ECCouncil 412-79v10 - EC-Council Certified Security Analyst (ECSA) V10
What does ICMP Type 3/Code 13 mean?
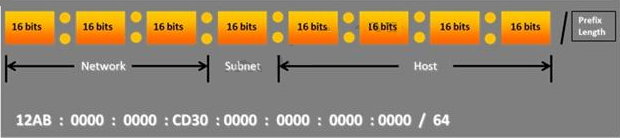
Choose the correct option to define the Prefix Length.
Meyer Electronics Systems just recently had a number of laptops stolen out of their office. On these laptops contained sensitive corporate information regarding patents and company strategies.
A month after the laptops were stolen, a competing company was found to have just developed products that almost exactly duplicated products that Meyer produces.
What could have prevented this information from being stolen from the laptops?
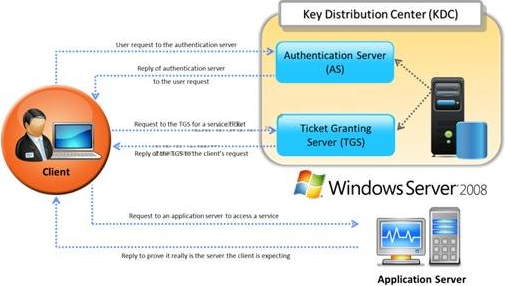
Identify the type of authentication mechanism represented below:
Harold wants to set up a firewall on his network but is not sure which one would be the most appropriate. He knows he needs to allow FTP traffic to one of the servers on his network, but he wants to only allow FTP-PUT.
Which firewall would be most appropriate for Harold?
What is kept in the following directory? HKLM\SECURITY\Policy\Secrets
The objective of this act was to protect consumers personal financial information held by financial institutions and their service providers.
Which one of the following is a useful formatting token that takes an int * as an argument, and writes the number of bytes already written, to that location?
Which of the following reports provides a summary of the complete pen testing process, its outcomes, and recommendations?
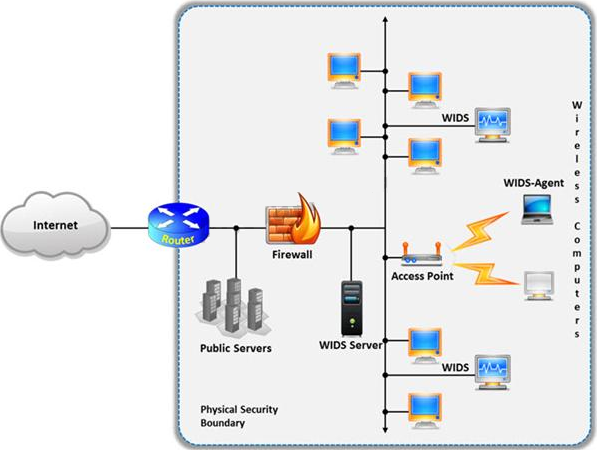
A wireless intrusion detection system (WIDS) monitors the radio spectrum for the presence of unauthorized, rogue access points and the use of wireless attack tools.
The system monitors the radio spectrum used by wireless LANs, and immediately alerts a systems administrator whenever a rogue access point is detected. Conventionally it is achieved by comparing the MAC address of the participating wireless devices.
Which of the following attacks can be detected with the help of wireless intrusion detection system (WIDS)?