Cisco 350-901 - Developing Applications using Cisco Core Platforms and APIs (DEVCOR)
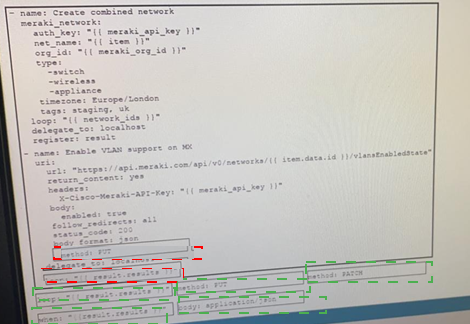
Drag and drop the code from the bottom onto the box where the code is missing on the Ansible task to enable a VLAN on a Meraki MX Device, Not all options are used.
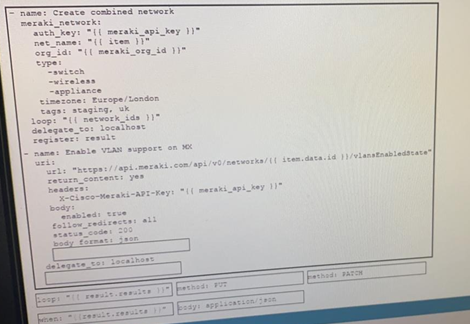
Refer to the exhibit.
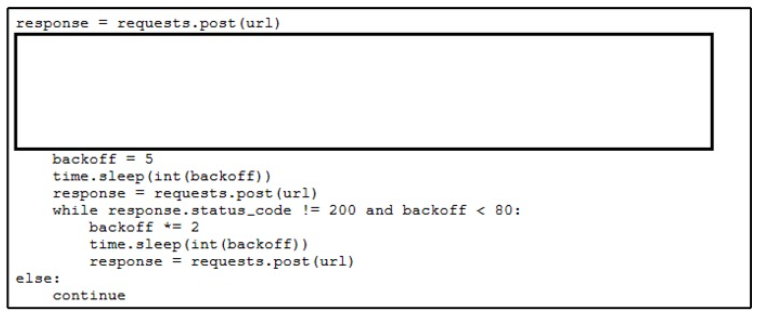
An engineer needs to implement REST API error handling when a timeout or rate limit scenario is present. Which code snippet must be placed into the blank in the code to complete the API request?
A)
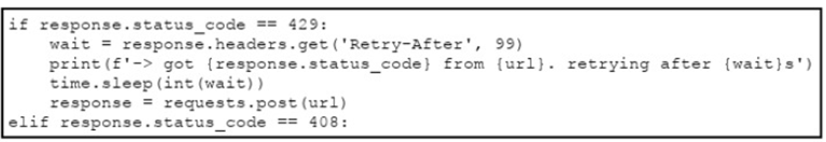
B)
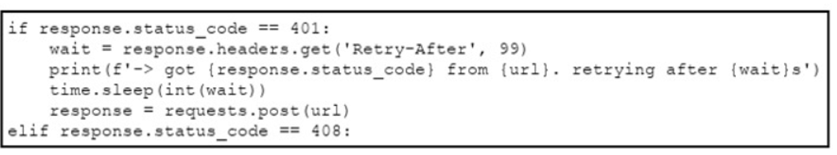
C)
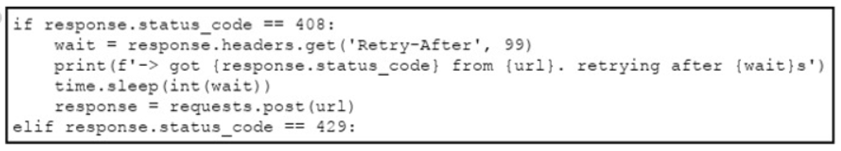
D)
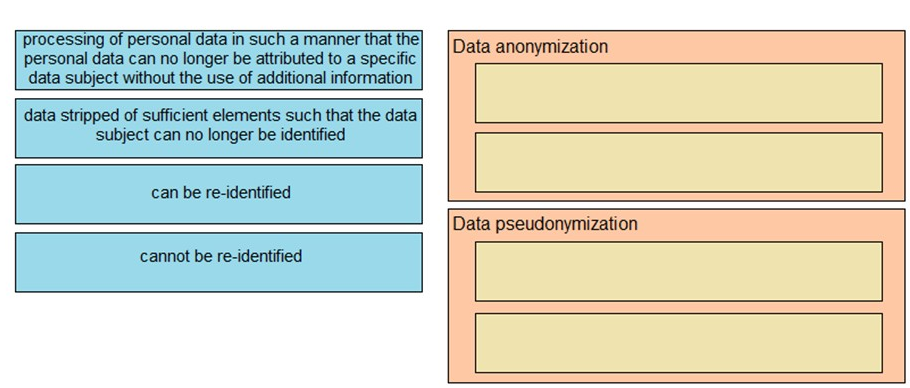
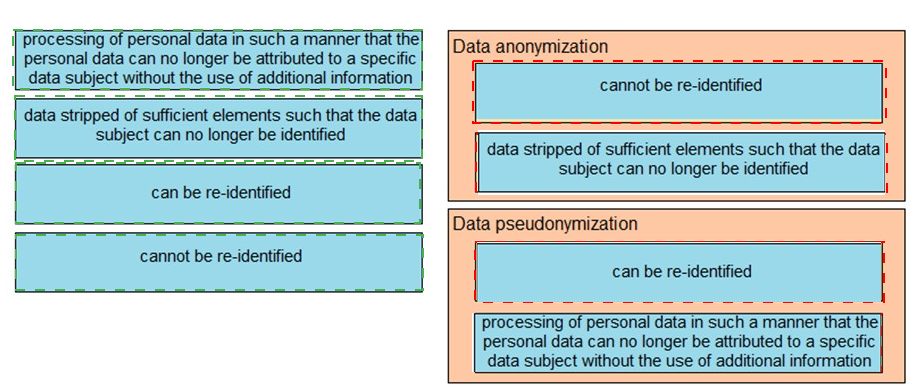
Drag and drop the characteristics from the left onto the correct data processing techniques on the right, in the context of GDPR.
