Cisco 350-701 - Implementing and Operating Cisco Security Core Technologies (SCOR 350-701)
Which two features of Cisco DNA Center are used in a Software Defined Network solution? (Choose two)
Which solution allows an administrator to provision, monitor, and secure mobile devices on Windows and Mac computers from a centralized dashboard?
Which two protocols must be configured to authenticate end users to the Cisco WSA? (Choose two.)
An engineer needs to add protection for data in transit and have headers in the email message Which configuration is needed to accomplish this goal?
An engineer must modify a policy to block specific addresses using Cisco Umbrella. The policy is created already and is actively used by devices, using many of the default policy elements.
What else must be done to accomplish this task?
How does Cisco Stealthwatch Cloud provide security for cloud environments?
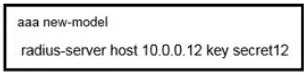
Refer to the exhibit. What is the result of using this authentication protocol in the configuration?
Refer to the exhibit.
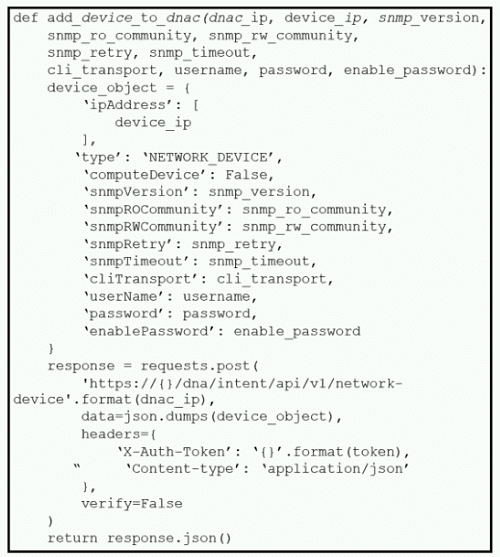
What is the result of this Python script of the Cisco DNA Center API?
An engineer is deploying Cisco Advanced Malware Protection (AMP) for Endpoints and wants to create a policy that prevents users from executing file named abc424952615.exe without quarantining that file What type of Outbreak Control list must the SHA.-256 hash value for the file be added to in order to accomplish this?
What are two functions of secret key cryptography? (Choose two)
Which technology is used to improve web traffic performance by proxy caching?
Based on the NIST 800-145 guide, which cloud architecture may be owned, managed, and operated by one or more of the organizations in the community, a third party, or some combination of them, and it may exist on or off premises?
An engineer is deploying a Cisco Secure Email Gateway and must configure a sender group that decides which mail policy will process the mail. The configuration must accept incoming mails and relay the outgoing mails from the internal server. Which component must be configured to accept the connection to the listener and meet these requirements on a Cisco Secure Email Gateway?
What is the term for when an endpoint is associated to a provisioning WLAN that is shared with guest
access, and the same guest portal is used as the BYOD portal?
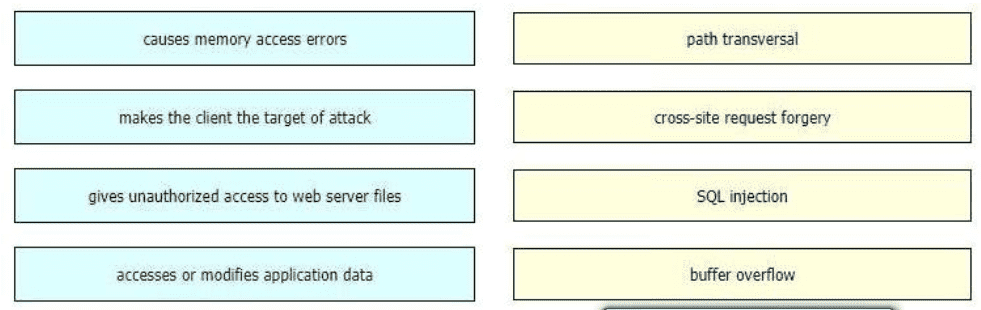
Drag and drop the exploits from the left onto the type of security vulnerability on the right.