Cisco 352-011 - Cisco Certified Design Expert Practical Exam
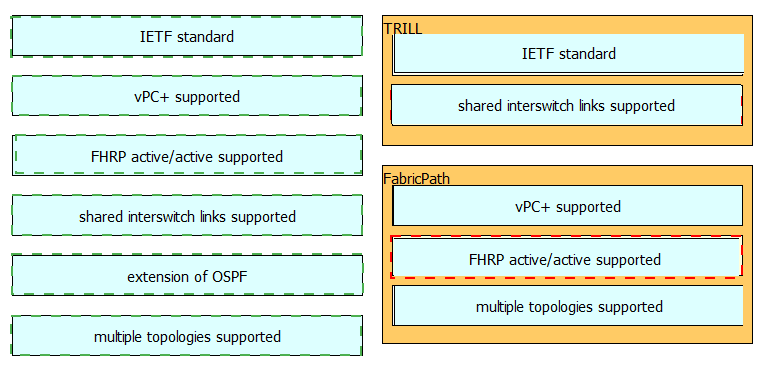
Drag and drop the technology details or features support on the left into the corresponding Layer 2 multipath technologies on the right. Not all options will be used.
A Company has these requirements for access to their wireless and wired corporate LANs using 802.1x
ï‚· Clients devices that corporate assets and have joined the active directory domain are allowed access
ï‚· Personal devices must be not allowed access
ï‚· Clients and access servers must be mutually authenticated.
Which solution meets these requirements?
Which option is a design consideration when using routers in a distributed hardware architecture?
Refer to the Exhibit.
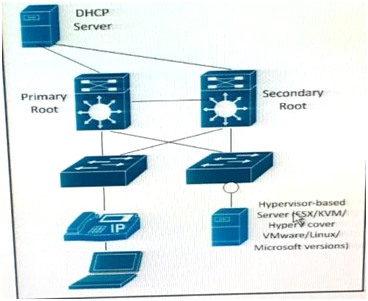
The server is running multiple VLANs on its NIC. Which two Layer 2 features should be applied to the network location identified by a circle? (Choose two)
An enterprise customer A with provider-independent address space is dual-homed to two ISP. Which two options , when combined, allow for customer A to efficiently achieve out-bond traffic load-balancing? ( Choose two)
The cloud service provider CSP is planning to launch five data centers in Egypt, United Arab Emirates, Saudi Arabia, Qatar and Turkey. CSP is looking for VLAN extension and DCIs between these five data centers to allow for software replication, where original and backup VMs must be on the same subnet. Which tunneling technology must they use?
A retail company connects its 250 branches across the globe to the core using MPLS Layer 3 VPN. The company is planning to migrate its traditional telephony services to VoIp, in order to reduce the cost of international calls. What are the two primary concerns when implementing this migration? (Choose two)
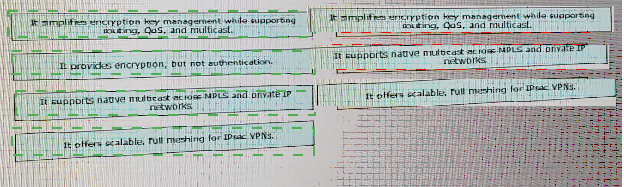
Drag and drop the design characteristics of GET VPN from the left to the right. Not all options are used.

A service provider is designing a new backbone based on an IGP and MPLS what are two valid reasons for implementing MPLS-TE as well? (Choose two)
Refer to the exhibit.
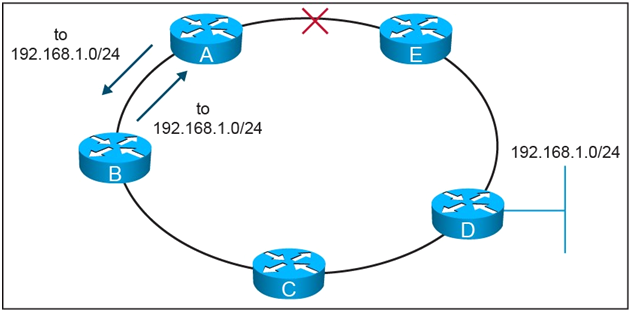
On this MPLS-based network ring, links have failed between router A and router E. These failures formed microloops while the network converged, when A forwarded traffic to B but B forwards it back to A. Which technology is the simplest solution to avoid microloops without enabling a new protocol in the network?