Which kind of API that is used with Cisco DNA Center provisions SSIDs, QoS policies, and update software versions on switches?
Refer to the exhibit.

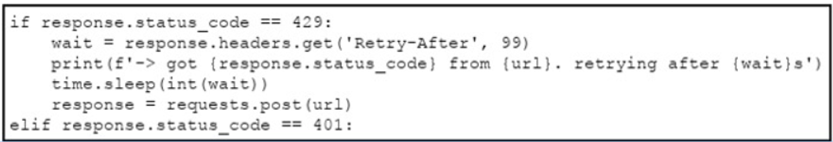
A network engineer needs to handle API errors in their requests when users do not have permission to access the resource, even if they are authenticated and authorized. Which line of code needs to be placed on the snippet where the code is missing to handle these API errors?
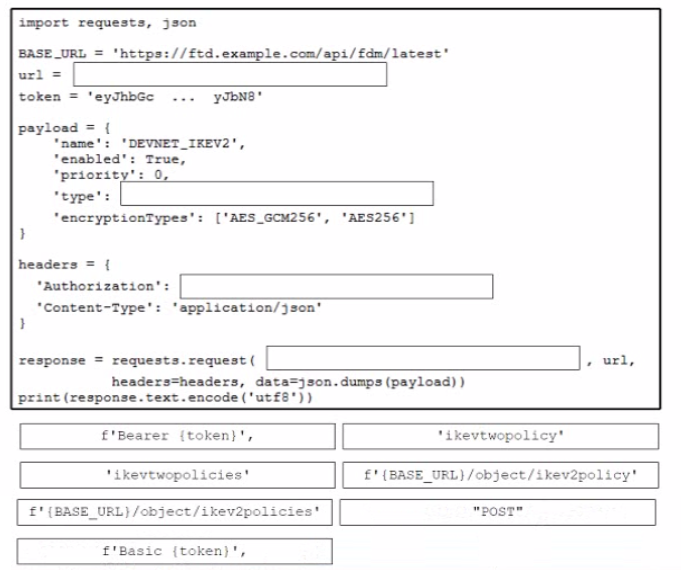
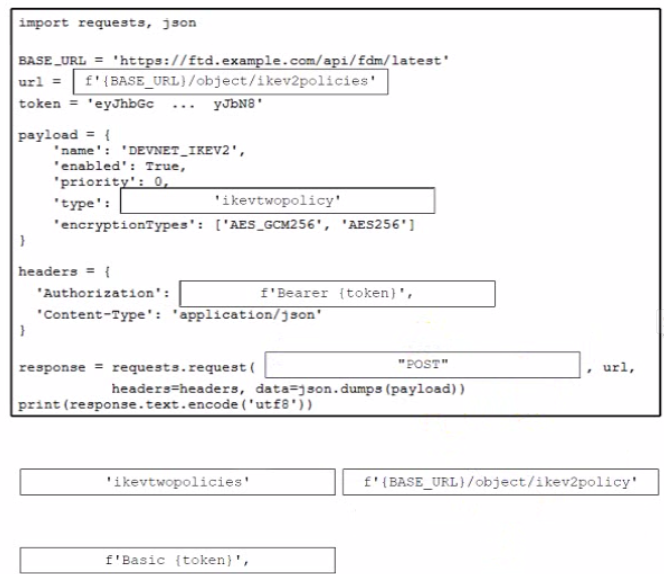
Drag and drop the code from the bottom onto the box where the code is missing to create a new IKEv2 policy Not all options are used
A developer corrects an application bug with ID buglDa98416945110x and then installs it on a Cisco Catalyst 9300 series switch. Which command will enable the application called myapp?
