Cisco 350-701 - Implementing and Operating Cisco Security Core Technologies (SCOR 350-701)
Which feature is leveraged by advanced antimalware capabilities to be an effective endpomt protection platform?
Which two services must remain as on-premises equipment when a hybrid email solution is deployed? (Choose two)
Which two prevention techniques are used to mitigate SQL injection attacks? (Choose two)
Which type of DNS abuse exchanges data between two computers even when there is no direct connection?
Which benefit does endpoint security provide the overall security posture of an organization?
Which type of attack is MFA an effective deterrent for?
Which term describes when the Cisco Secure Firewall downloads threat intelligence updates from Cisco Tables?
A large organization wants to deploy a security appliance in the public cloud to form a site-to-site VPN
and link the public cloud environment to the private cloud in the headquarters data center. Which Cisco
security appliance meets these requirements?
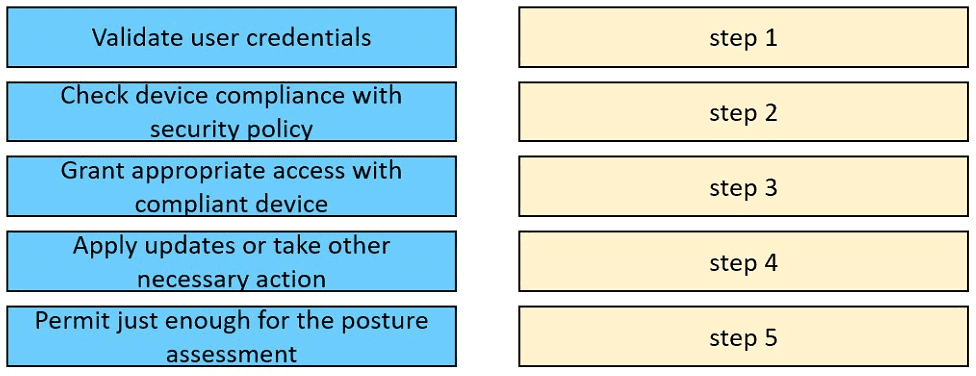
Drag and drop the posture assessment flow actions from the left into a sequence on the right.
Which two protocols must be configured to authenticate end users to the Web Security Appliance? (Choose two.)
What is the purpose of the My Devices Portal in a Cisco ISE environment?
Which open source tool does Cisco use to create graphical visualizations of network telemetry on Cisco IOS XE devices?
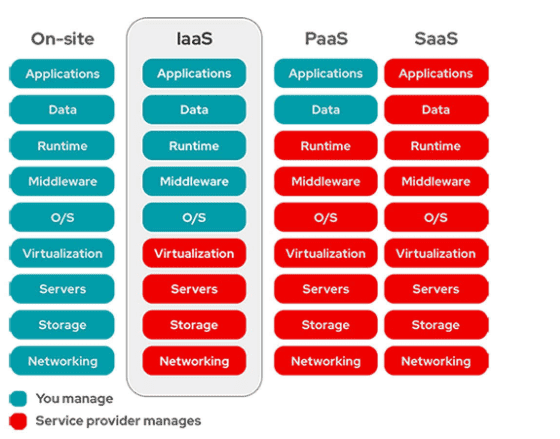
In which cloud services model is the tenant responsible for virtual machine OS patching?
Which Cisco security solution gives the most complete view of the relationships and evolution of Internet domains IPs, and flies, and helps to pinpoint attackers' infrastructures and predict future threat?
An organization is implementing URL blocking using Cisco Umbrella. The users are able to go to some sites but other sites are not accessible due to an error. Why is the error occurring?