Cisco 350-701 - Implementing and Operating Cisco Security Core Technologies (SCOR 350-701)
Which Cisco security solution protects remote users against phishing attacks when they are not connected to
the VPN?
Which technology reduces data loss by identifying sensitive information stored in public computing
environments?
Which feature within Cisco Umbrella allows for the ability to inspect secure HTTP traffic?
A Cisco Secure Cloud Analytics administrator is setting up a private network monitor sensor to monitor an on-premises environment. Which two pieces of information from the sensor are used to link to the Secure Cloud Analytics portal? (Choose two.)
Which feature within Cisco ISE verifies the compliance of an endpoint before providing access to the
network?
An organization configures Cisco Umbrella to be used for its DNS services. The organization must be able to block traffic based on the subnet that the endpoint is on but it sees only the requests from its public IP address instead of each internal IP address. What must be done to resolve this issue?
An engineer needs a cloud solution that will monitor traffic, create incidents based on events, and integrate with
other cloud solutions via an API. Which solution should be used to accomplish this goal?
Refer to the exhibit.
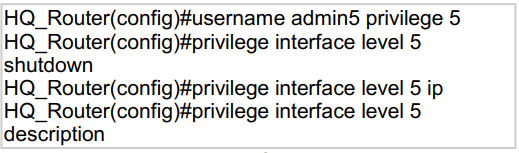
A network administrator configures command authorization for the admin5 user. What is the admin5 user able to do on HQ_Router after this configuration?
Where are individual sites specified to be blacklisted in Cisco Umbrella?
Which two probes are configured to gather attributes of connected endpoints using Cisco Identity Services
Engine? (Choose two)
What is a difference between GETVPN and IPsec?
What is a difference between a zone-based firewall and a Cisco Adaptive Security Appliance firewall?
Which function is performed by certificate authorities but is a limitation of registration authorities?
What are two security benefits of an MDM deployment? (Choose two.)
A Cisco ESA administrator has been tasked with configuring the Cisco ESA to ensure there are no viruses before quarantined emails are delivered. In addition, delivery of mail from known bad mail servers must be prevented. Which two actions must be taken in order to meet these requirements? (Choose two)



