Cisco 350-901 - Developing Applications using Cisco Core Platforms and APIs (DEVCOR)
How is AppDynamics used to instrument an application?
A network operations team is using the cloud to automate some of their managed customer and branch locations. They require that all of their tooling be ephemeral by design and that the entire automation environment can be recreated without manual commands. Automation code and configuration state will be stored in git for change control and versioning. The engineering high-level plan is to use VMs in a cloud- provider environment then configure open source tooling onto these VMs to poll, test, and configure the remote devices, as well as deploy the tooling itself.
Which configuration management and/or automation tooling is needed for this solution?

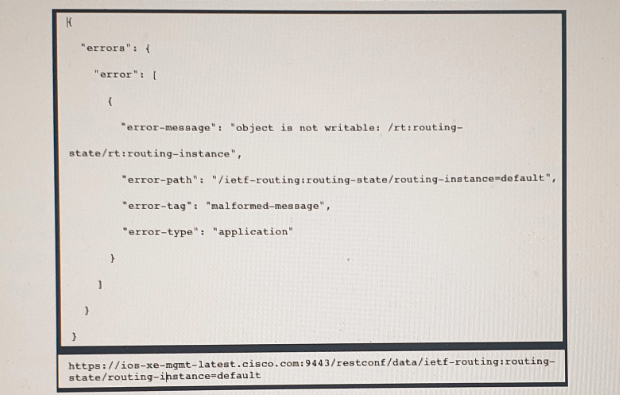
Refer to the exhibit above and click on the IETF Routing tab in the top left corner to help with this question. A developer is trying to update the routing instance by adding a new route to the routes list using the URL in the exhibit. What action must be taken to fix the error being received?
Which type of file is created from issued intermediate, root, and primary certificates for SSL installation on a server?
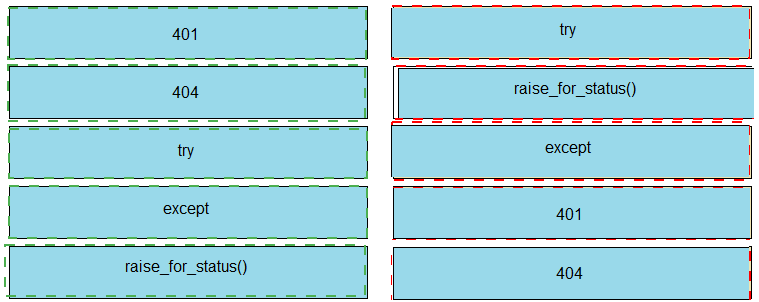
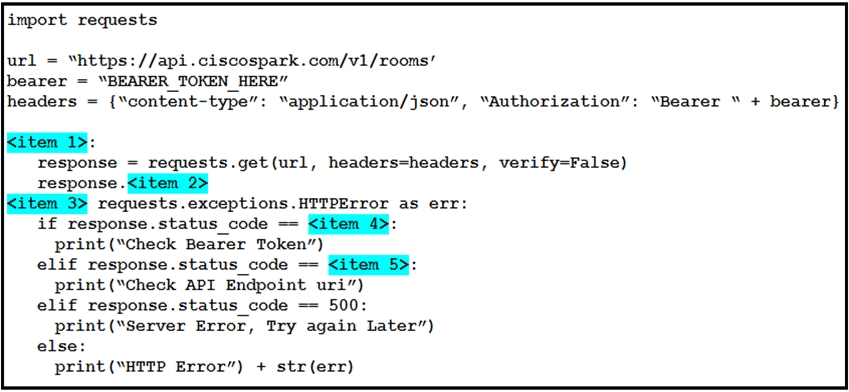
A developer is creating a Python script to use the Webex Teams REST API to list joined spaces, and gracefully handle and print the errors it receives. Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to complete the script.
