Cisco 350-401 - Implementing Cisco Enterprise Network Core Technologies (350-401 ENCOR)
At which plane does vBond operate in Cisco SD-WAN solutions?
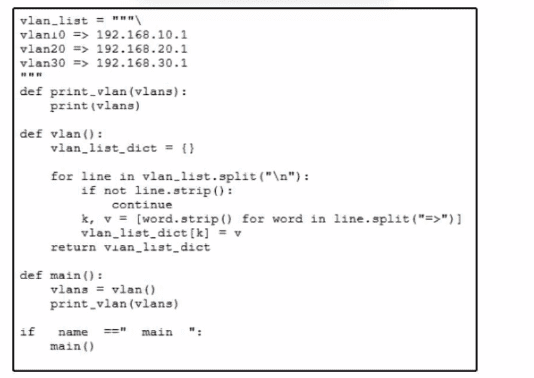
Refer to the exhibit A network engineer must use a Python script lo convert data received from a network device. Which type of data is printed to the console when the script runs?
Which two functions is an edge node responsible for? (Choose two.)
Which two new security capabilities are introduced by using a next-generation firewall at the Internet edge? (Choose two.)
What is used by vManage to interact with Cisco SD-WAN devices in the fabric?
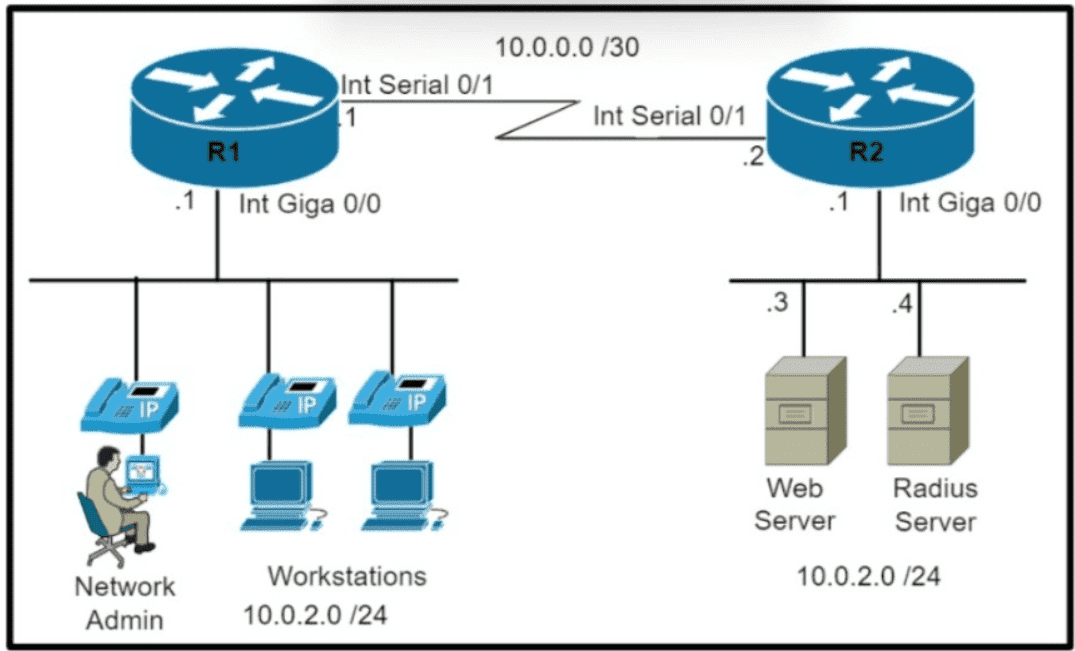
Refer to the exhibit Which command set is required on router R1 to allow the network administrator to authenticate via RADIUS'?

What are two of benefits of using VXLAN? (Choose two.)
What are two benefits of virtualizing the server with the use of VMs in a data center environment? (Choose two.)
Which function does a Cisco SD-Access extended node perform?
Why would an architect use an OSPF virtual link?



