Cisco 350-901 - Developing Applications using Cisco Core Platforms and APIs (DEVCOR)
Refer to the exhibit.
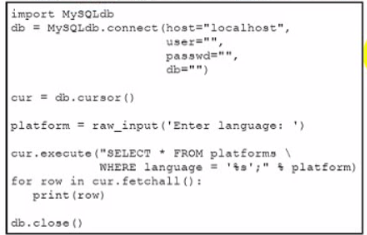
Which action should be performed to avoid an SQL injection attack?
Refer to the exhibit.
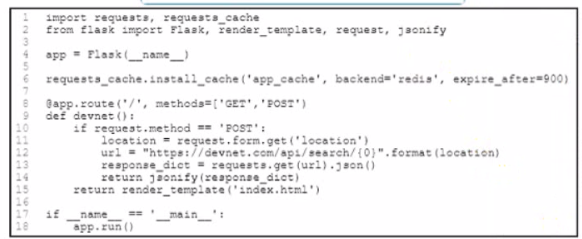
An application has been developed to serve the users in an enterprise After HTTP cache controls are implemented m the application users report that they receive state data when they refresh the page Without removing HTTP cache controls, which change ensures that the users get current data when refreshing the page'
Refer to the exhibit.
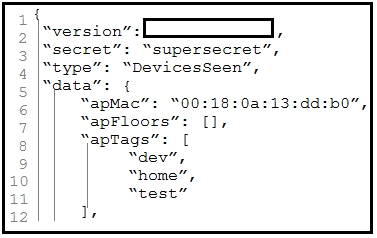
Which parameter is missing from the JSON response to confirm the API version that is
used?
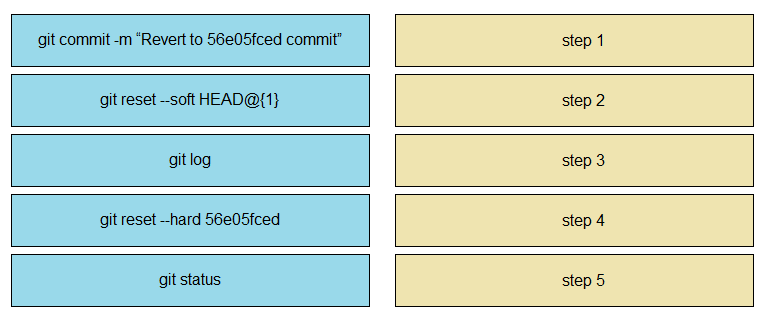
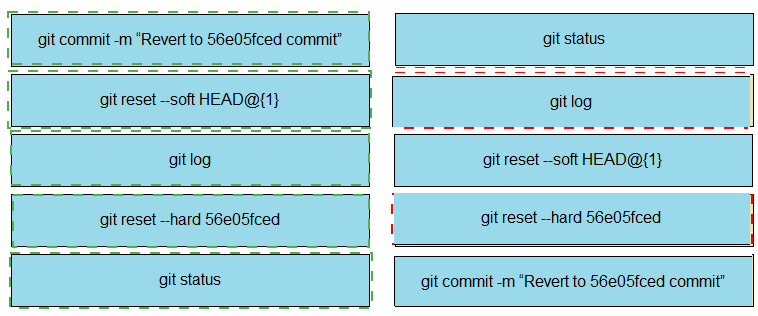
Drag and drop the steps from the left into the correct sequence on the right to describe how to use Git to maintain the current HEAD and revert back to a previous commit, while undoing all intermediate commits.
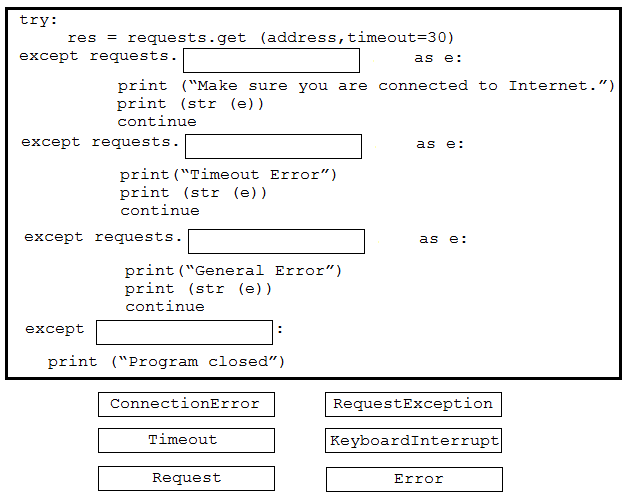
A developer is creating a Python script to catch errors using REST API calls and to aid in debugging. Drag and drop the code from the bottom onto the box where the code is missing to implement control flow for REST API errors. Not all options are used.
Refer to the exhibit.
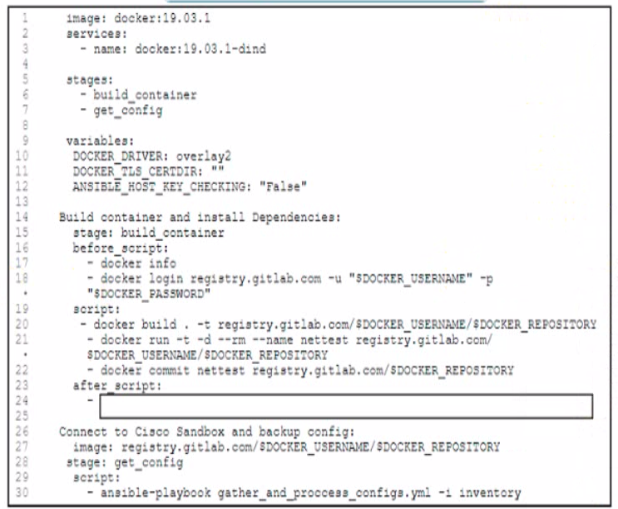
A)

