Cisco 350-901 - Developing Applications using Cisco Core Platforms and APIs (DEVCOR)
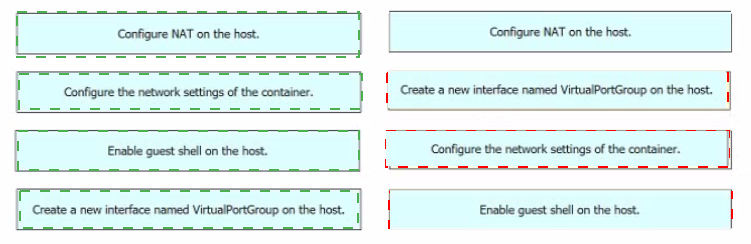
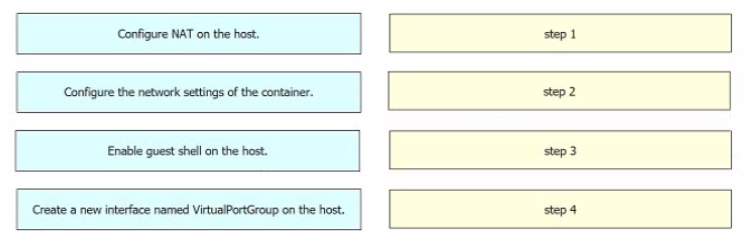
Drag and drop the steps from the left into the order on the right to ensure that an application requiring communication to the external network is hosted on a Cisco Catalyst 9000 switch.
An application is developed in order to communicate with Cisco Webex. For reporting, the application must retrieve all the messages sent to a Cisco Webex room on a monthly basis.
Which action calls /v1/messages directly?
An Etag header is included in the HTTP response for an API resource. What are two benefits of using the value of the Etag for future interactions involving the same API resource? (Choose two.)
Refer to the exhibit , The command docker build -tag=friendlyhello . is run to build a docker image from the given Dockerfile,
requirements,txt, and app.py, Then the command docker run -p 4000:80 friendlyhello is executed to run the application. Which URL is entered in the web browser to see the content served by the application?
Refer to the exhibit.
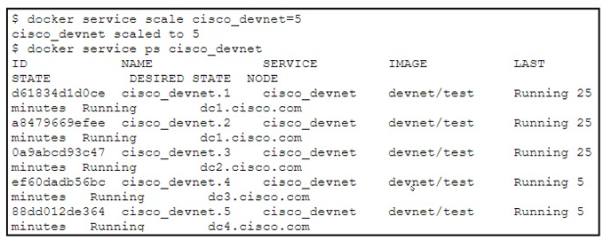
A developer runs the docker service scale command to increase the number of replicas for the cisco_devnet service. The swarm cluster is using a private IP address subnet. The service has these design requirements:
It must be hosted behind a virtual IP address that is reachable from the Internet.
For security reasons, the Docker swarm cluster subnet must not be reachable from the Internet.
Which design approach is used to fulfill the requirements?
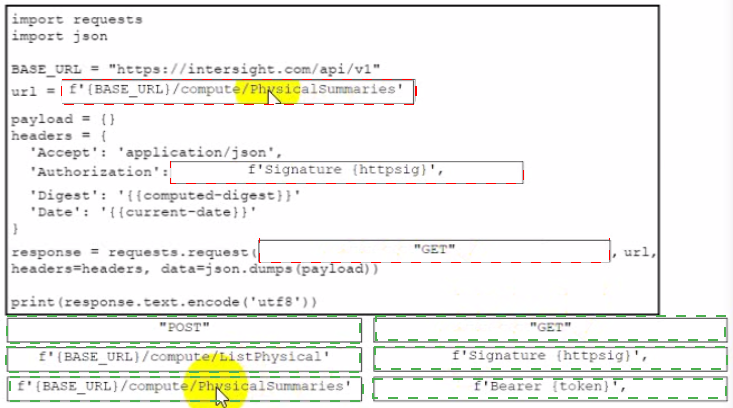
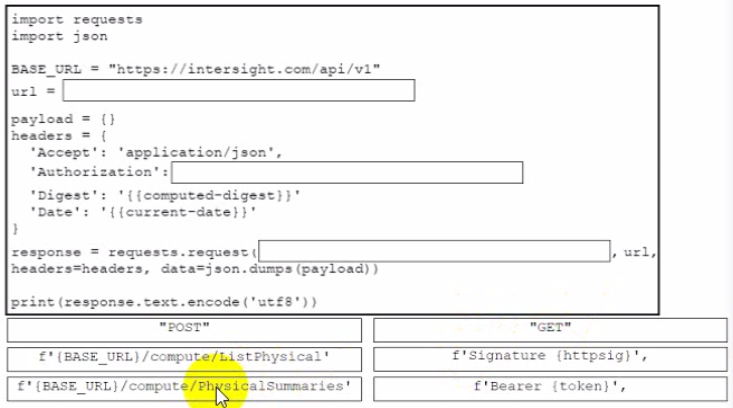
Drag and drop the code from the bottom onto the box where the code is missing to retrieve a summary of physical compute resources. The collected information about the compute resources will be presented in a dashboard to be developed for device monitoring purposes. Not all snippets are used.
