Cisco 350-501 - Implementing and Operating Cisco Service Provider Network Core Technologies (350-501 SPCOR)
How does model-driven telemetry use YANG?
A network engineer is configuring Flexible NetFlow and enters these commands
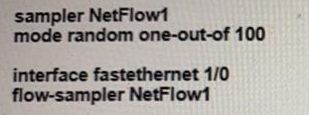
What are two results of implementing this feature instead of traditional NetFlow? (Choose two.)
Refer to the exhibit.
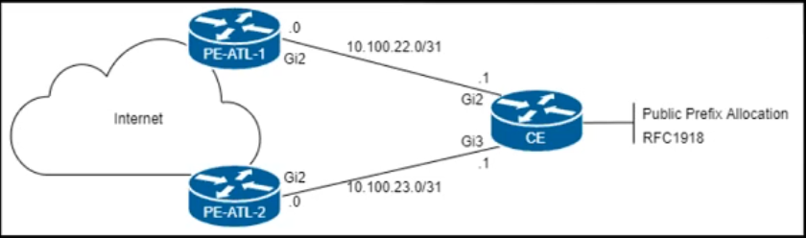
The CE router is peering with both PE routers and advertising a public prefix to the internet. Routing to and from this prefix will be asymmetric under certain network conditions, but packets must not be discarded. Which configuration must an engineer apply to the two PE routers so that they validate reverse packet forwarding for packets entering their Gi2 interfaces and drop traffic from the RFC1918 space?
A service provider requires continuous real-time network monitoring to provide reliable SLAs to its customers. To satisfy this requirement, a network administrator is implementing gRPC dial out on an ASR with TLS. Receiver 192.168.10.2 will be assigned one of the subscriptions, and it will manage the ASR. Which configuration must the engineer apply to the router as part of the configuration process?
When Cisco lOS XE REST API uses HTTP request methods what is the purpose of a PUT request?
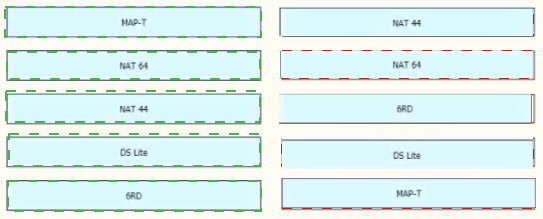
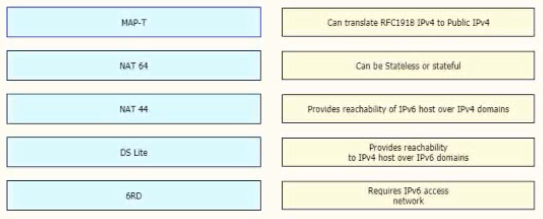
Drag and drop the functionalities from the left onto the target fields on the right.
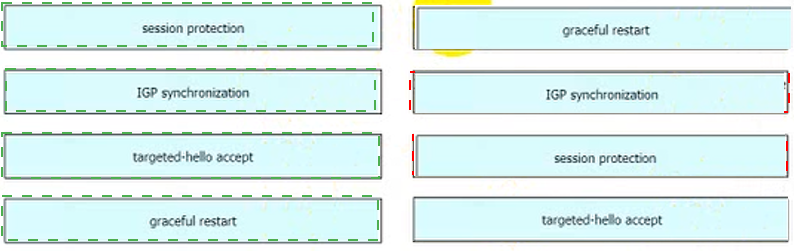
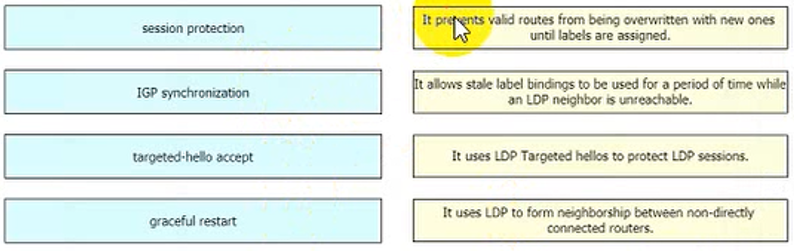
Drag and drop the LDP features from the left onto their usages on the right.
Refer to the exhibit:

An engineer is preparing to implement link aggregation configuration.
Which statement al about this configuration is true?
Refer to the exhibit.
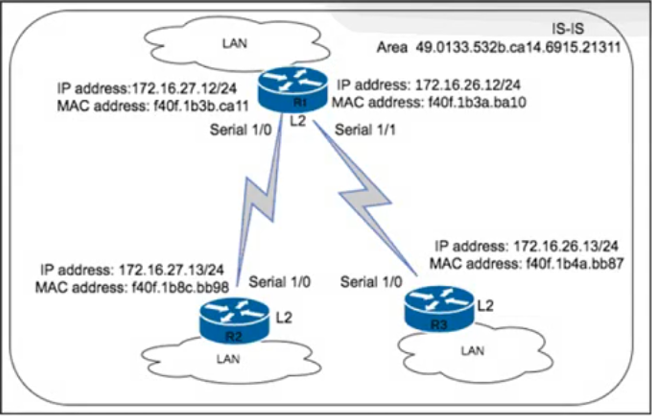
An engineer with an employee 10:4350:47:853 is implementing IS-IS as the new routing protocol in the network. All routers in the network operate as Level 2 routers in the same private autonomous system, and the three branches are connected via dark fibre. The engineer has already implemented IS-IS on router R1 with NET address 49.0133.532b.ca14.6915.21311.F40F.1B3a.ba10.00. Which IS-IS NET address configuration must be implemented on R3 to establish IS-IS connectivity?
While implementing TTL security, you issue the PE(config-router-af)#neighbor 2.2.2.2 ttl-security hops 2 command.
After you issue this command, which BGP packets does the PE accept?