Cisco 350-901 - Developing Applications using Cisco Core Platforms and APIs (DEVCOR)
A developer is working on a new feature in a branch named 'newfeay000222118' and the current working primary branch is named 'pnm409024967' The developer requires a merge commit during a fast forward merge for record-keeping purposes. Which Git command must Be used?
A)

B)

C)

D)

What securely stores and encrypts the API keys and tokens that are used for an application deployment?
Refer to the exhibit.
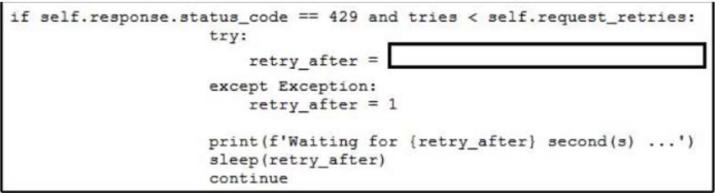
Which line of code needs to be placed on the snippet where the code is missing to provide APl rate-limiting to the requests?
What is a benefit of running multiple instances of a back-end service and using load balancing to distribute the communication between the front-end and back-end services?
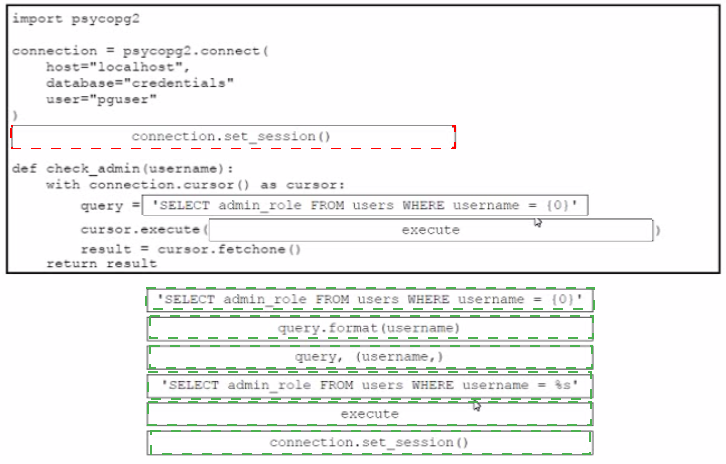
Drag and drop the code from the bottom onto the box where the code is missing in the Python code to query for user permissions while mitigating against SQL Injection Not all options are used.
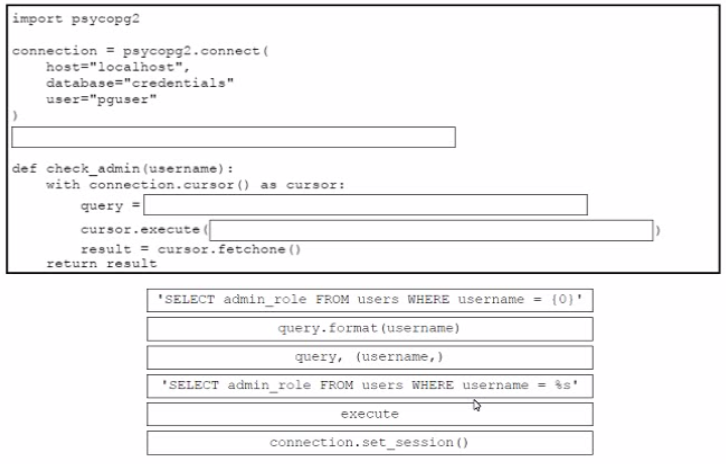
Refer to the exhibit.
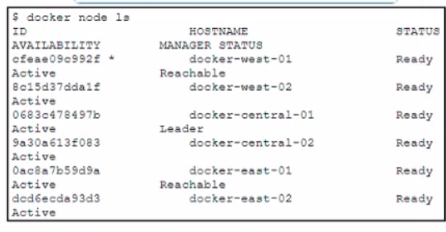
A Docker swarm cluster is configured to load balance services across data centers in three different geographical regions west central and east. The cluster has three manager nodes and three worker nodes Anew service named cisco.devnet is being deployed. The service has these design requirements
