Cisco 350-501 - Implementing and Operating Cisco Service Provider Network Core Technologies (350-501 SPCOR)
A network engineer is testing an automation platform that interacts with Cisco networking devices via NETCONF over SSH. In accordance with internal security requirements:
NETCONF sessions are permitted only from trusted sources in the 172.16.20.0/24 subnet.
CLI SSH access is permitted from any source.
Which configuration must the engineer apply on R1?
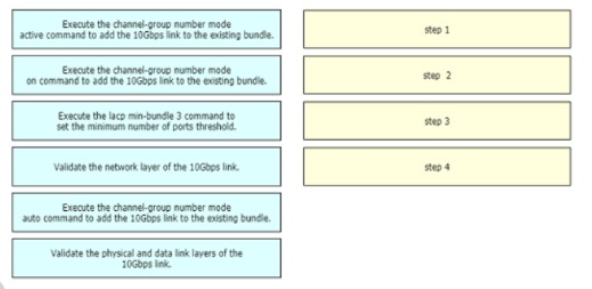
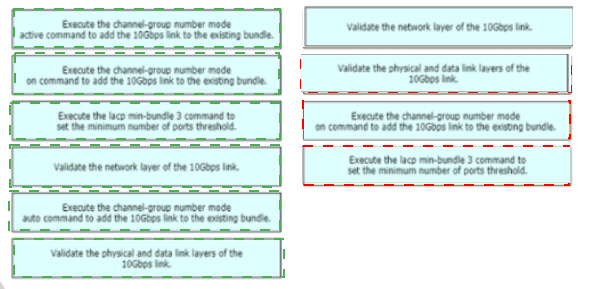
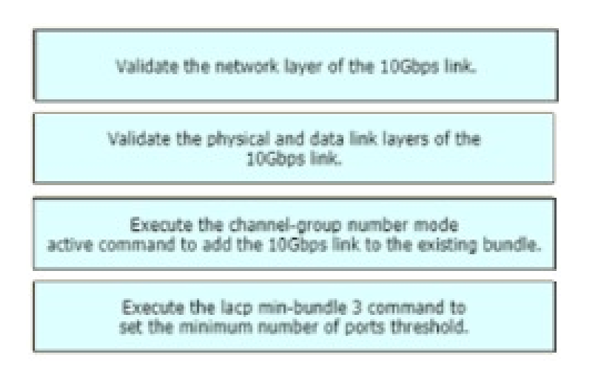
A network engineer is adding 10Gbps link to an existing 2X1Gbps LACP-based LAG to augment its capacity. Network standards require a bundle interface to be take out of service if one of its member links does down, and the new link must be added with minimal impact to the production network. Drag and drop the tasks that the engineer must perform from the left into the sequence on the right. Not all options are used.
A company needs to improve the use of the network resources that is used to deploy internet access service to customers on separate backbone and internet access network. Which two major design models should be used to configure MPLS L3VPNs and internet service in the same MPLS backbone? (Choose two.)
What are two characteristics of MPLS TE turrets? (Choose two)
Which role does the Adjacency-SID sub-TLV extension perform in the IS-IS routing protocol?
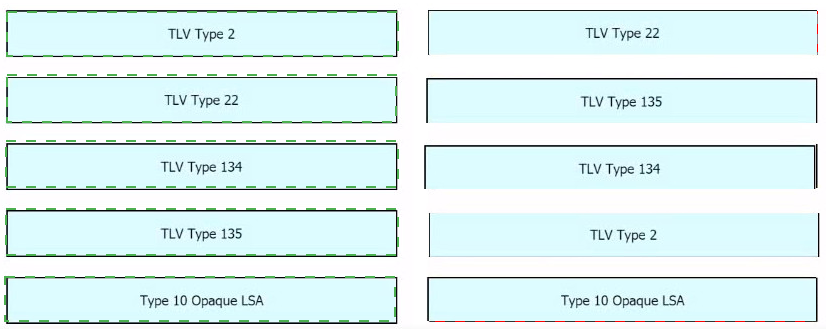
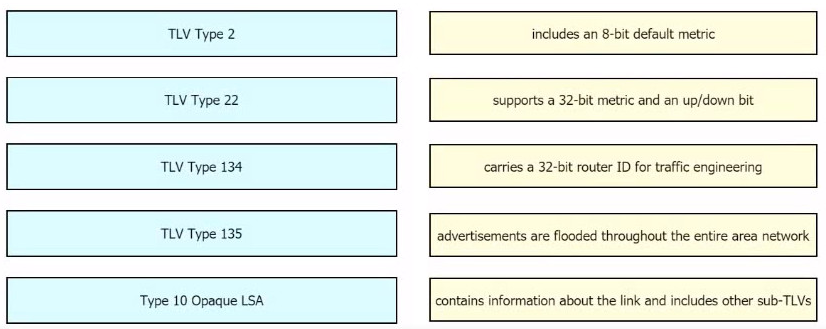
Drag and drop the OSPF and IS-IS Cisco MPLS TE extensions from the left to their functional descriptions on the right.
A network administrator must monitor network usage to provide optimal performance to the network end users when the network is under heavy load. The administrator asked the engineer to install a new server to receive SNMP traps at destination 192.168.1.2. Which configuration must the engineer apply so that all traps are sent to the new server?
Which MPLS design attribute can you use to provide Internet access to a major customer through a separate dedicated VPN?
What is the difference between SNMP and model-driven telemetry?
Refer to the exhibit:
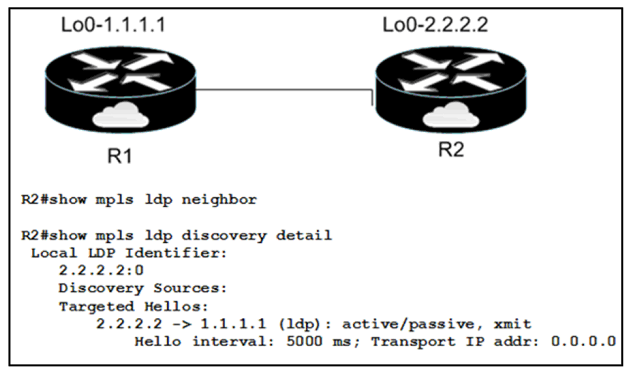
When implementing an LDP protocol, an engineer experienced an issue between two directly connected routers and noticed that no LDP neighbor exists for 1.1.1.1.
Which factor should be the reason for this situation?



 Application, table
Description automatically generated with medium confidence
Application, table
Description automatically generated with medium confidence