Cisco 350-701 - Implementing and Operating Cisco Security Core Technologies (SCOR 350-701)
An engineer enabled SSL decryption for Cisco Umbrella intelligent proxy and needs to ensure that traffic is inspected without alerting end-users. Which action accomplishes this goal?
A small organization needs to reduce the VPN bandwidth load on their headend Cisco ASA in order to
ensure that bandwidth is available for VPN users needing access to corporate resources on the10.0.0.0/24 local HQ network. How is this accomplished without adding additional devices to the
network?
Which command is used to log all events to a destination colector 209.165.201.107?
What is the purpose of joining Cisco WSAs to an appliance group?
What are two benefits of using Cisco Duo as an MFA solution? (Choose two.)
Which open standard creates a framework for sharing threat intelligence in a machine-digestible format?
Which two fields are defined in the NetFlow flow? (Choose two)
Which Cisco security solution secures public, private, hybrid, and community clouds?
Which two Cisco ISE components must be configured for BYOD? (Choose two.)
Which Cisco network security device supports contextual awareness?
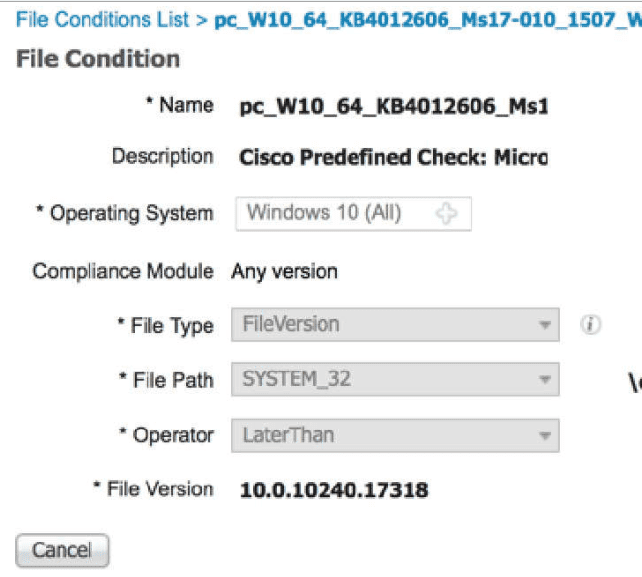
Which Cisco platform ensures that machines that connect to organizational networks have the recommended
antivirus definitions and patches to help prevent an organizational malware outbreak?
What is managed by Cisco Security Manager?
What is the purpose of CA in a PKI?
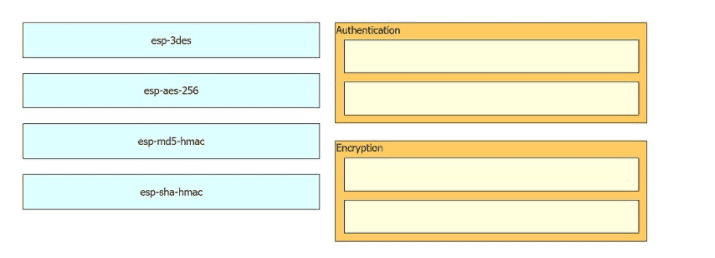
Drag and drop the cryptographic algorithms for IPsec from the left onto the cryptographic processes on the right.
A network administrator needs a solution to match traffic and allow or deny the traffic based on the type of application, not just the source or destination address and port used. Which kind of security product must the network administrator implement to meet this requirement?