• All containers must be hosted only on nodes in the central region
• The service must run only on nodes that are ineligible for the manager role
Which approach fulfills the requirements?
A developer has just completed the configuration of an API that connects sensitive internal systems. Based on company policies, the security of the data is a high priority.
Which approach must be taken to secure API keys and passwords?
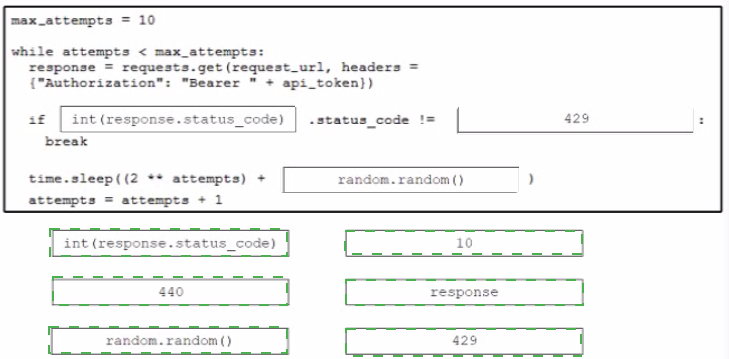
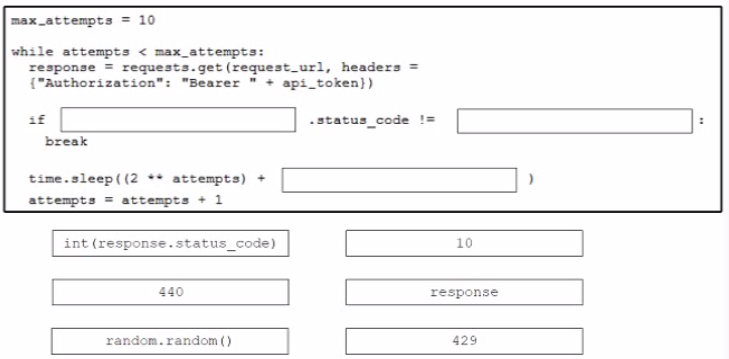
Drag and drop the code from the bottom onto the box where the code is missing to stop the REST API requests if a 'Too Many Requests" response is received Not all options are used.
An architect must optimize traffic that targets a popular API endpoint Currently, the application downloads a large file hourly, but often the file is unchanged and the download causes unnecessary load and delays Which cURL command must be used to determine the last modified date of the file and to optimize the API usage?
Refer to the exhibit.
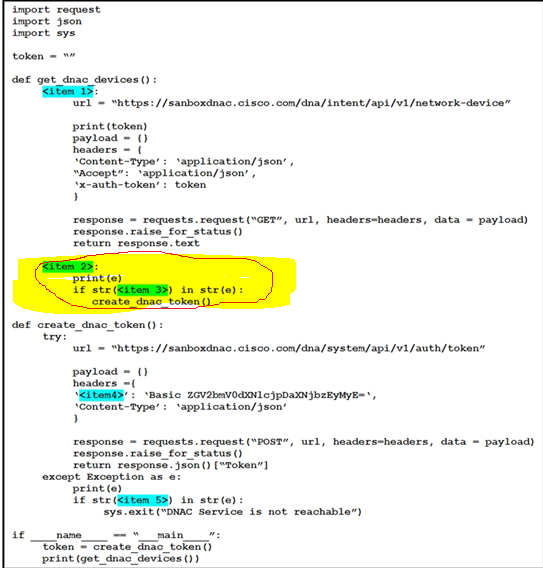
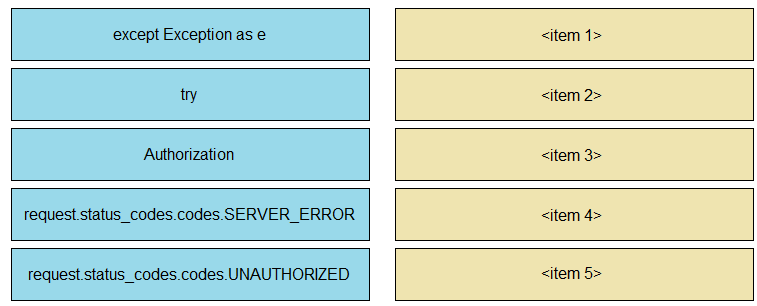
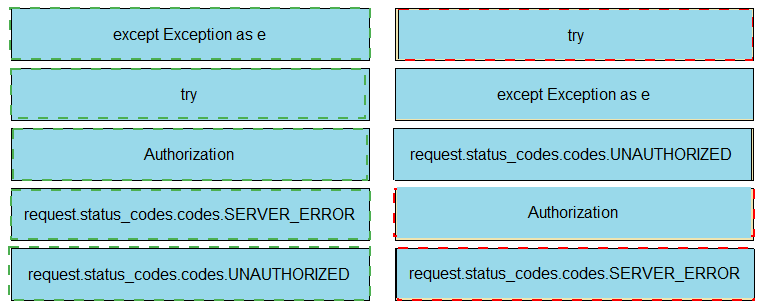
Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to complete the script to implement control flow.