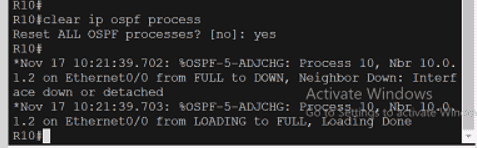
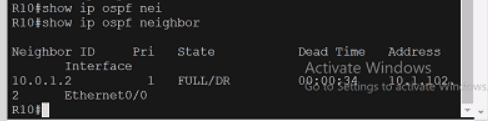
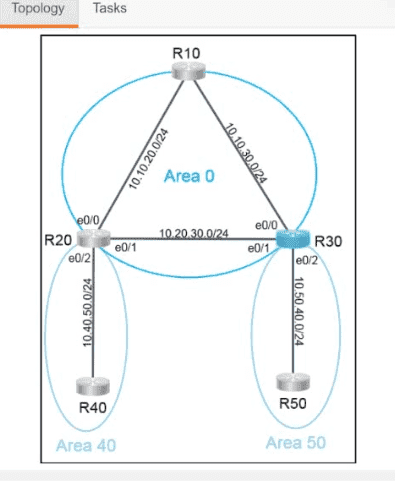
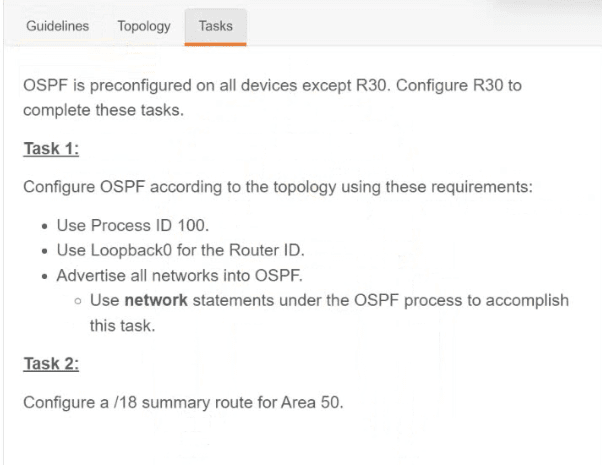
Cisco 350-401 - Implementing Cisco Enterprise Network Core Technologies (350-401 ENCOR)
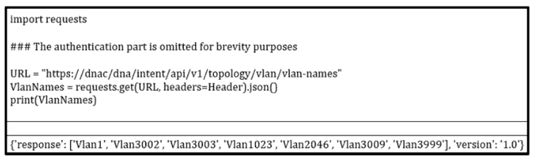
Refer to the exibit. How should the programmer access the list of VLANs that are recevied via the API call?
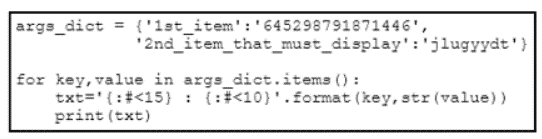
Refer to the exhibit. What is the output of this code?
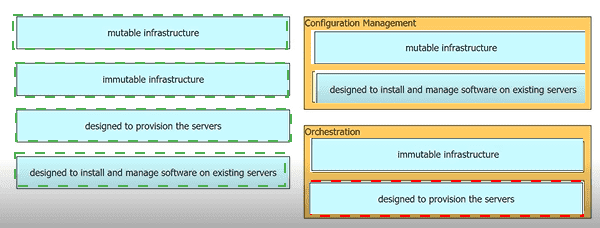
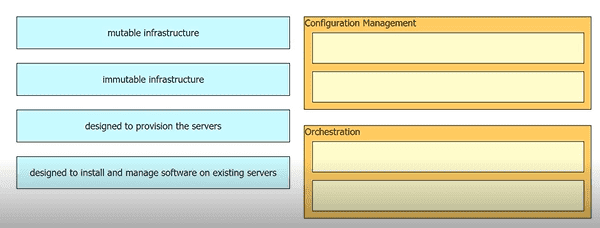
Drag and drop the characteristics from the left onto the orchestration tool classifications on the right.