B)

C)

D)

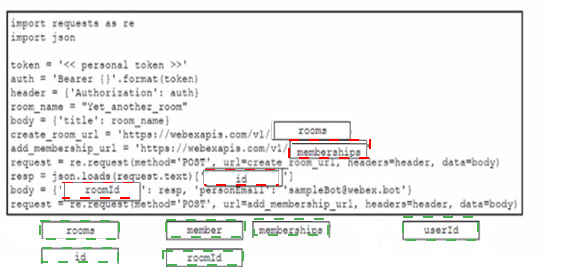
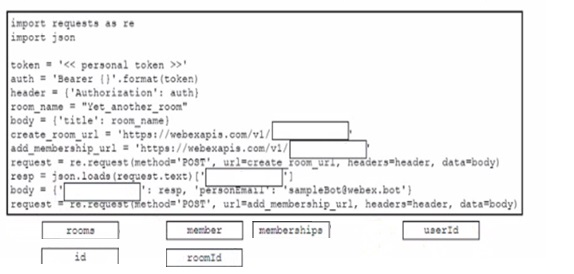
Drag and drop the code from the bottom onto the box where the code is missing to create a new Cisco Webex space and attach a previously configured bot named 'sampleBot'. Not all options are used.
{'lat': 37.4180951010362, 'lng': -122.098531723022, 'address': '', 'serial': 'Q2HP-F5K5-F98Q',
'mac': '88:15:44:ea:f5:bf', 'lanIp': '10.10.10.15',
'url': 'https://n149.meraki.com/DevNet-Sandbox/n/EFZDavc/manage/nodes/new_list/78214561218351',
'model': 'MS220-8P', 'switchProfileId': None, 'firmware': 'switch-11-31', 'floorPlanId': None}
Refer to the exhibit. A developer needs to find the geographical coordinates of a device on the network L_397561557481105433 using a Python script to query the Meraki API. After running response = requests.get() against the Meraki API, the value of response.text is shown in the exhibit.
What Python code is needed to retrieve the longitude and latitude coordinates of the device?
In the three-legged OAuth2 authorization workflow, which entity grants access to a protected resource?
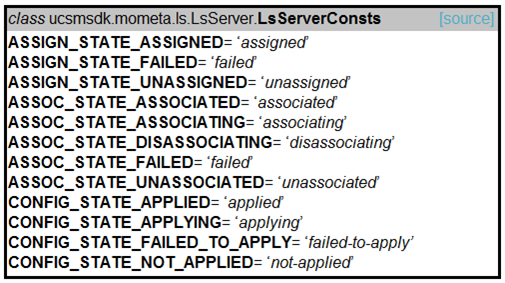
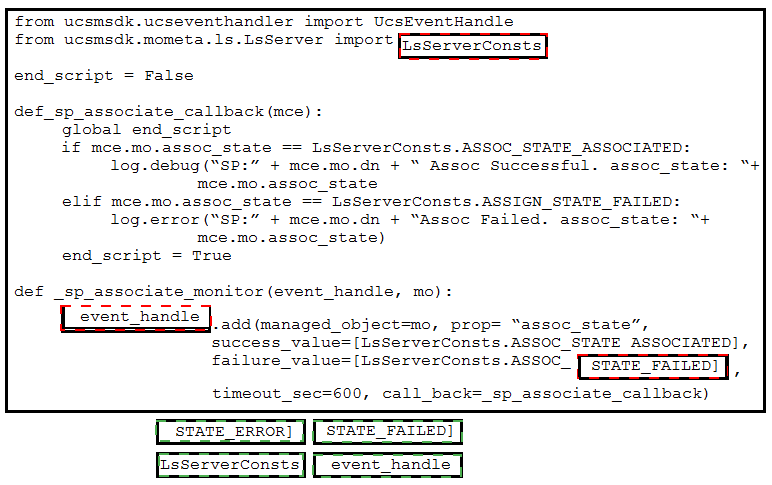
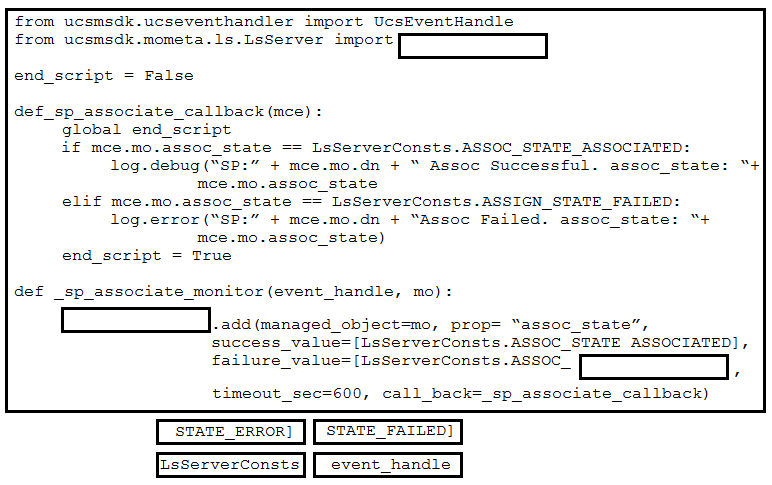
Refer to the exhibit. Drag and drop the code snippets from the bottom onto the blanks in the code to provision a new UCS server. Not all options are used.



