Cisco 350-701 - Implementing and Operating Cisco Security Core Technologies (SCOR 350-701)
An engineer is trying to decide between using L2TP or GRE over IPsec for their site-to-site VPN implementation. What must be un solution?
Which Cisco solution provides a comprehensive view of Internet domains. IP addresses, and autonomous systems to help pinpoint attackers and malicious infrastructures?
Which Cisco ISE service checks the compliance of endpoints before allowing the endpoints to connect to
the network?
What does the Cloudlock Apps Firewall do to mitigate security concerns from an application perspective?
A security engineer must create a policy based on the reputation verdict of a file from a Cisco Secure Email Gateway. The file with an undetermined verdict must be dropped. Which action must the security engineer take to meet the requirement?
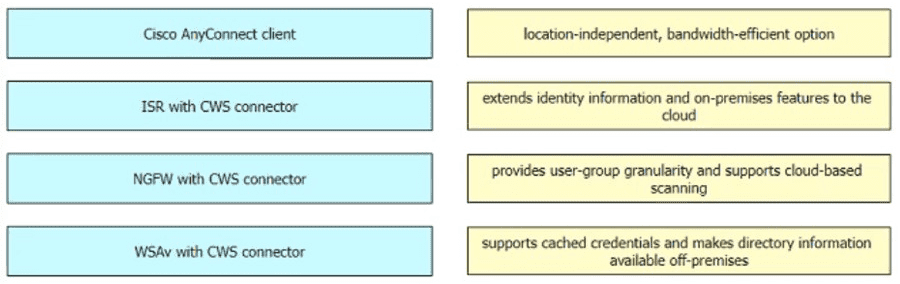
Drag and drop the Cisco CWS redirection options from the left onto the capabilities on the right.
Which solution is made from a collection of secure development practices and guidelines that developers must follow to build secure applications?
Which compliance status is shown when a configured posture policy requirement is not met?
An engineer is configuring 802.1X authentication on Cisco switches in the network and is using CoA as a mechanism. Which port on the firewall must be opened to allow the CoA traffic to traverse the network?
What is a benefit of using Cisco AVC (Application Visibility and Control) for application control?
When using Cisco AMP for Networks which feature copies a file to the Cisco AMP cloud for analysis?
Refer to the exhibit.
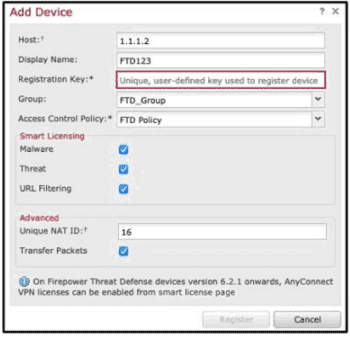
An administrator is adding a new Cisco FTD device to their network and wants to manage it with Cisco FMC.
The Cisco FTD is not behind a NAT device. Which command is needed to enable this on the Cisco FTD?
What is a functional difference between a Cisco ASA and a Cisco IOS router with Zone-based policy firewall?
A Cisco Firepower administrator needs to configure a rule to allow a new application that has never been seen
on the network. Which two actions should be selected to allow the traffic to pass without inspection? (Choose
two)
What is the benefit of installing Cisco AMP for Endpoints on a network?




