ECCouncil 412-79v10 - EC-Council Certified Security Analyst (ECSA) V10
Which type of vulnerability assessment tool provides security to the IT system by testing for vulnerabilities in the applications and operation system?
Traffic on which port is unusual for both the TCP and UDP ports?
Which of the following defines the details of services to be provided for the client’s organization and the list of services required for performing the test in the organization?
What is a difference between host-based intrusion detection systems (HIDS) and network-based intrusion detection systems (NIDS)?
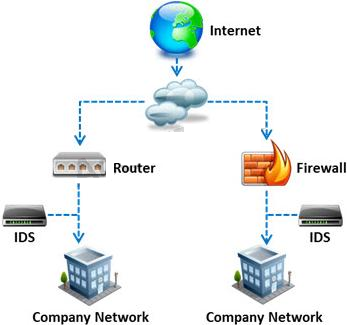
In which of the following IDS evasion techniques does IDS reject the packets that an end system accepts?
In the process of hacking a web application, attackers manipulate the HTTP requests to subvert the application authorization schemes by modifying input fields that relate to the user ID, username, access group, cost, file names, file identifiers, etc.
They first access the web application using a low privileged account and then escalate privileges to access protected resources. What attack has been carried out?
Tyler is setting up a wireless network for his business that he runs out of his home. He has followed all the directions from the ISP as well as the wireless router manual. He does not have any encryption set and the SSID is being broadcast.
On his laptop, he can pick up the wireless signal for short periods of time, but then the connection drops and the signal goes away. Eventually the wireless signal shows back up, but drops intermittently.
What could be Tyler issue with his home wireless network?
Paulette works for an IT security consulting company that is currently performing an audit for the firm ACE Unlimited. Paulette's duties include logging on to all the company's network equipment to ensure IOS versions are up-to-date and all the other security settings are as stringent as possible.
Paulette presents the following screenshot to her boss so he can inform the clients about necessary changes need to be made. From the screenshot, what changes should the client company make?
Exhibit:

What are the 6 core concepts in IT security?
A chipset is a group of integrated circuits that are designed to work together and are usually marketed as a single product.†It is generally the motherboard chips or the chips used on the expansion card.
Which one of the following is well supported in most wireless applications?