Refer to the exhibit.
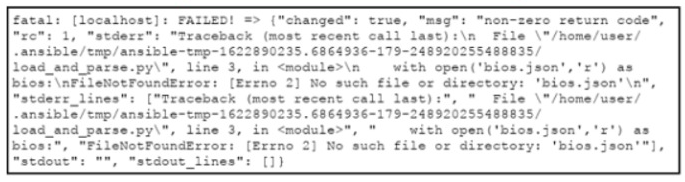
An engineer creates an application that leverages the Ansible framework to provision CPE endpoints that have configuration changes. The application contains an Ansible playbook named provision_cpes.yml that uses the ansible.builtin.script Ansible module to execute these two Python scripts:
•gather and_create.py. which creates a JSON file named bios.json that contains the CPE models and their respective IOS file information
•load and parse.py. which loads the file data and parses it for later consumption
After several successful runs, the application fails. During a review of the Ansible execution logs, the engineer discovers an error output that indicates that one of the stages failed. What is the cause of this issue?
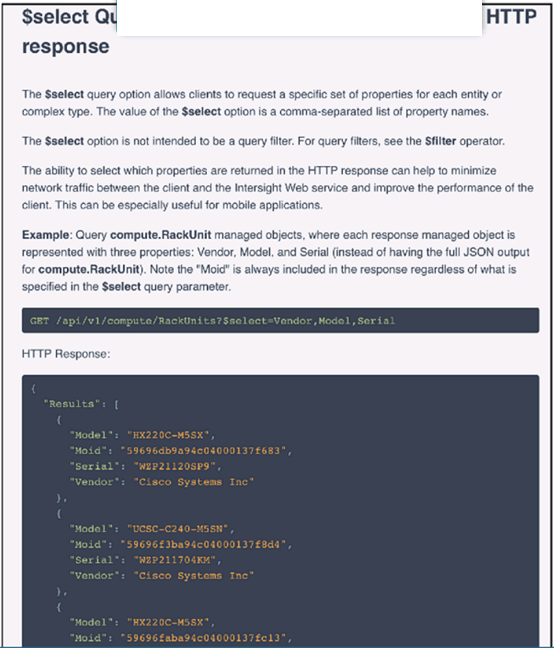
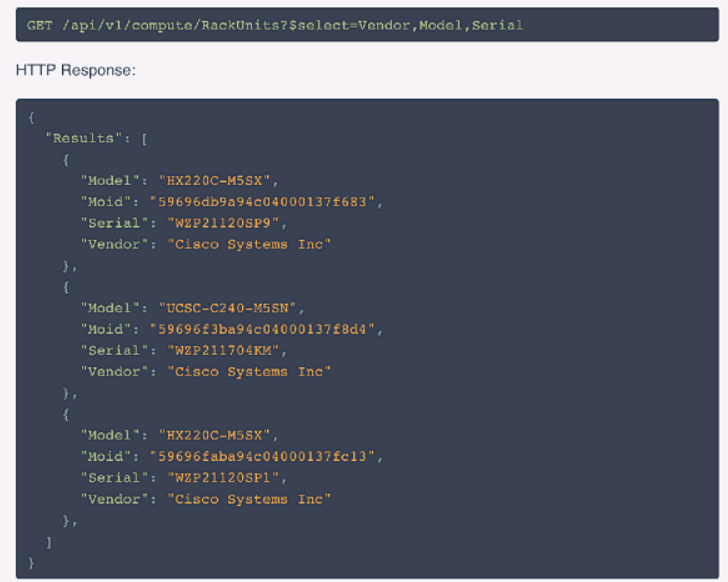
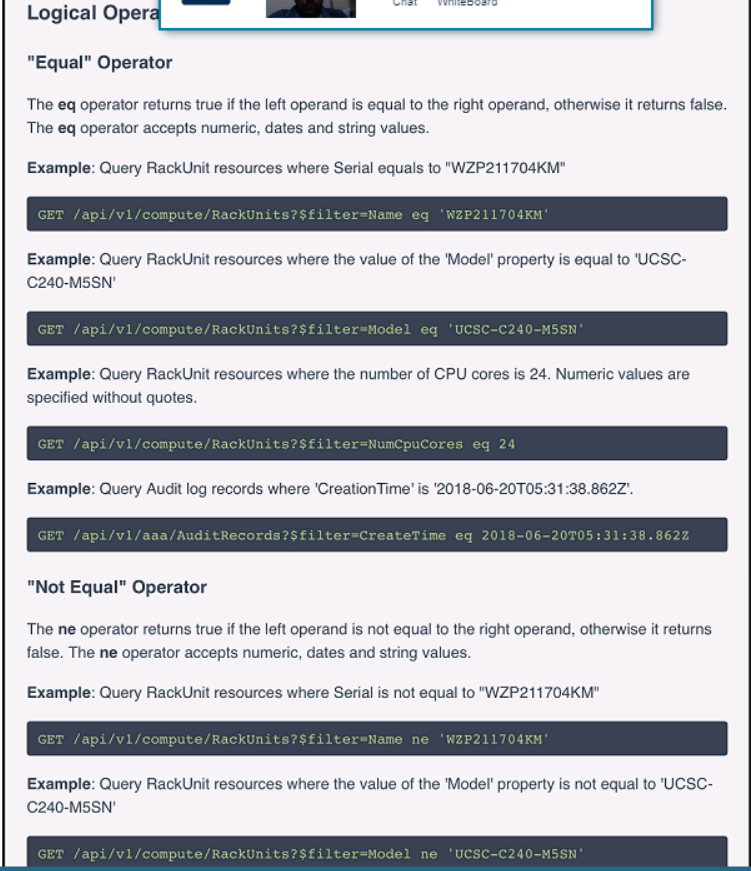
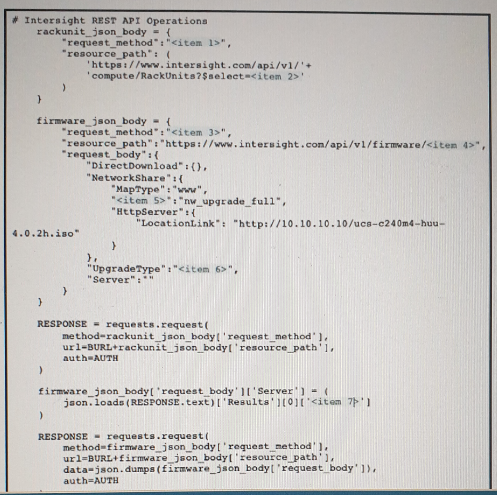
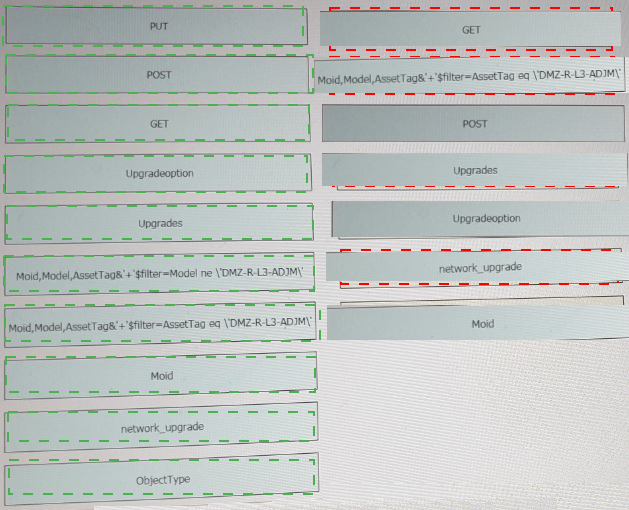
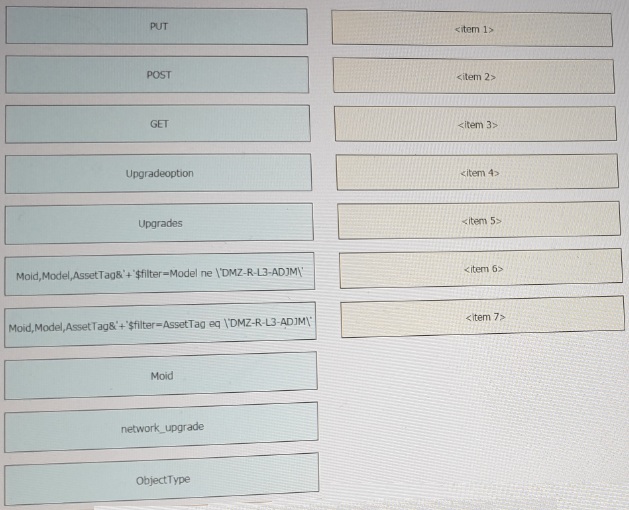
Refer to the exhibit above and click on the resource tabs in the top left corner to view