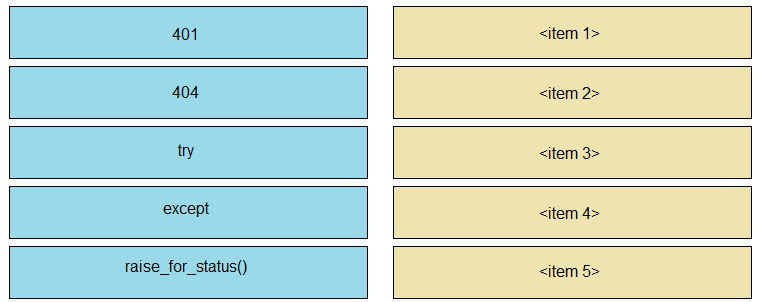
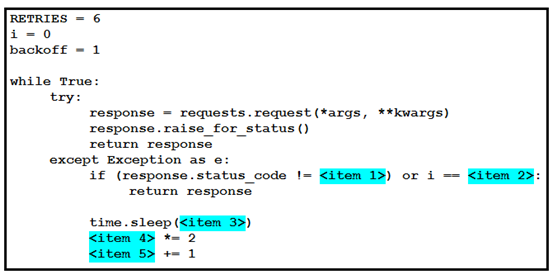
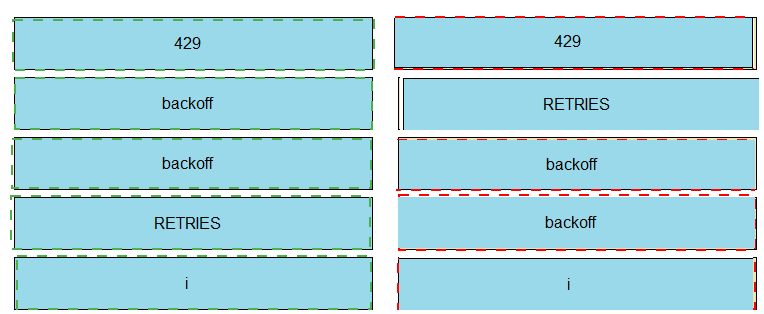
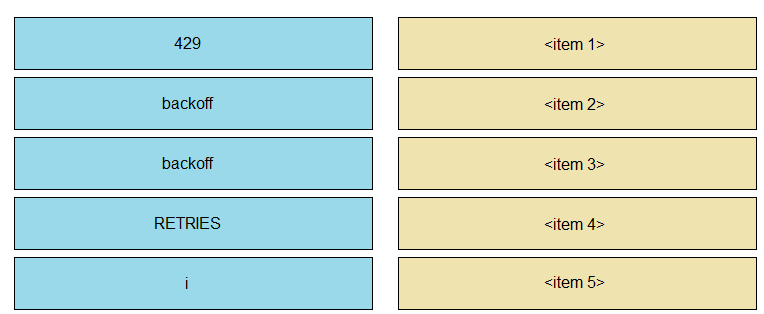
Refer to the exhibit. The self-service Webex Teams bot is failing when many users attempt to interact with it at the same time. Drag and drop the code snippets from the left onto the correct item numbers on the right that match the missing sections in the exhibit to complete this code to handle this high-load situation.
How is an OAulh2 three-legged authentication flow initiated?
Refer to the exhibit.
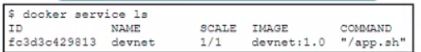
Refer to the exhibit A Docker swarm service is currently running m a local data center The service is hosting an HTML website it the container fads then the service becomes unavailable The design must meet these requirements
• The service must be highly available and resilient against a data center outage.
• The service must be accessible from a single URL
• The HTTP session must remain on the server from which the original request was sent
• Failure of the server must force the client to reconnect
Which two design approaches must be used to meet the requirements? (Choose two.)
An application uses OAuth to get access to several API resources on behalf of an end user. What are two valid parameters to send to the authorization server as part of the first step of an authorization code grant flow? (Choose two.)
Users report that they are no longer able to process transactions with the online ordering application, and the logging dashboard is
displaying these messages:
Fri Jan 10 19:37:31.123 ESI 2020 [FRONTEND] [NFO: Incoming request to add item to cart from user 45834534858
Fri Jan 10 19:37:31.247 EST 2020 [BACKEND] INFO: Attempting to add item to cart
Fri Jan 10 19:37:31.250 EST 2020 [BACKEND] ERROR: Failed to add item: MYSQLDB ERROR: Connection refused
What is causing the problem seen in these log messages?