest countermeasure?
Bob was recently hired by a medical company after it experienced a major cyber security breach. Many patients are complaining that their personal medical records are fully exposed on the Internet and someone can find them with a simple Google search. Bob's boss is very worried because of regulations that protect those data. Which of the following regulations is mostly violated?
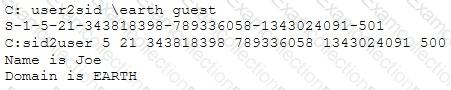
What did the following commands determine?
[Image Output of USER2SID and SID2USER showing that SID ending in -500 corresponds to user Joe on domain EARTH]
Gilbert, a web developer, uses a centralized web API to reduce complexity and increase the Integrity of updating and changing data. For this purpose, he uses a web service that uses HTTP methods such as PUT. POST. GET. and DELETE and can improve the overall performance, visibility, scalability, reliability, and portability of an application. What is the type of web-service API mentioned in the above scenario?
Which of the following Google advanced search operators helps an attacker in gathering information about websites that are similar to a specified target URL?
A multinational corporation recently survived a severe Distributed Denial-of-Service (DDoS) attack and has implemented enhanced security measures. During an audit, you discover that the organization uses both hardware- and cloud-based solutions to distribute incoming traffic in order to absorb and mitigate DDoS attacks while ensuring legitimate traffic remains available. What type of DDoS mitigation strategy is the company utilizing?
Attempting an injection attack on a web server based on responses to True/False QUESTION NO:s is called which of the following?
Encrypted session tokens vary in length, indicating inconsistent encryption strength. What is the best mitigation?
You are the chief security officer at AlphaTech, a tech company that specializes in data storage solutions. Your company is developing a new cloud storage platform where users can store their personal files. To ensure data security, the development team is proposing to use symmetric encryption for data at rest. However, they are unsure of how to securely manage and distribute the symmetric keys to users. Which of the following strategies
would you recommend to them?
What is GINA?
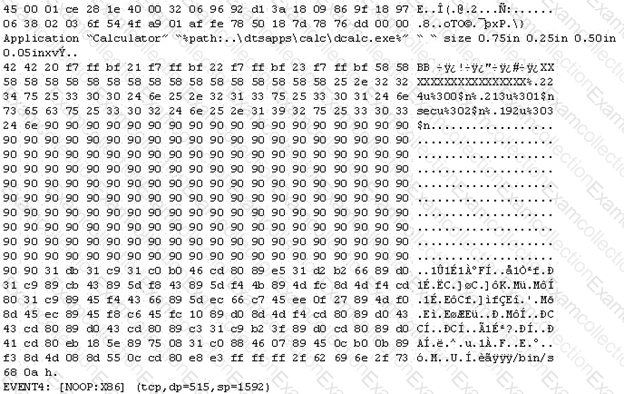
The following is an entry captured by a network IDS. You are assigned the task of analyzing this entry.
You notice the value 0x90, which is the most common NOOP instruction for the Intel processor.
You also notice "/bin/sh" in the ASCII part of the output.
As an analyst, what would you conclude about the attack?
Which of the following Bluetooth hacking techniques does an attacker use to send messages to users without the recipient’s consent, similar to email spamming?
From the following table, identify the wrong answer in terms of Range (ft).
Standard
Range (ft)
802.11a
150–150
802.11b
150–150
802.11g
150–150
802.16 (WiMax)
30 miles
A system administrator observes that several machines in the network are repeatedly sending out traffic to unknown IP addresses. Upon inspection, these machines were part of a coordinated spam campaign. What is the most probable cause?
A penetration tester identifies that a web application's login form is not using secure password hashing mechanisms, allowing attackers to steal passwords if the database is compromised. What is the best approach to exploit this vulnerability?
Infected systems receive external instructions over HTTP and DNS, with fileless payloads modifying system components. What is the most effective action to detect and disrupt this malware?