Refer to the exhibit.
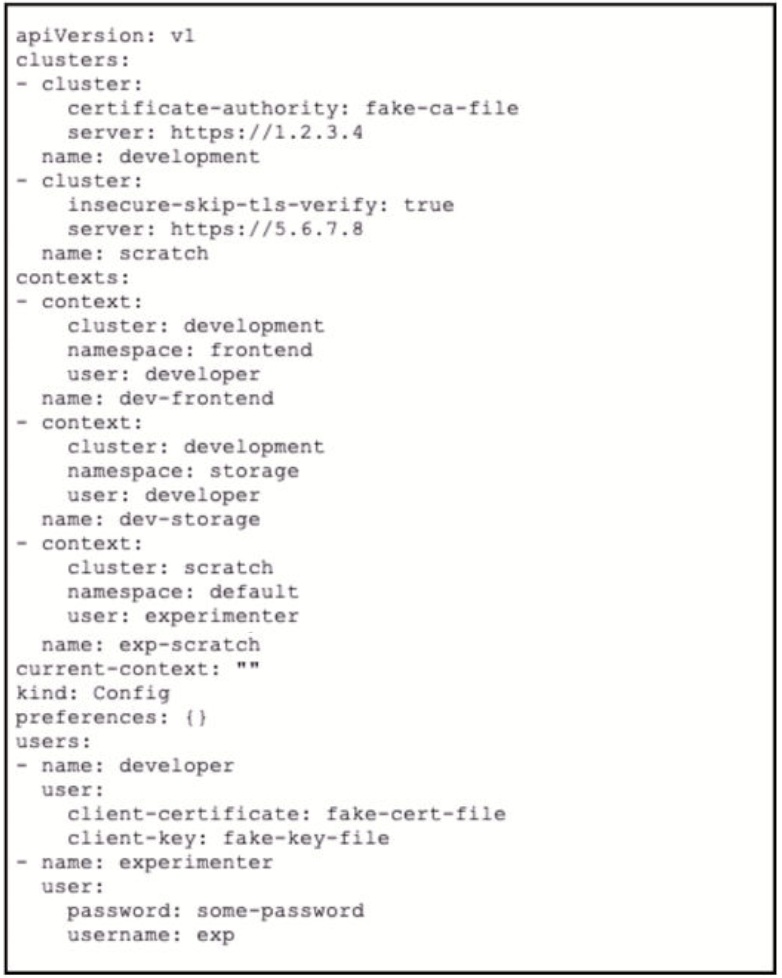
A kubeconfig file to manage access to Kubernetes clusters is shown. How many Kubernetes clusters are defined in the
file, and which cluster FS accessed using username/password authentication rather than using a certificate?
An organization manages a large cloud-deployed application that employs a microservices architecture. No notable issues occur with downtime because the services of this application are redundantly deployed over three or more data center regions. However, several times a week reports are received about application slowness. The container orchestration logs show faults in a variety of containers that cause them to fail and then spin up brand new.
Which action must be taken to improve the resiliency design of the application while maintaining current scale?
What is submitted when an SSL certificate is requested?




 C:\Users\wk\Desktop\mudassar\Untitled.png
C:\Users\wk\Desktop\mudassar\Untitled.png