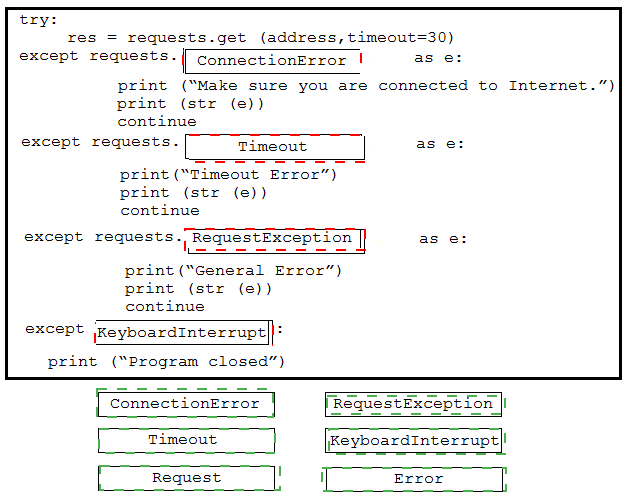
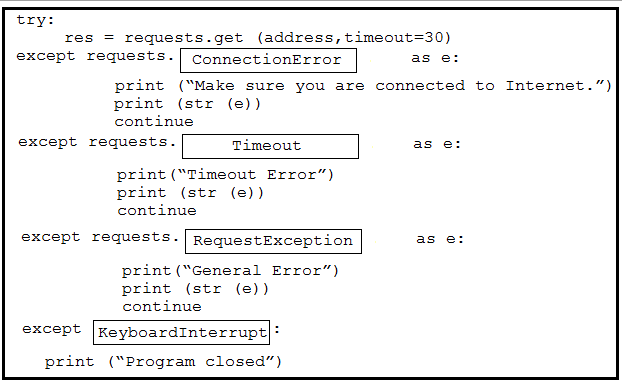 Graphical user interface, text, application
Description automatically generated
Graphical user interface, text, application
Description automatically generated