Cisco 350-701 - Implementing and Operating Cisco Security Core Technologies (SCOR 350-701)
What Cisco command shows you the status of an 802.1X connection on interface gi0/1?
Which Cisco security solution determines if an endpoint has the latest OS updates and patches installed on the system?
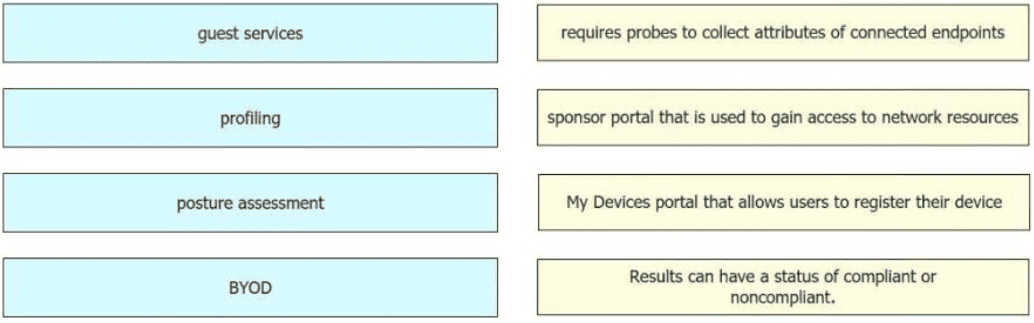
Drag and drop the concepts from the left onto the correct descriptions on the right
What is a characteristic of Cisco ASA Netflow v9 Secure Event Logging?
Which endpoint solution protects a user from a phishing attack?
An administrator enables Cisco Threat Intelligence Director on a Cisco FMC. Which process uses STIX and allows uploads and downloads of block lists?
A Cisco ESA network administrator has been tasked to use a newly installed service to help create policy based on the reputation verdict. During testing, it is discovered that the Cisco ESA is not dropping files that have an undetermined verdict. What is causing this issue?
Which license is required for Cisco Security Intelligence to work on the Cisco Next Generation Intrusion
Prevention System?
An engineer must implement a file transfer solution between a company's data center and branches. The company has numerous servers hosted in a hybrid cloud implementation. The file transfer protocol must support authentication, protect the data against unauthorized access, and ensure that users cannot list directories or remove files remotely. Which protocol must be used?
Which Cisco DNA Center Intent API action is used to retrieve the number of devices known to a DNA Center?
Which threat intelligence standard contains malware hashes?
An engineer needs a solution for TACACS+ authentication and authorization for device administration.
The engineer also wants to enhance wired and wireless network security by requiring users and endpoints to
use 802.1X, MAB, or WebAuth. Which product meets all of these requirements?
Why is it important to have logical security controls on endpoints even though the users are trained to spot security threats and the network devices already help prevent them?
What is a prerequisite when integrating a Cisco ISE server and an AD domain?
How does Cisco Umbrella archive logs to an enterprise owned storage?




