VMware 3V0-752 - VMware Certified Advanced Professional 7 - Desktop and Mobility Design Exam
An architect is working on a physical desktop replacement using Horizon View.
The architect gathered this information from the customer:
There are currently 500 physical desktops, all with traditional spinning hard drives.
Each desktop peaks at 75 IOPS multiple times during the day.
The average read/write ratio is 30% reads, 70% writes.
The architect decided to size the vSAN cluster to handle the workload using FTT=1 and Fault Tolerance Method of RAID-1.
Using only the information provided, what are the total calculated IOPS required for the vSAN cluster?
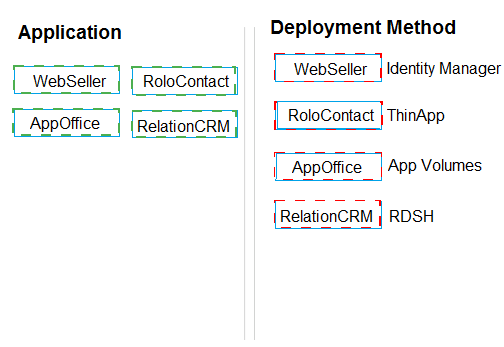
A company has several applications that are being moved to a Horizon environment. An architect has been given several application types and is designing an environment to accommodate all of the applications.
List of applications:
WebSeller – a cloud-based application that is single sign-on capable.
RoloContact – a Windows application that utilizes an Internet Explorer 6 and an IE plugin, but needs to be deployed to Windows 8 desktops.
AppOffice – a group of Windows based application that needs to be deployed together to an existing View linked clone desktop pool for the remote sales team.
RelationCRM – a server-based application that is currently accessed via RDP.
Match each application with its appropriate deployment method.
An architect for Company A is working on implementing a VMware Horizon solution.
Company A will be acquiring Company B in the coming months.
Company B has an existing Active Directory structure and there are NO plans to move those users over to Company A’s Active Directory structure
However, users from Company B need to be able to use VDI desktops running in Company A.
Which step could the architect take to meet requirements?
A company’s IT team wants to provide multiple Microsoft Office suite applications to end users without incurring any Windows desktop operating system licensing fees.
They also want each end users’ Microsoft Office suite application customization settings and configuration changes preserved and restored when the end user logs off and logs back in.
Which two VMware technologies must they deploy to meet the requirements? (Choose two.)
The IT team for a regional healthcare company wants to provide several applications to iOS and Android tablets and smartphones as well as Mac and Windows laptops using VMware products. It wants to minimize Windows desktop operating system licensing and support costs.
Which meets the requirements?
The finance group in a company has asked for a new application to be made available to all of the members of the finance department. The application is currently installed on all the finance desktops, but will be moving to a cloud-hosted model.
What solution should the IT administrator use to manage access to the new application?
An application packaging team is preparing to deploy a new enterprise application for 1000 users.
Application requirements and limitations include:
Windows 2012 R2 or Windows 10 64-bit OS
Installation of a PDF printer
Application only allows a single instance to be launched
1 GB RAM
The organization is only using Horizon hosted applications on Windows 2012 R2. The servers are at 30% utilization. No additional users will be added.
What changes to the Horizon environment will be required to deploy the application?
A company wants to deploy Windows 8 Horizon desktops for end users with the following goals:
Fast provisioning
Fast guest customization
Minimum storage space
No user profiles on the C: drive
What must be implemented to meet these requirements?
The IT team at a small government organization wants to deploy Windows RDS desktops to their end users. They want the end users’ profile and application customization setting preserved. They also want to deploy applications using VMware App Volumes.
What should be implemented to meet requirements?
A customer wants to securely deliver applications. They have given these requirements to an architect:
1,100 corporate users
Applications run on Windows
Confidential data must remain inside the datacenter at all times
Datacenter has a firewall separating it off from the corporate LAN
Security team policy will NOT allow a corporate LAN subnet through the firewall to a datacenter subnet (example: source 172.16.30.0 /24, destination 10.10.1.0 /24 would NOT be allowed)
Security team policy does allow corporate LAN subnets to access specific datacenter IP addresses (example: source 172.16.30.0 /24, destination 10.10.1.100 /24 would be allowed)
50 of the 1,100 internal users work exclusively on tablets, some Android and some IOS devices
Which two recommendations can the architect propose? (Choose two.)