What is a characteristics of Wi-Fi channels?
Which definition describes JWT in regard to REST API security?
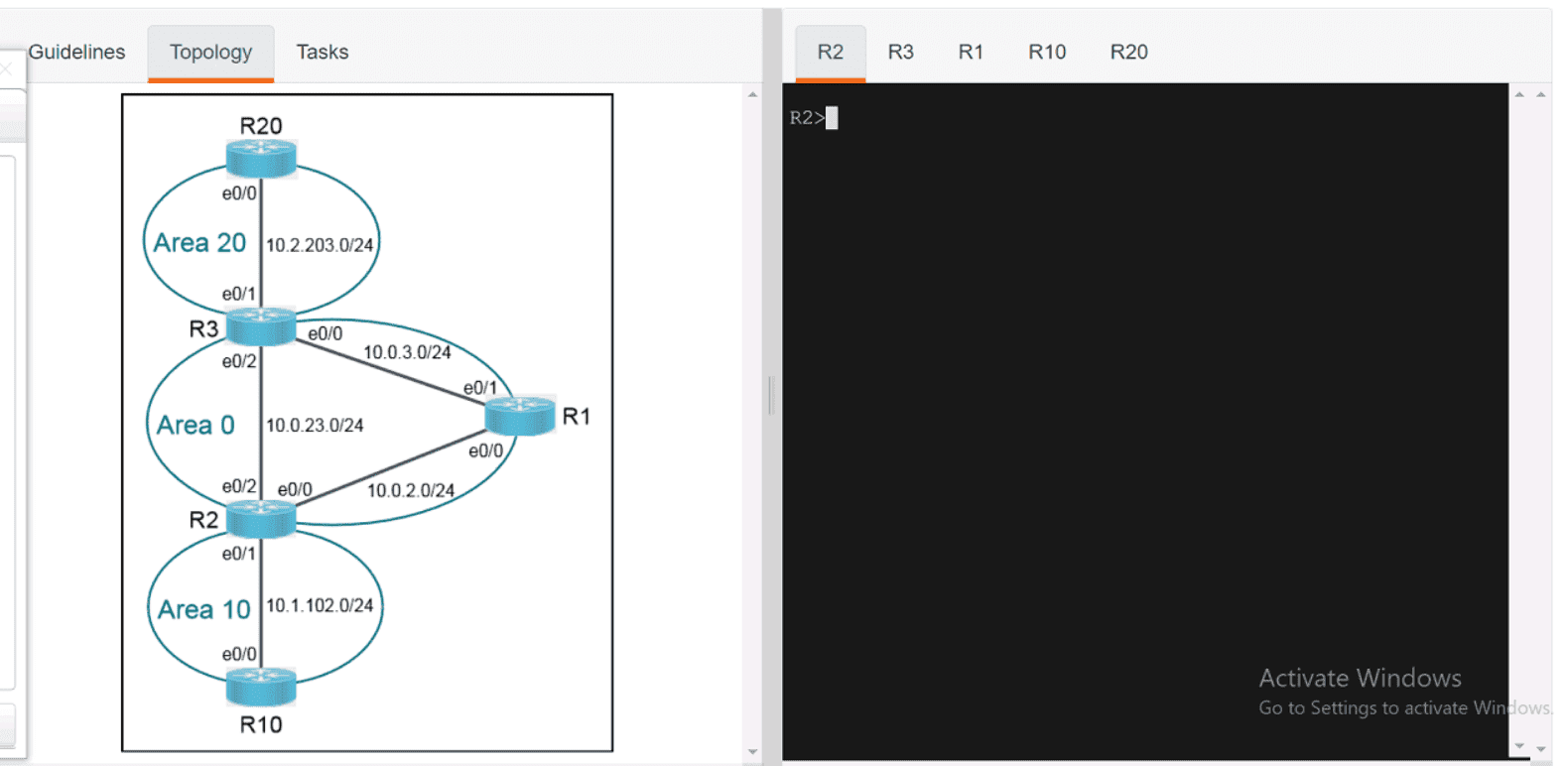
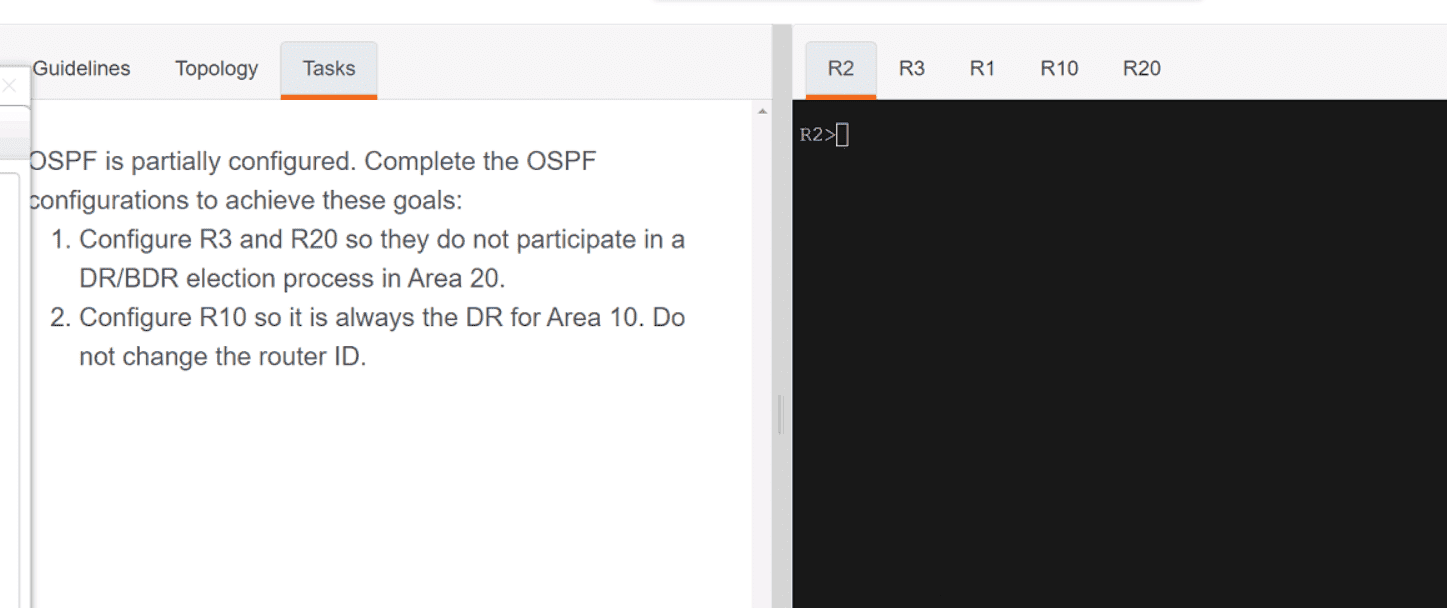
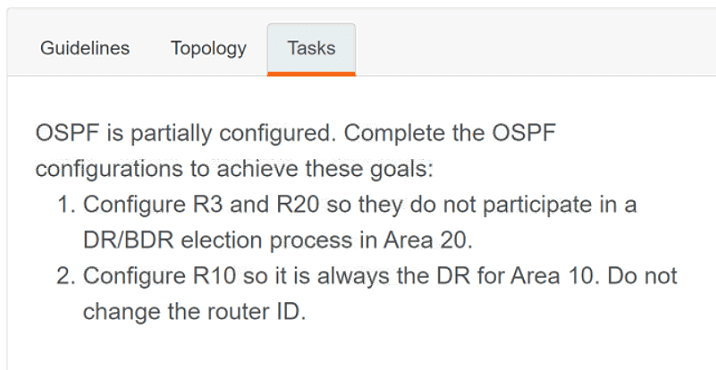
In a Cisco SD-Access network architecture, which access layer cabling design is optimal for the underlay network?
What is the name of the numerical relationship of the wireless signal compared to the noise floor?
What is contained in the VXLAN header?