Cisco 350-701 - Implementing and Operating Cisco Security Core Technologies (SCOR 350-701)
Refer to the exhibit.
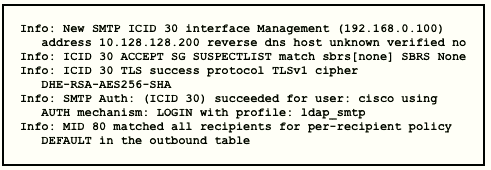
Which type of authentication is in use?
Which cryptographic process provides origin confidentiality, integrity, and origin authentication for packets?
Which two criteria must a certificate meet before the WSA uses it to decrypt application traffic? (Choose two.)
What is a difference between DMVPN and sVTI?
How does Cisco Umbrella protect clients when they operate outside of the corporate network?
Which Secure Email Gateway implementation method segregates inbound and outbound email?
Refer to the exhibit.
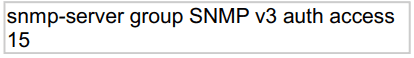
What does the number 15 represent in this configuration?
What is a feature of container orchestration?
Which type of data exfiltration technique encodes data in outbound DNS requests to specific servers
and can be stopped by Cisco Umbrella?
What is a language format designed to exchange threat intelligence that can be transported over the TAXII
protocol?
A customer has various external HTTP resources available including Intranet. Extranet, and Internet, with a proxy configuration running in explicit mode Which method allows the client desktop browsers to be configured to select when to connect direct or when to use the proxy?
An engineer is configuring IPsec VPN and needs an authentication protocol that is reliable and supports ACK
and sequence. Which protocol accomplishes this goal?
Refer to the exhibit.
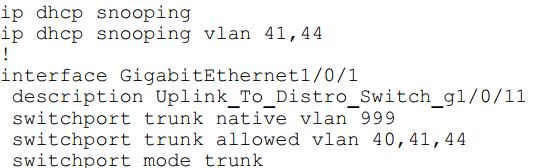
An organization is using DHCP Snooping within their network. A user on VLAN 41 on a new switch is
complaining that an IP address is not being obtained. Which command should be configured on the switch
interface in order to provide the user with network connectivity?
What are two characteristics of Cisco Catalyst Center APIs? (Choose two.)
What is an advantage of using a next-generation firewall compared to a traditional firewall?



