Cisco 350-501 - Implementing and Operating Cisco Service Provider Network Core Technologies (350-501 SPCOR)
Refer to the exhibit:
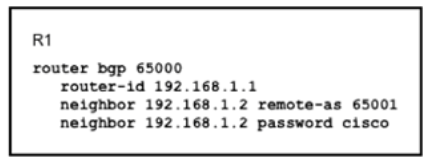
Router R1 and its peer R2 reside on the same subnet in the network, If does it make connections to R27
Refer to the exhibit:
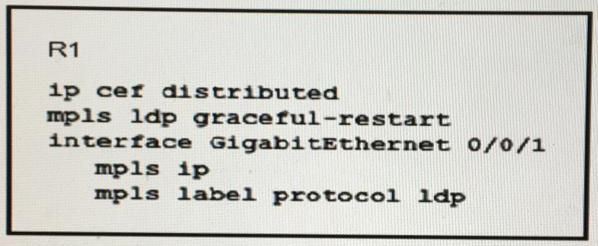
Which effect of this configuration is true?
The engineering team at a large ISP has been alerted a customer network is experiencing high traffic congestion. After a discussion between the ISP and technical personnel at the customer site, the team agrees that traffic to the customer network that exceeds a specific threshold will be dropped. Which task must the engineer perform on the network to implement traffic policing changes?
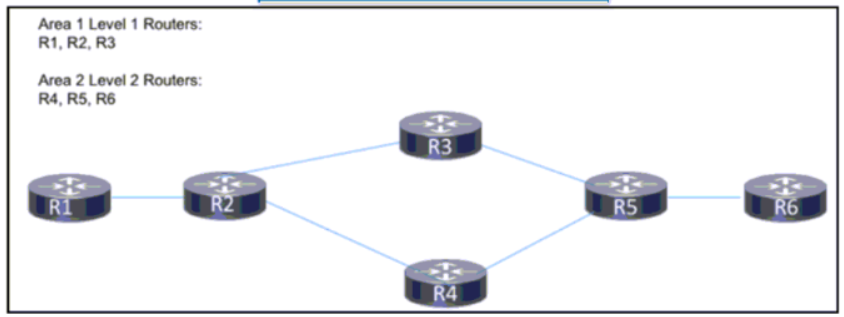
Refer to the exhibit A network engineer is in the process of implementing IS-IS Area 1 and Area 2 on this network to segregate traffic between different segments of the network The hosts in the two new areas must maintain the ability to communicate with one another In both directions. Which additional change must be applied?
Refer to the exhibit.
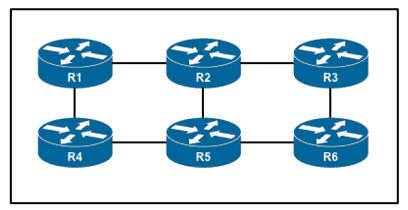
An engineer is configuring an administrative domain in the given multi-vendor environment with PIM-SM. Which feature must the engineer implement so that devices will dynamically learn the RP?
Exhibit:
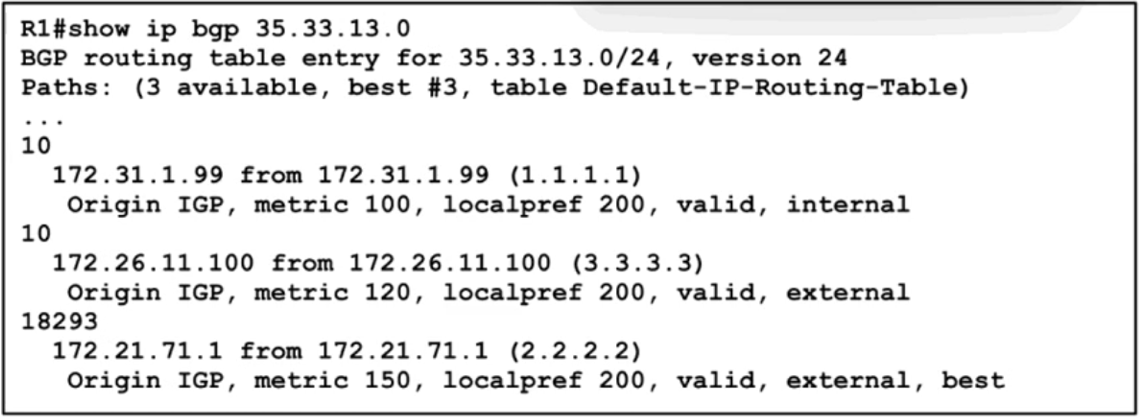
A network engineer must update the routing toward the web server with IP address 35.22.13.1. The primary path must be configured via the neighbor router with ID 1.1.1.1. However, local-preference configuration is not permitted on R1. Which task must the engineer perform on R1 to complete the implementation?
Refer to the exhibit:
What does this value mean when it is received in XML?
Refer to the exhibit:
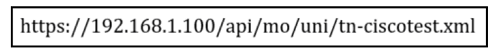
What is the URL used for with REST API?
Which type of attack is an application attack?
Refer to the exhibit:
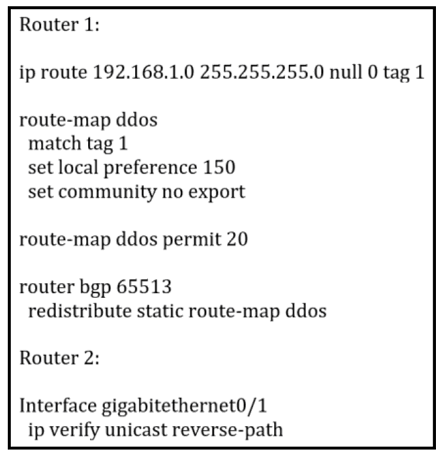
An engineer is preparing to implement data plane security configuration.
Which statement about this configuration is true?



