Cisco 350-901 - Developing Applications using Cisco Core Platforms and APIs (DEVCOR)
An application must be able to print the values of the variables in specific modules. Different message levels will be used for production and for development. Proof of access and activity must be documented. What must be included in the implementation to support these observability requirements?
A Cisco Catalyst 9000 switch has guest shell enabled. Which Linux command installs a third-party application?
Refer to the exhibit.
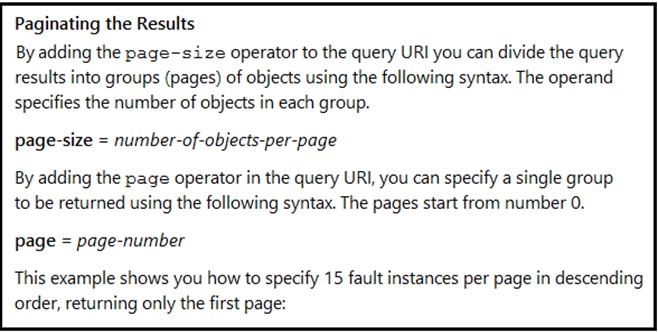
Many faults have occurred in the ACI environment and a sample of them needs to be examined. Which API call retrieves faults 30 through 45?
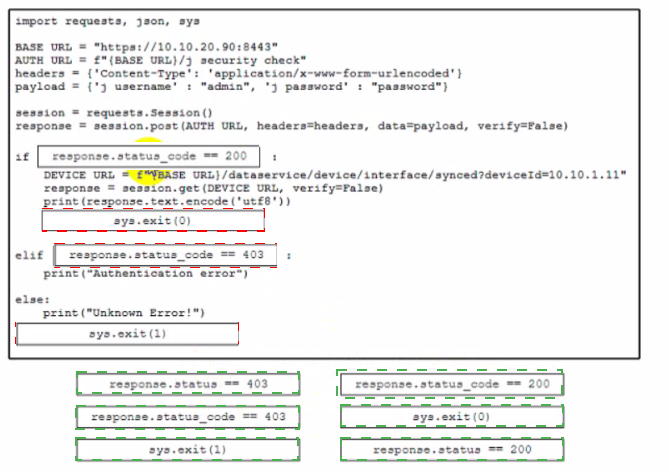
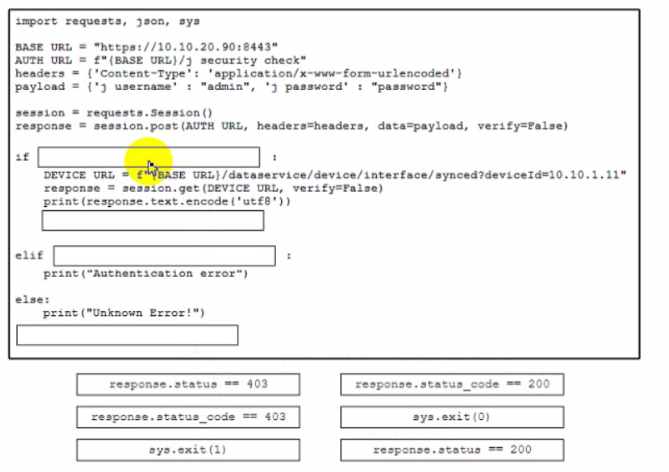
Refer to the exhibit.
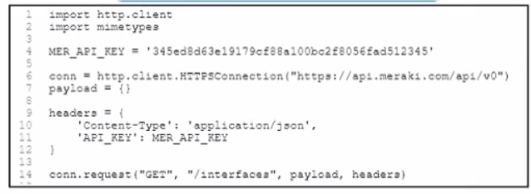
A developer created a Python script to retrieve information about Meraki devices in a local network deployment After requesting a security review of the code the security analyst has observed poor secret storage practices What is the appropriate secret storage approach''
A developer is creating a Python script to analyze errors during REST API call operations. The script will be used with Cisco solution and devices. Drag and drop the code from the bottom to the box where the code is missing to implement control flow for handling unrecoverable REST API calls. Not all options are used.
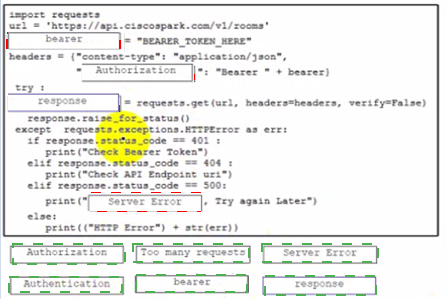
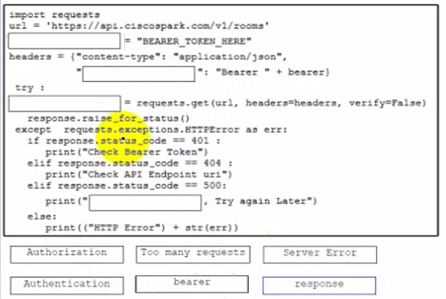
A developer is creating a Python script to use the Webex REST API to list joined spaces and handle and print the errors it receives. Drag and drop the code from the bottom of the code snippet onto the blanks in the code to complete the script. Not all options are used.
What is the unique identifier in the 0Auth2 three-legged authorization code flow?
Which two gRPC modes of model-driven telemetry are supported on Cisco IOS XE Software? (Choose two.)