resources to help with this question. The script uses the Cisco Intersight REST API. Drag and drop the code snippets from the left onto the item numbers on the right to match the missing sections in the Python script to update the firmware on specific Cisco Intersight USC rack server.DMZ_R-L3-ADJM. Not all code snippets are used.
An application has been developed for monitoring rooms in Cisco Webex. An engineer uses the application to
retrieve all the messages from a Cisco Webex room, but the results are slowly presented. Which action
optimizes calls to retrieve the messages from the /v1/messages endpoint?
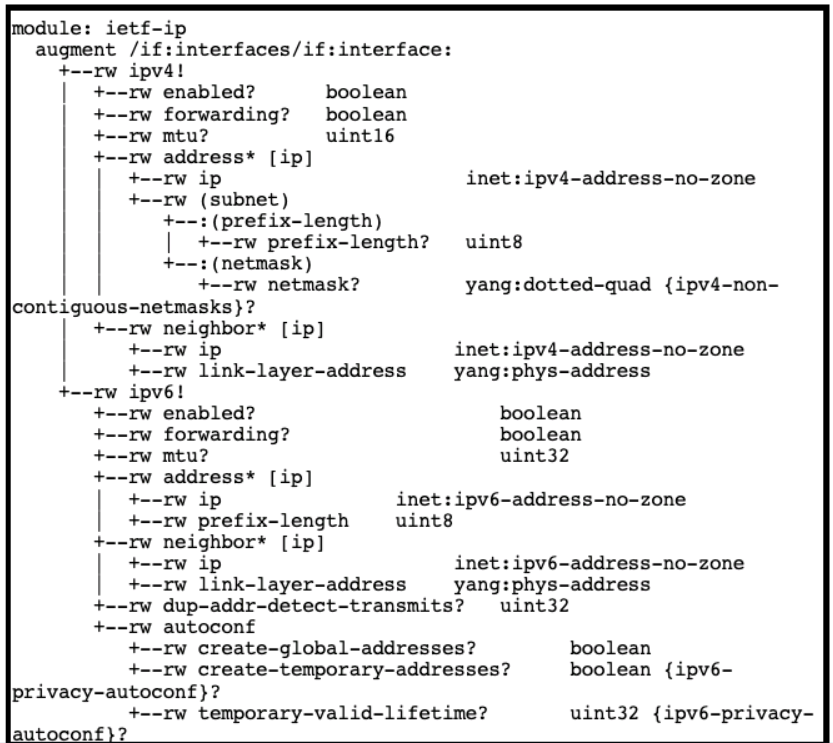
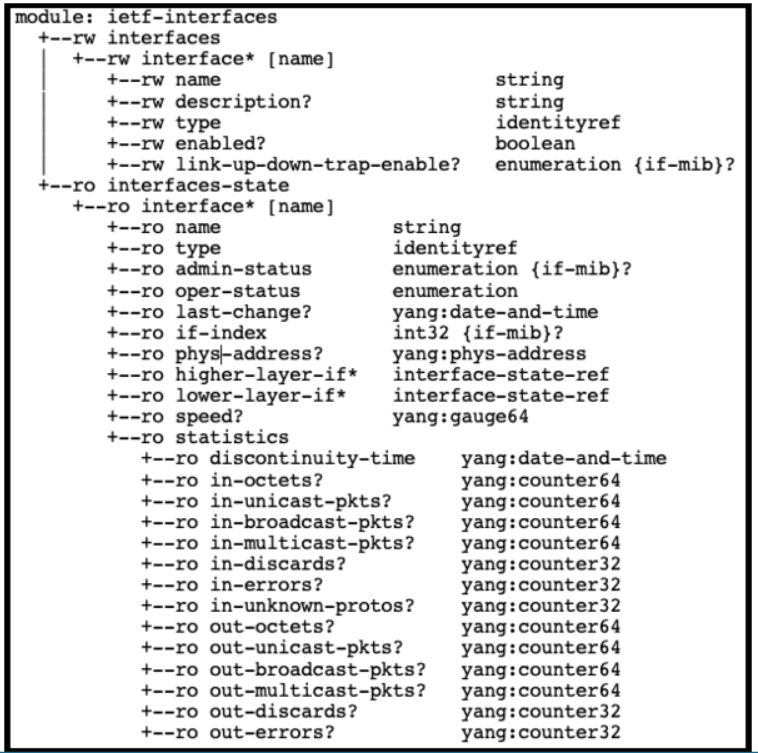
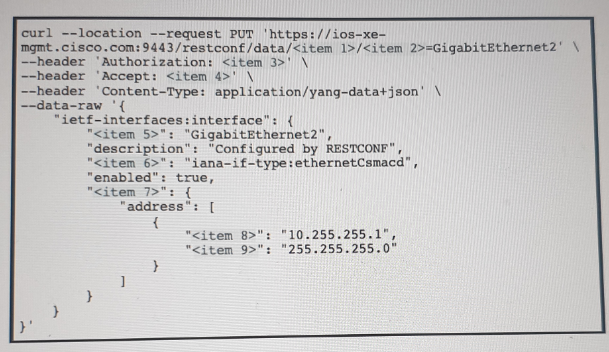
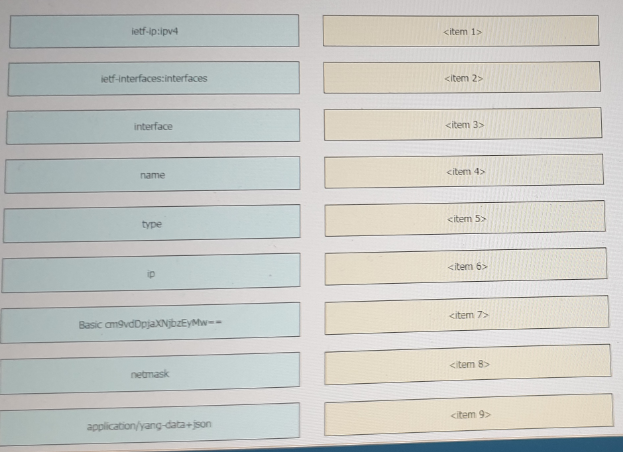
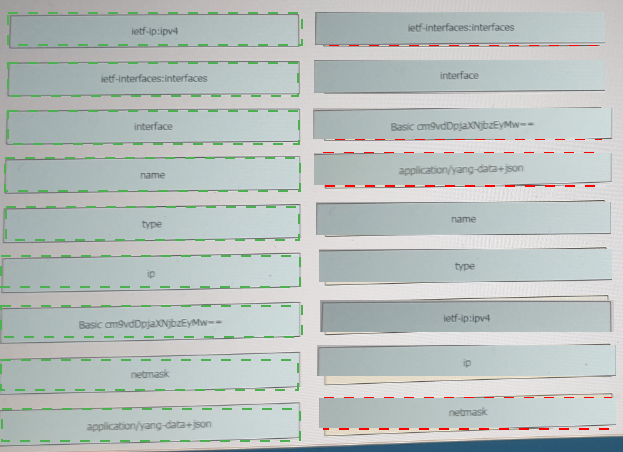
Refer to the exhibit above and click on the resource tabs in the top left corner to view resources to help with this question. Drag and drop the correct code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to complete the cURL script that will use RESTCONF to update an interface on a CISCO IOS XE device.