Cisco 350-401 - Implementing Cisco Enterprise Network Core Technologies (350-401 ENCOR)
What is one benefit of adopting a data modeling language?
Which two methods are used to assign security group tags to the user in a Cisco Trust Sec architecture? (Choose two.)
Which three methods does Cisco Catalyst Center (formerly DNA Center) use to discover devices? (Choose three.)
Which NGFW mode block flows crossing the firewall?
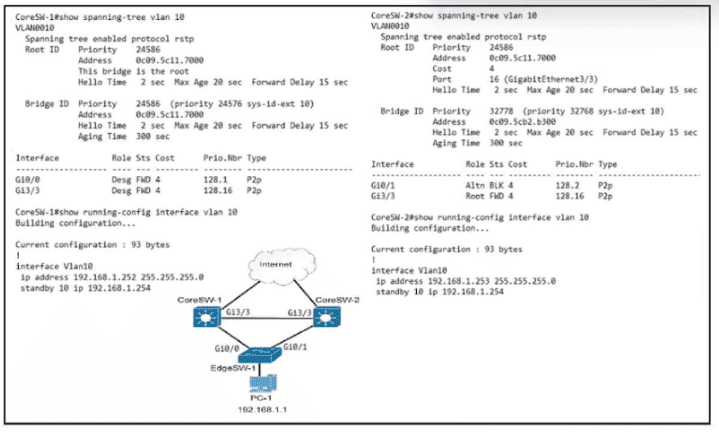
Refer to the exhibit. Which configuration causes the traffic from PC-1 to the internet to use the link between CoreSW-1 and CoreSW-2 when both switches are up?

Which language can be used to model configuration and state data?
What are two best practices when designing a campus Layer 3 infrastructure? (Choose two.)
Which two Cisco SD-Access components provide communication between traditional network elements and the controller layer? (Choose two.)
Which data format can be used for an API request?
Which statement describes the Cisco SD-Access plane functionality for fabric-enabled wireless?



